Question
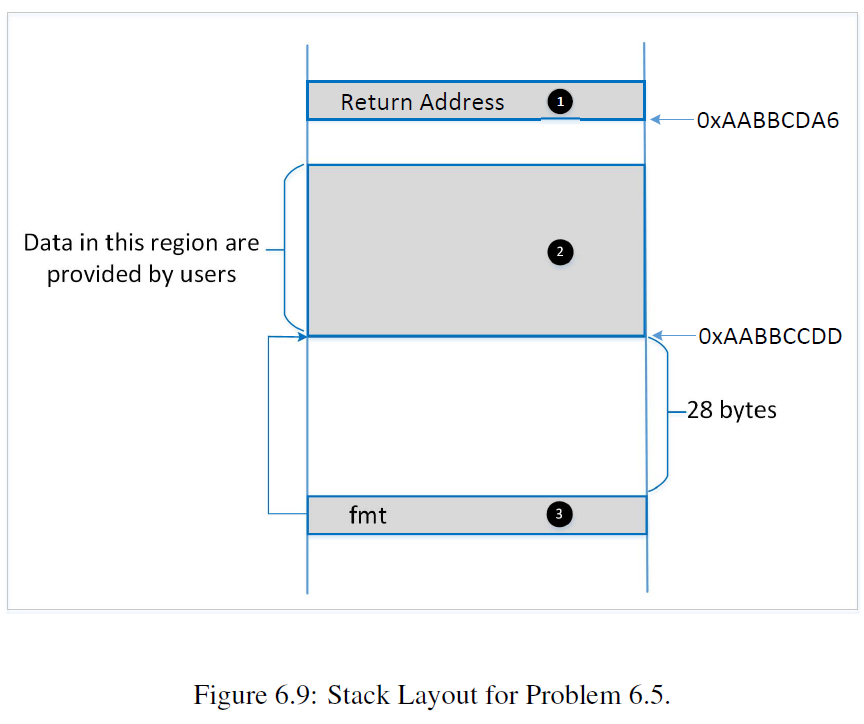
A server program takes an input from a remote user, saves the input in a buffer allocated on the stack (Region in Figure 6.9). The
A server program takes an input from a remote user, saves the input in a buffer allocated on the stack (Region in Figure 6.9). The address of this buffer is then stored in the local variable fmt, which is used in the following statement in the server program: printf(fmt); When the above statement is executed, the current stack layout is depicted in Figure 6.9. If you are a malicious attacker, can you construct the input, so when the input is fed into the server program, you can get the server program to execute your code? Please write down the actual content of the input (you do not need to provide the exact content of the code; just put malicious code in your answer, but you need to put it in the correct location).
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


