Question: ACIS 4024 Cases 114% - Do Expo The audit team also confirmed that the Prophecy and FultiPro applications are configured such that users Buthenticate with
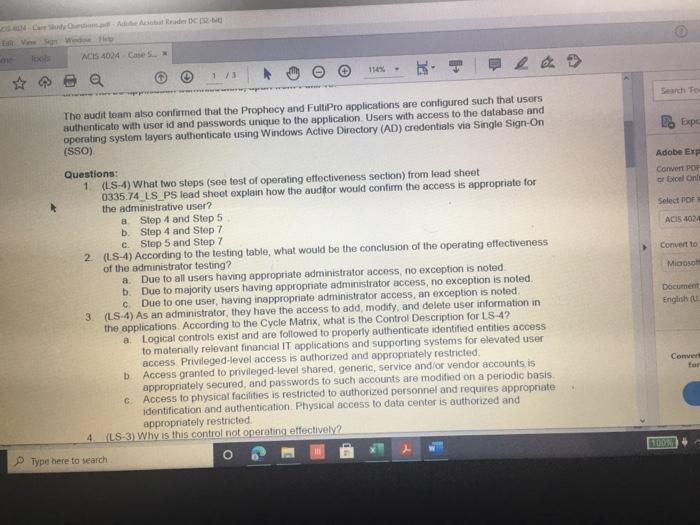
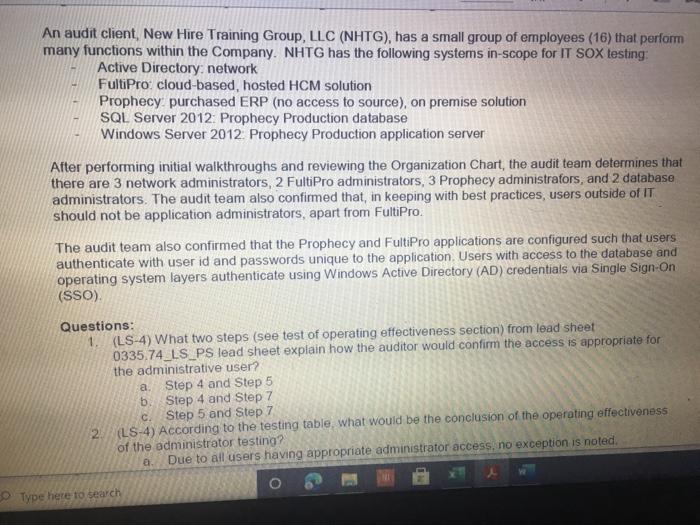
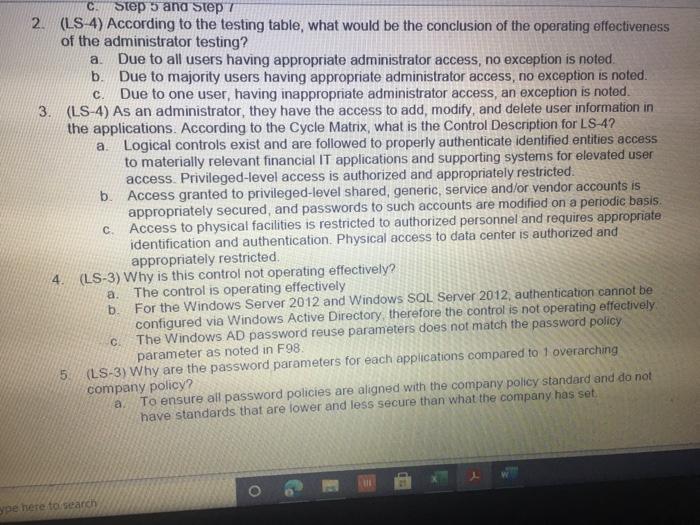
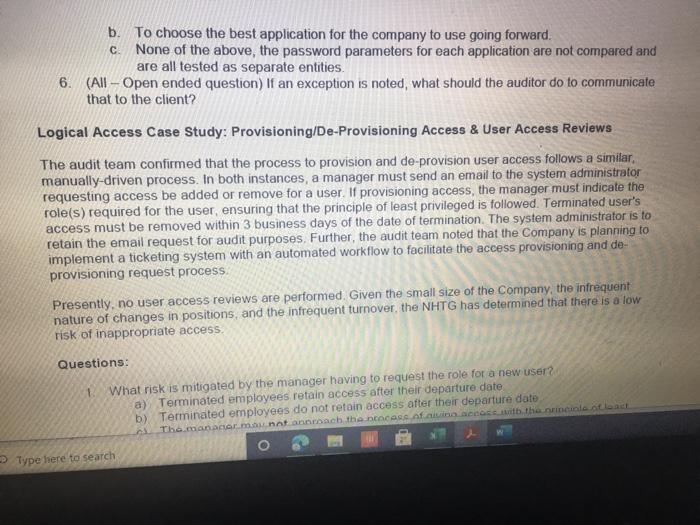
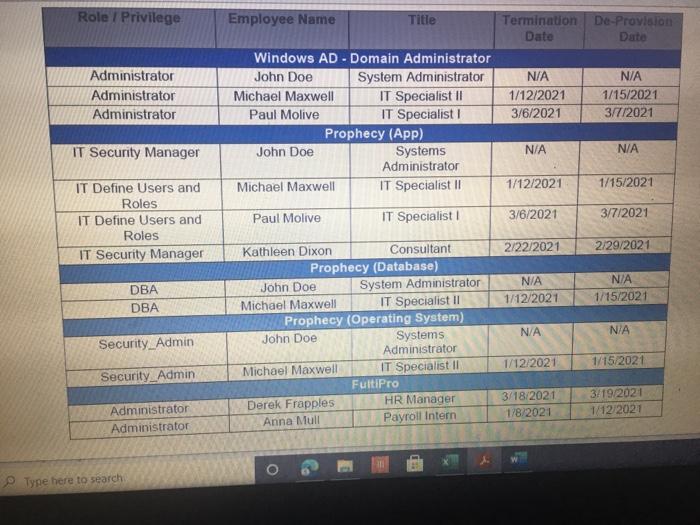
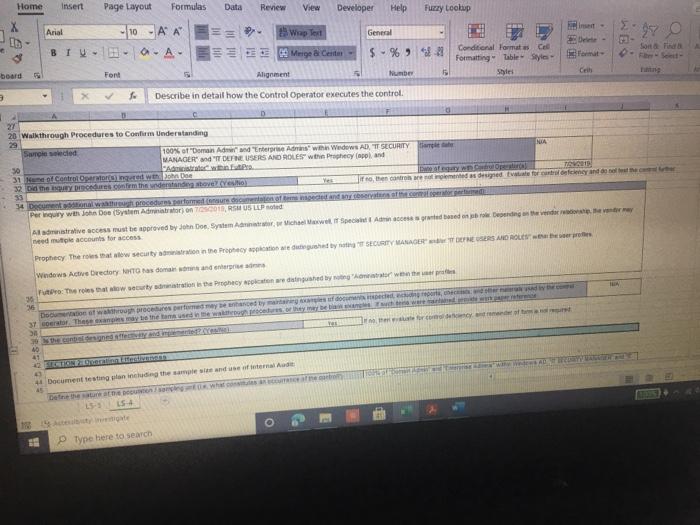
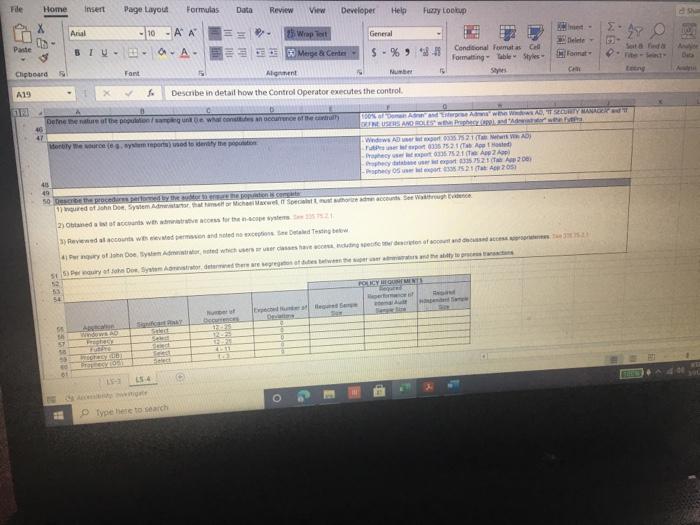
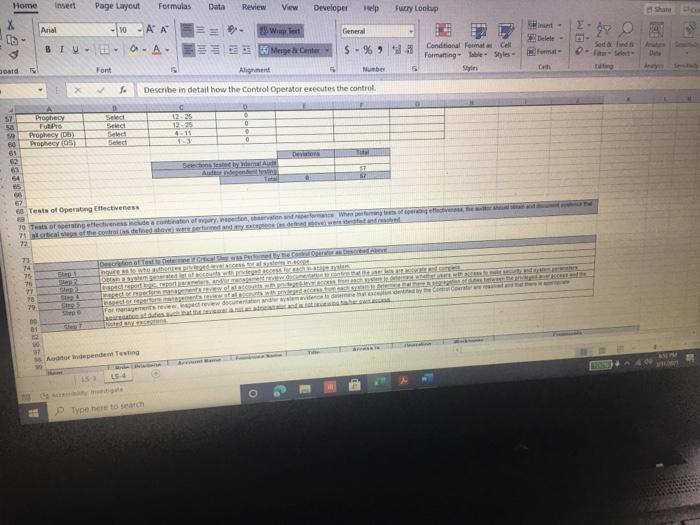
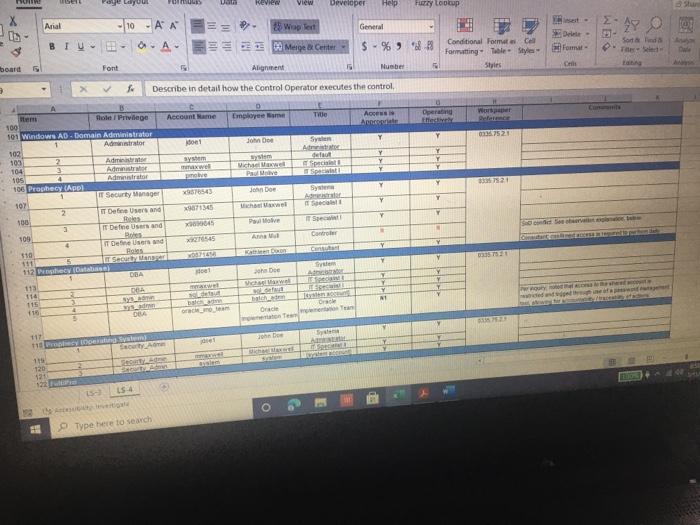
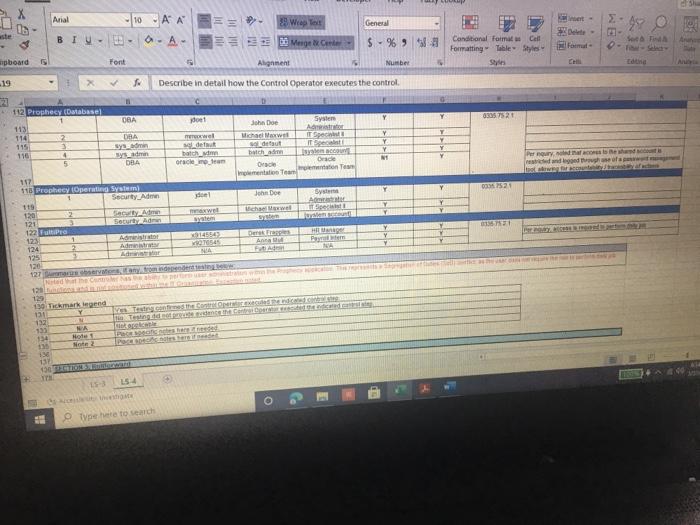
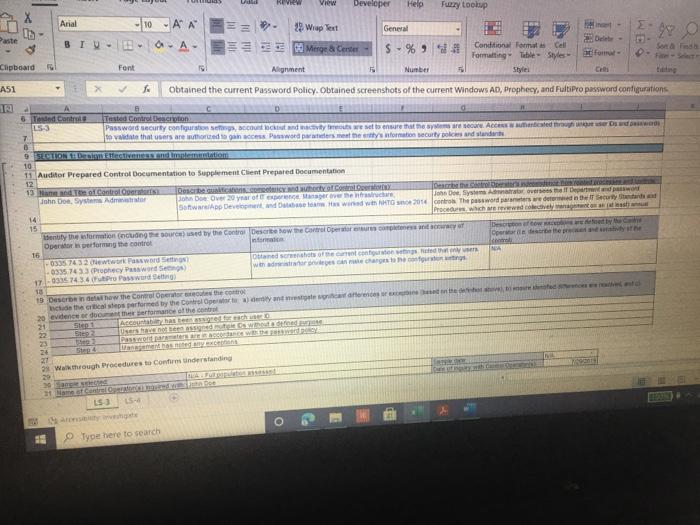
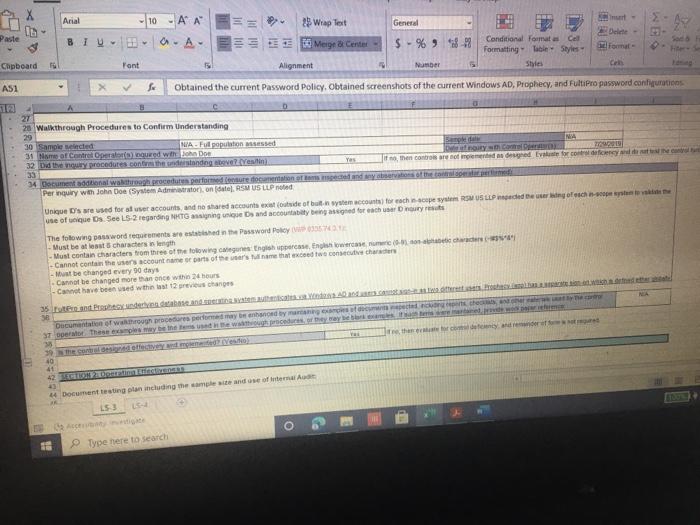
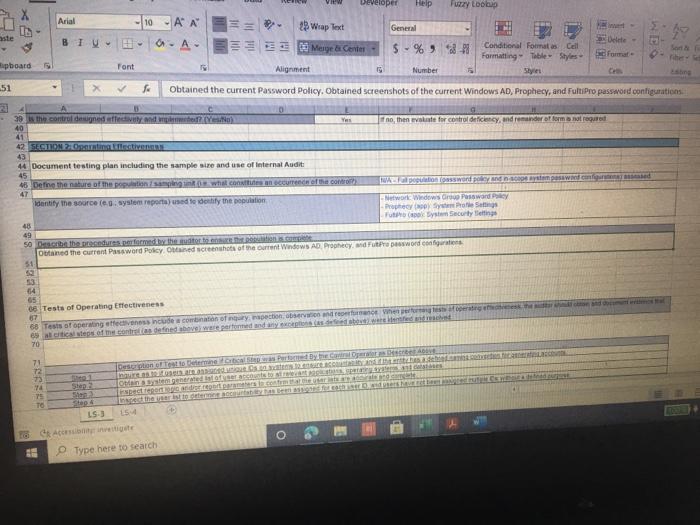
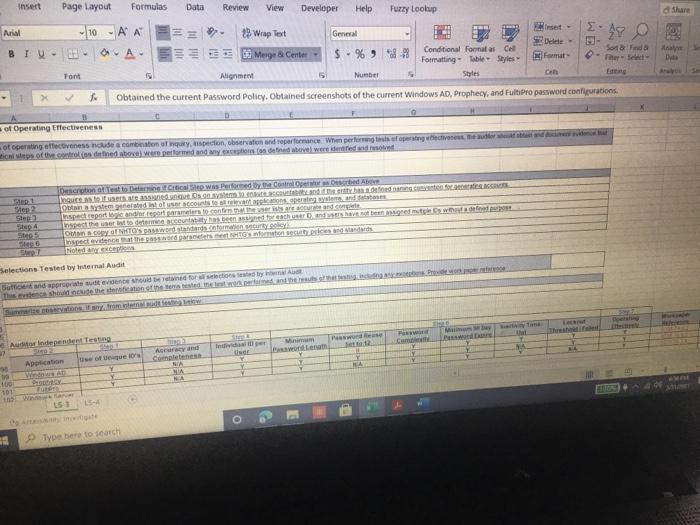
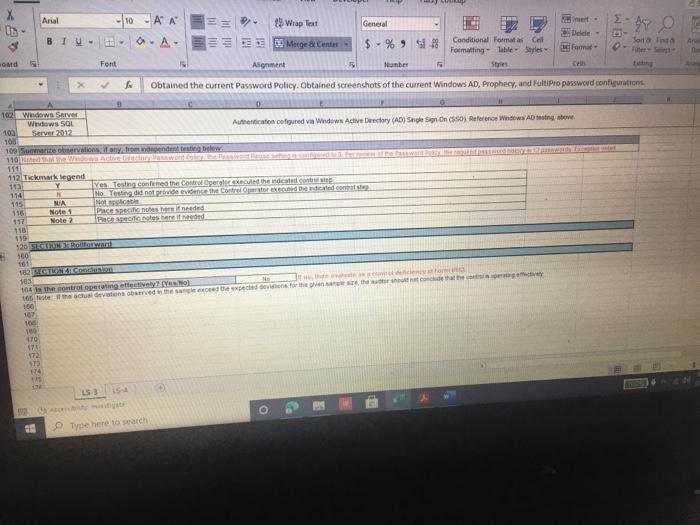
ACIS 4024 Cases 114% - Do Expo The audit team also confirmed that the Prophecy and FultiPro applications are configured such that users Buthenticate with user id and passwords unique to the application Users with access to the database and operating system layers authonticate using Windows Active Directory (AD) credentials via Single Sign-On (SSO) Adobe Exp Convert POHY of Excel One Select POF ACIS 4024 Convert to Micos Document English C Questions: 1 (LS-4) What two stops (see test of operating effectiveness section) from lead sheet 0335.74 LS_PS lead sheet explain how the auditor would confirm the access is appropriate for the administrative user? a Step 4 and Step 5 b. Step 4 and Step 7 c. Step 5 and Step 7 2 (LS-4) According to the testing table, what would be the conclusion of the operating effectiveness of the administrator testing? a. Due to all users having appropriate administrator access, no exception is noted b. Due to majority users having appropriate administrator access, no exception is noted Due to one user, having inappropriate administrator access, an exception is noted 3. (LS-4) As an administrator, they have the access to add, modify, and delete user information in the applications According to the Cycle Matrix, what is the Control Description for LS 42 a Logical controls exist and are followed to properly authenticate identified entities access to materially relevant financial IT applications and supporting systems for elevated user access Privileged-level access is authorized and appropriately restricted b. Access granted to privileged-level shared, generic, service and/or vendor accounts is appropriately secured, and passwords to such accounts are modified on a periodic basis cAccess to physical facilities is restricted to authorized personnel and requires appropriate identification and authentication Physical access to data center is authorized and appropriately restricted 4 (LS-3) Why is this control not operating effectively? Type here to search Convert tur 100 An audit client, New Hire Training Group, LLC (NHTG), has a small group of employees (16) that perform many functions within the Company. NHTG has the following systems in-scope for IT SOX testing Active Directory: network FultiPro cloud-based, hosted HCM solution Prophecy purchased ERP (no access to source), on premise solution SQL Server 2012: Prophecy Production database Windows Server 2012 Prophecy Production application server After performing initial walkthroughs and reviewing the Organization Chart, the audit team determines that there are 3 network administrators, 2 FultiPro administrators, 3 Prophecy administrators, and 2 database administrators. The audit team also confirmed that, in keeping with best practices, users outside of IT should not be application administrators, apart from FultiPro. The audit team also confirmed that the Prophecy and FultiPro applications are configured such that users authenticate with user id and passwords unique to the application. Users with access to the database and operating system layers authenticate using Windows