Question
AAB (a fictitious company) is an HK mobile network operator and internet service provider. The company is looking to become one of the largest mobile
AAB (a fictitious company) is an HK mobile network operator and internet service provider. The company is looking to become one of the largest mobile network operators in HK, with approximately two million subscribers as of November 2020. Its main office and data centre is located in London. The company recently opened a new site and data center in China in May 2021. AAB launched a new on-demand TV service for broadband customers in March 2021. The service is provided on an internet-connected TV box or through an app on selected computers, mobile devices, and Smart TVs. Subscribers to the new TV service will need to create an online account using an email address and password, first and last names, addresses, and credit card details. Subscribers are then able to manage their online accounts and make payments to renew their subscriptions through the companys e-commerce website and mobile app. All digital copies of popular shows and movies streamed by subscribers are stored on multiple servers at both data centers. In May 2021, the company suffered a major fire incident that caused physical damage to the data centre and destroyed a Network Attached Storage (NAS) device used to back up sensitive company documents and files. To allow staff at the different company sites to easily share company files, documents and backups following this incident, the network administrator decided to set up a temporary internal file server that is accessible to all employees. Since the start of the pandemic in 2019, some employees at AAB who work off-site can access their workstations remotely from home. Most of the employees are happy with the flexibility of being able to work from home or from anywhere with access to the public internet such as cafes, airport lounges or restaurants. Recently, the company received a fine of HKD40,000 after several emails, which contained details of several customers personal information and account details, were sent to the wrong customers. An investigation into the incident revealed that an employee selected the wrong email addresses during the creation of an email distribution list. The data itself was not encrypted and thus was able to be viewed by unintended recipients.
Network Overview The HK and CHINA sites are all interconnected using Cisco RV340 Series routers to ensure that all employees have access to the network resources that they need to be productive. Remote employees have a Remote Desktop Protocol (RDP) client application installed on their computers which they use to remotely access the companys internal network.
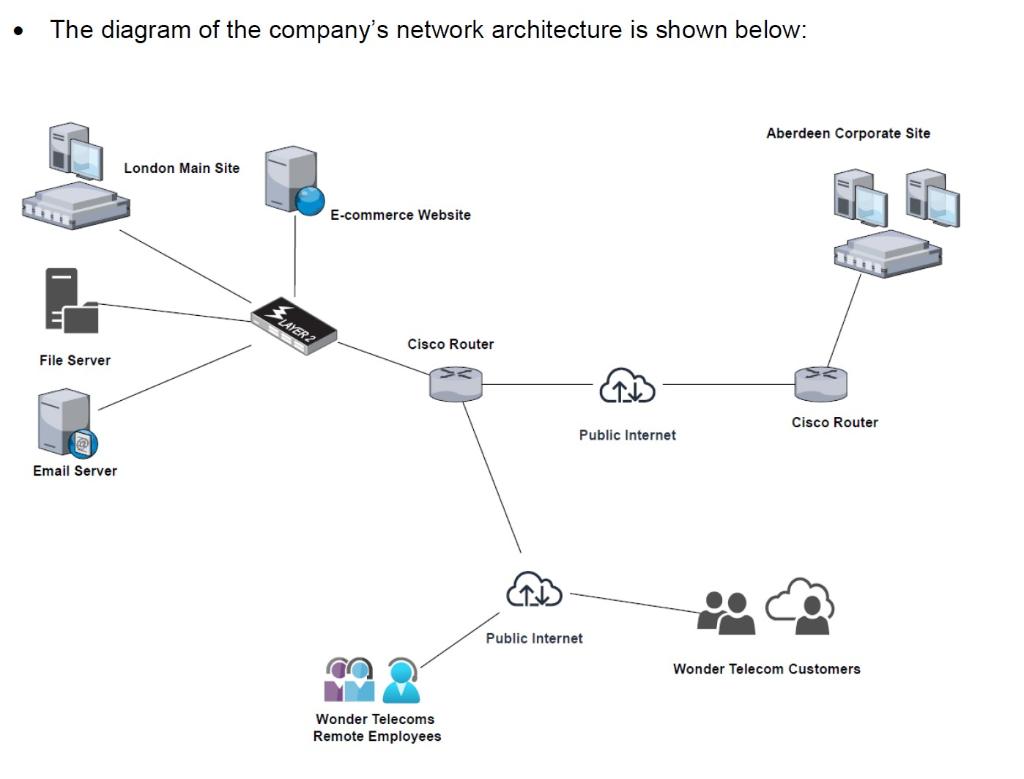
HK Site Network: The companys main e-commerce website used by its customers to manage their TV subscriptions has the following setup as shown below: Apache HTTP Server 2.4.50 Magento Commerce version 2.4.2 Oracle GlassFish Server Open-Source Edition 4.1 MariaDB version 10.2 The internal file server (hosted at the London site) is configured to use File Transfer Protocol (FTP) and allows employees to log in using a shared username: FTP user and password: @W0nd3rFul567 The diagram of the companys network architecture is shown below:
Once you have identified the highest risks, you need to make recommendations on how to control those risks, i.e., what security you will put in place. a) Discuss each of the threats you have identified in Task 1b) and recommend security implementations to reduce the risks. For higher marks, consider including alternative countermeasures to mitigate the risks and provide clear justifications. When you use a technical term, you should explain it. 15 Marks b) Write a report based on the setup for the main e-commerce website. In your report you MUST: Provide detailed explanations about the vulnerabilities affecting the website. For extra marks, provide references to exploits, Common Vulnerabilities and Exposures (CVE) security advisory notes for each vulnerability. Describe details of security recommendations to fix the top THREE (3) vulnerabilities you have described in your report. Describe details of security recommendations to prevent staff from sending misdirected and insecure emails to customers in future.
The diagram of the company's network architecture is shown below
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