Active Directory (AD) credentials via Single Sign-On (SSO) a Questions: (LS-4) What two steps (see test of operating effectiveness section) from lead sheet 0335.74_LS_PS lead sheet explain how the auditor would confirm the access is appropriate for the administrative user? Step 4 and Step 5 b Step 4 and Step 7 c. Step 5 and Step 7 2 (LS-4) According to the testing table, what would be the conclusion of the operating effectiveness of the administrator testing? Due to all users having appropriate administrator access, no exception is noted. Type here to search 2. C Step 5 and Step 2. (LS-4) According to the testing table, what would be the conclusion of the operating effectiveness of the administrator testing? a. Due to all users having appropriate administrator access, no exception is noted. b. Due to majority users having appropriate administrator access, no exception is noted. C. Due to one user, having inappropriate administrator access, an exception is noted. 3. (LS-4) As an administrator, they have the access to add, modify, and delete user information in the applications. According to the Cycle Matrix, what is the Control Description for LS-4? a. Logical controls exist and are followed to properly authenticate identified entities access to materially relevant financial IT applications and supporting systems for elevated user access. Privileged-level access is authorized and appropriately restricted. b. Access granted to privileged-level shared, generic, service and/or vendor accounts is appropriately secured, and passwords to such accounts are modified on a periodic basis. Access to physical facilities is restricted to authorized personnel and requires appropriate identification and authentication. Physical access to data center is authorized and appropriately restricted. 4. (LS-3) Why is this control not operating effectively? The control is operating effectively b. For the Windows Server 2012 and Windows SOL Server 2012, authentication cannot be configured via Windows Active Directory, therefore the control is not operating effectively C The Windows AD password reuse parameters does not match the password policy parameter as noted in F98. 5 (LS-3) Why are the password parameters for each applications compared to 1 overarching company policy? a. To ensure all password policies are aligned with the company policy standard and do not have standards that are lower and less secure than what the company has set . a. o ype here to search C b. To choose the best application for the company to use going forward. None of the above, the password parameters for each application are not compared and are all tested as separate entities 6. (All - Open ended question) If an exception is noted, what should the auditor do to communicate that to the client? Logical Access Case Study: Provisioning/De-Provisioning Access & User Access Reviews The audit team confirmed that the process to provision and de provision user access follows a similar manually-driven process. In both instances, a manager must send an email to the system administrator requesting access be added or remove for a user. If provisioning access, the manager must indicate the role(s) required for the user, ensuring that the principle of least privileged is followed. Terminated user's access must be removed within 3 business days of the date of termination. The system administrator is to retain the email request for audit purposes. Further, the audit team noted that the Company is planning to implement a ticketing system with an automated workflow to facilitate the access provisioning and de- provisioning request process. Presently, no user access reviews are performed. Given the small size of the Company, the infrequent nature of changes in positions, and the infrequent turnover, the NHTG has determined that there is a low risk of inappropriate access Questions: 1 What risk is mitigated by the manager having to request the role for a new user? a) Terminated employees retain access after their departure date b) Terminated employees do not retain access after their departure date Thomanacor munnt anroach the case of giving access to the principle of load Type here to search nature of changes in positions, and the infrequent turnover, the NHTG has determined that there is a low risk of inappropriate access. Questions: 1. What risk is mitigated by the manager having to request the role for a new user? a) Terminated employees retain access after their departure date. b) Terminated employees do not retain access after their departure date. c) The manager may not approach the process of giving access with the principle of least privilege d) The manager may approach the process of giving access with the principle of least privilege 2 What does it mean to assign access"in keeping with the principle of least privileged?" a) Making sure the employee has the least amount of access in order to successfully perform his/her job role. b) Making sure the employee has more access than is required to successfully perform his/her job role c) Making sure the employee has no access at all d) Making sure all employees have the same level of access regardless of role 3. Is the response to the low risk associated with not performing a user access review appropriate? What risks are the Company exposed to if without periodic UARS? a) Yes, potential unauthorized users may be able to get away with functions or be exposed to information that may be confidential b) No, potential unauthorized users may be able to get away with functions or be exposed to information that may be confidential c) No terminated employees may retain access after their departure date d) Yes the Company is not exposed to any other risks. Type here to search Role / Privilege Employee Name Title Termination De-Provision Date Date Administrator Administrator Administrator N/A 1/12/2021 3/6/2021 N/A 1/15/2021 3/7/2021 Windows AD - Domain Administrator John Doe System Administrator Michael Maxwell IT Specialist 11 Paul Molive IT Specialist Prophecy (App) John Doe Systems Administrator Michael Maxwell IT Specialist 11 IT Security Manager N/A N/A 1/12/2021 1/15/2021 Paul Molive IT Define Users and Roles IT Define Users and Roles IT Security Manager 3/6/2021 IT Specialisti 3/7/2021 2/22/2021 2/29/2021 DBA DBA N/A 1/12/2021 1/15/2021 N/A NA Security Admin Kathleen Dixon Consultant Prophecy (Database) John Doe System Administrator Michael Maxwell IT Specialist 11 Prophecy (Operating System) John Doe Systems Administrator Michael Maxwell IT Specialist II FultiPro Derek Frapples HR Manager Anna Mull Payroll Intern 1/12/2021 1/15/2021 Security Admin 3/18/2021 1/8/2021 3/19/2021 1/12/2021 Administrator Administrator E Type here to search 4. What documentation would be needed to verify the employee's access was de provisioned timely? a. No documentation would be needed b. Only the email requesting removal of access. C. Email requesting access be removed, documented verification that the access was successfully removed. d. Email requesting access be removed, documented verification that the access was successfully removed, documentation of the employee's termination from the Compan 5. Are there any users whose user access was not terminated in accordance with Company polic e. Yes, two users. f. Yes, one user g. No, all users access was removed appropriately h. Yes, three users. 6 How would the ticketing system help streamline the de-provisioning process? Type here to search Home Insert Page Layout Formulas Data Review View Developer Help Furry Lookup X Arial 10 - ' EE General LE 2 Wiap lant Merge Center BI $ - % Delele Il Format Conditional Format set Formatting Table Styles - Co board Font Alignment Number 9 Describe in detail how the Control Operator executes the control. 5 Tested Control Tested Control Description Logical controls and are followed to property Ruthentical tertified entities access to material relevant financial Toplications and supporting systems for sale 7 level access is authored and appropriately restricted B 9 LIONSTEST mpanti 10 11 Auditor Prepared Control Documentation to Supplement Client Prepared Documentation 12 13 Name and the Control Describe us forumondott.Contes escribe the one John Doe System Admirator John Doe over 20 year of experience Manager over the structure John Doe System Antorforms periodic US Access 14 Software App Devent and was an as wined with 2014 tard and veged users 15 Identify the information (including the source used by the Control Describe how the core Operator cures macacy of Description of low carb the Operator in performing the contro info 10 System user es ist exports (showing accountty Observed a report generation and the screenshots of the recorrer ting the deet system 17 Described how the Control Operator the control include the critical steps performed by the Control Operator and site igricantes or correo eleton 20 vide or document their performance of the control 21 Shop nagement reviews and respect Step 2 angement checks that can compte 23 Step Management showing of precio del Monte 24 Step Fxconsentified by the Control Opera 25 Steps Any reviewers are greated from it and an eng 27 25 Walkthrough Procedures to Confirm Understanding 100% of Domandant Enterprise OwWwWADE MANAGER IT DERE USERS AND ROLES wis Prophecies LS 4 O Type here to search Home Insert ' 79 Arial Page Layout Formulas Data Review View Developer Help Fuzzy Lookup 10-AA Wap Test General Conditional Formatas C 0-A-Meige Cente $ - % ** Formatting Table Styles Font Alignment 5 hube Sona B TV- Cell board 3 Describe in detail how the Control Operator executes the control 27 20 Walkthrough Procedures to Confirm Understanding Samochod 100% of "Demon Add Entre Answi Widows AD, SECURITY NA MANAGER" and "IT DEFNE USERS AND ROLES W Precy appland Admite 31 of Controlering what TOVAR 32 me fem the widerstandige resto iro, the contemples designed for control of an 14 Dec w procedures performers Per wory with John Doe (System Administrator) on TB, REMUS LUP Alive must be approved by John Dos System Anwich VW Ambedded need to accounts for access Prophecy The roles that allow seculty in the Prophecy option toghed by T SECURITY MANAGERSERS OROUS Windows Active Directory for a domain and energie there Pro: The roles that we do is the reception editing by w 36 16 DVD of proceres performed by a 37 perator There may be the same used in the woods or the 3 worcom 40 41 TO 4 Document testing to including the same internal Audit Dette Dom LS Type here to search Fide Home Insert Page Layout Formulas Data Review View Developer Help Fuzzy Loop 247 Anal - 10 ' ' E- Wraport a. A-Merge Center Al General $ - % 9 Paste Telete- Fannat Conditional Formulas C Formatting Table Styles Sys Clipboard Font A19 Describe in detail how the Control Operator executes the control Deine neue of the plant was como of the 47 Morblywende symptomer BONGOWE WARTY CUSS AND BOLSA Windows or 0935521 per 635751 (A 0335721 (2) 033572 0335521 AGR 205 40 1 word of the System Araratmetr Michael Star VR 2) One of accounts Wort - Reviewed to weaven and led necelled Testing y oth Don And which wieder af si Souryosohe Dots de POLICY OMNIS D Sted SSB Type to search - Delete - go o Home Insert Page Layout Formulas Review View Developer Help Fuery Lookup Arial OSAA Weit General 19- BIU. OA- Conditional Format Cell Mestemte $ - % 3 Formatting - - Styles Font Alig Number Describe in detail how the Control Operator executes the control C D 225 0 Prophecy FUERTO Prophecy 3) Prophecy 05 Select Sect Se Select 60 65 Seneste bydra 54 66 Tests of Operating tflectiveness 70 Testa operating sites de son of your worse 71 article these werden 72 In the 74 75 70 77 78 79 De 01 For conserve our way A dependent Testing LS-4 Type here to search th review View Developer Help Futy tookup - WE 2 Arial 10 - AN Wap tert BIU-- A. Merge Center Font Alignment $ % 9 Delete- Format Conditional Form Cell Formatting Tile Styles Styles Sort lied There 5 C board Nusbet 3 Describe in detail how the Control Operator executes the control, Operating Title Puriya Account Name Employee Name Acces Ace 37520 Y System Jomo Sym de Spec Y Y Y 104 Wich Pave 2 Mole Privilege 100 101 Windows AD - Domain Administrator Admistrator 102 103 2 Admin Admin 105 Astrator 106 Prophecy (Apel IT Security Manager 107 2 IT Detee Users and 100 IT Defne Users and 109 4 One Users and 110 Y boe A Y AM 112 Ny Dates De www 116 115 116 4 Die Lec ES 19 Type here to search SI Arial General 249.0 10 A A 39 Weapol a. A- 3. Menge Cotter BIU $ - % ST Forma Conditional Format Call Formatting Table Styles Sy pboard Font Alignment Number Eating .19 Describe in detail how the Control Operator executes the control 112 Prophecy (Database Y 03057521 OBA dont System A Spec 113 114 115 116 2 2 4 5 UBA Sym John Doe Michael Maxwell Sadetut utch Oce Y Y Y soldat batch me orciemen ICCOUNT Oracle Per our se ndodh 003452 el Syst A pel howed w Bate 117 518 Prophecy Operating System) Security Admin 115 120 Saty 121 Setud 122 Ture 123 Amor 124 Admin 125 120 He Anna NA Merethe COMENCEM 129 130 Tickmark tegen 133 132 133 NA No 2 130 13 Che HOME type to search REM View Developer Help Furry tookup X Arial 10 -A A 29 Wiap Text SE O Merge & Center BIO a. A General S.% Conditional Format Cell Formatting Table Styles Number Style Sortid F Clipboard Font Alignment A51 Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and FaltiPro password configurations 8 TestedConte Tested Contraction 155 Password curty configuration Securit and activity weet ensure that the systems are. Acested to 7 to validate that users are thod to gain Pword present they formation security cold standarte PENETIN 10 11 Auditor Prepared Control Documentation to Supplement Client Prepared Documentation 12 13 d. Ton Control Dance Quote Contrato John Don System Admin hoe over 20 year of CE Meterware John Systems A verses the Software Development and team wina w 2014 control the password as we determine Securit 14 Procedure wchwed contrast 15 dentify the information (including sourced by the Control Describe how the control Operus completeness of Opens in performing the control no Open the path 16 - 0335 74 52 et Password Setting Od screts of the 0335 74 33 Prophecy Password with a strong 17-0335 74 34 Ft Pro Password Setting 13 19 Describe in how the Control Operwore the control ce the critical steps performed by the Control pertanian started 20 evidence of door therBromance at the con 21 22 24 24 2 Waugh Procedures to confirm Understanding 15- Type here to search nur Arial 10 - A A SE 2 Wrap Test General $ - % **- Paste BIU- 3 Meige Center format Conditional Format Formatting Table Styles Styles Chpboard Font Alignment Number C ASI Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and Fultipro password configurations 27 28 Walkthrough Procedures to Confirm Understanding 29 30 Sample sched NIA Full population Med 31 Name of Control Oranged with D model Roy.com 32 Did the procedures sont the understanding stone? Vesti the controleerd ghed for com defesa de come 34 Documentational walitog procedures performed centre con espected and tons of the Per inquiry we John Doe (System Administrator) on (telRSMUS ULP Unique D's are used for all user accounts, and no shared accounts (otside of bullen we account for each cupes RSS LLPced the ring of use of ique Ds See LS-2 regarding NATO signing uniques and accountably being and for eachers The following password requirements are then the Password Policy03067 - Must be at least characters length - Must contain characters from three of the following algunes English ease, Englewoon Cannot contain the user's accountname e parts of the var's name that we had must be changed every 90 days Cannot be changed more than once within 24 hours Cannot have been used within a review changes 35 transcendente Documentation of where performed may be enhanced by the there are the coffectivement 40 41 44 Document testing plan including me samples and one of L3 19 Type here to search Developer Help Fuzzy Loop Arial General aste BIV - 10 AM 2 Wrap lect a. Ata Menge di Center Font Alignment 5 - %9 23-28 Udele Conditional Formats Cell Formatting Table Styles format Sort fie upboard 19 Number 51 Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and FultiPro password configurations 39 the control desgned effectively and effe 40 to the site for control deficiency, and remainder of forma nature 41 42 SECTION OLIVE 43 44 Document testing plan including the sample size and use of internal Audit 45 45 Define the nature of the poputong won an occurrence of the como powerpoint 47 Identity the source le system reporta) used to defy the population WOTE WGO Password Properties Fol System Security Setting 48 49 50 Describe the procedures performed by the store.com Outined the current Password Policy, and screenshots of the current Windows AD Prophecy, FutPro possword configurations 53 54 __ 0 Tests of Operating Effectiveness 87 66 Tests of operating effects includes combination of natyrspection, bere were spectre premier 15 O Type here to search Insert Page Layout Formulas Data Review View Developer Help Fuzzy Lookup Shure Arial AA 29 Wrap Test General $ - % Merge & Center - Format Conditional Formatas Cel Formatting - Table Styles Shles Sto da Sed A De Font Alignment 5 Number Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and FultiPro password configurations of Operating effectiveness of operating effectiveness nude combustion of inquiry, spection, observation and reperformance Wien performing of operating euro Eins of the controls defined above) were performed and any oto end above were dete Step 2 Step p4 Step 5 Descroton Test to Dich was perford by the Contacted Alert Hures for Rent Osona. DE System generated into secology and ped report onder report parameters to content meer as een spect the user to determosed to Chand Bags W O cory of NATO's word standarde conformen scury spect decat the password Gepard Diode Selections Tested by Internal Audit Bucand appropriate but I should be for so by Password ett Cum Autos independent Testing 2 Arcy and Voor Application use of que MIA 101 Type here to search Arial - B TV- 10 Az Wrap Text General Delet- A.A. 23 Merge Center $ - % 9 51 Conditional Formats Cel Formatting Table Styles Format Anment Number Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and FultiPro password configurations card Font x 102 Windows Server Windows SQL 103 Server 2012 Authentication figured vi Windows Active Directory (AD) Single Sign-On Si Reference Windows AD testing above 100 Summit in any trenden testing below 1111 112 Tickmark legend Y 115 116 NA Notes Note 2 Yes Testing comed the Copercuted the contep No Tesling did not even the contre parte de contrast Hotectie Pace specific needed Pace Chord 119 500 101 12. 103 164 is the control operating effectively resto] 106 Motel Gevist observed that the wedding for the conclude the 100 19 170 171 2 13 53 14 O Type here to search ACIS 4024 Cases 114% - Do Expo The audit team also confirmed that the Prophecy and FultiPro applications are configured such that users Buthenticate with user id and passwords unique to the application Users with access to the database and operating system layers authonticate using Windows Active Directory (AD) credentials via Single Sign-On (SSO) Adobe Exp Convert POHY of Excel One Select POF ACIS 4024 Convert to Micos Document English C Questions: 1 (LS-4) What two stops (see test of operating effectiveness section) from lead sheet 0335.74 LS_PS lead sheet explain how the auditor would confirm the access is appropriate for the administrative user? a Step 4 and Step 5 b. Step 4 and Step 7 c. Step 5 and Step 7 2 (LS-4) According to the testing table, what would be the conclusion of the operating effectiveness of the administrator testing? a. Due to all users having appropriate administrator access, no exception is noted b. Due to majority users having appropriate administrator access, no exception is noted Due to one user, having inappropriate administrator access, an exception is noted 3. (LS-4) As an administrator, they have the access to add, modify, and delete user information in the applications According to the Cycle Matrix, what is the Control Description for LS 42 a Logical controls exist and are followed to properly authenticate identified entities access to materially relevant financial IT applications and supporting systems for elevated user access Privileged-level access is authorized and appropriately restricted b. Access granted to privileged-level shared, generic, service and/or vendor accounts is appropriately secured, and passwords to such accounts are modified on a periodic basis cAccess to physical facilities is restricted to authorized personnel and requires appropriate identification and authentication Physical access to data center is authorized and appropriately restricted 4 (LS-3) Why is this control not operating effectively? Type here to search Convert tur 100 An audit client, New Hire Training Group, LLC (NHTG), has a small group of employees (16) that perform many functions within the Company. NHTG has the following systems in-scope for IT SOX testing Active Directory: network FultiPro cloud-based, hosted HCM solution Prophecy purchased ERP (no access to source), on premise solution SQL Server 2012: Prophecy Production database Windows Server 2012 Prophecy Production application server After performing initial walkthroughs and reviewing the Organization Chart, the audit team determines that there are 3 network administrators, 2 FultiPro administrators, 3 Prophecy administrators, and 2 database administrators. The audit team also confirmed that, in keeping with best practices, users outside of IT should not be application administrators, apart from FultiPro. The audit team also confirmed that the Prophecy and FultiPro applications are configured such that users authenticate with user id and passwords unique to the application. Users with access to the database and operating system layers authenticate using Windows Active Directory (AD) credentials via Single Sign-On (SSO) a Questions: (LS-4) What two steps (see test of operating effectiveness section) from lead sheet 0335.74_LS_PS lead sheet explain how the auditor would confirm the access is appropriate for the administrative user? Step 4 and Step 5 b Step 4 and Step 7 c. Step 5 and Step 7 2 (LS-4) According to the testing table, what would be the conclusion of the operating effectiveness of the administrator testing? Due to all users having appropriate administrator access, no exception is noted. Type here to search 2. C Step 5 and Step 2. (LS-4) According to the testing table, what would be the conclusion of the operating effectiveness of the administrator testing? a. Due to all users having appropriate administrator access, no exception is noted. b. Due to majority users having appropriate administrator access, no exception is noted. C. Due to one user, having inappropriate administrator access, an exception is noted. 3. (LS-4) As an administrator, they have the access to add, modify, and delete user information in the applications. According to the Cycle Matrix, what is the Control Description for LS-4? a. Logical controls exist and are followed to properly authenticate identified entities access to materially relevant financial IT applications and supporting systems for elevated user access. Privileged-level access is authorized and appropriately restricted. b. Access granted to privileged-level shared, generic, service and/or vendor accounts is appropriately secured, and passwords to such accounts are modified on a periodic basis. Access to physical facilities is restricted to authorized personnel and requires appropriate identification and authentication. Physical access to data center is authorized and appropriately restricted. 4. (LS-3) Why is this control not operating effectively? The control is operating effectively b. For the Windows Server 2012 and Windows SOL Server 2012, authentication cannot be configured via Windows Active Directory, therefore the control is not operating effectively C The Windows AD password reuse parameters does not match the password policy parameter as noted in F98. 5 (LS-3) Why are the password parameters for each applications compared to 1 overarching company policy? a. To ensure all password policies are aligned with the company policy standard and do not have standards that are lower and less secure than what the company has set . a. o ype here to search C b. To choose the best application for the company to use going forward. None of the above, the password parameters for each application are not compared and are all tested as separate entities 6. (All - Open ended question) If an exception is noted, what should the auditor do to communicate that to the client? Logical Access Case Study: Provisioning/De-Provisioning Access & User Access Reviews The audit team confirmed that the process to provision and de provision user access follows a similar manually-driven process. In both instances, a manager must send an email to the system administrator requesting access be added or remove for a user. If provisioning access, the manager must indicate the role(s) required for the user, ensuring that the principle of least privileged is followed. Terminated user's access must be removed within 3 business days of the date of termination. The system administrator is to retain the email request for audit purposes. Further, the audit team noted that the Company is planning to implement a ticketing system with an automated workflow to facilitate the access provisioning and de- provisioning request process. Presently, no user access reviews are performed. Given the small size of the Company, the infrequent nature of changes in positions, and the infrequent turnover, the NHTG has determined that there is a low risk of inappropriate access Questions: 1 What risk is mitigated by the manager having to request the role for a new user? a) Terminated employees retain access after their departure date b) Terminated employees do not retain access after their departure date Thomanacor munnt anroach the case of giving access to the principle of load Type here to search nature of changes in positions, and the infrequent turnover, the NHTG has determined that there is a low risk of inappropriate access. Questions: 1. What risk is mitigated by the manager having to request the role for a new user? a) Terminated employees retain access after their departure date. b) Terminated employees do not retain access after their departure date. c) The manager may not approach the process of giving access with the principle of least privilege d) The manager may approach the process of giving access with the principle of least privilege 2 What does it mean to assign access"in keeping with the principle of least privileged?" a) Making sure the employee has the least amount of access in order to successfully perform his/her job role. b) Making sure the employee has more access than is required to successfully perform his/her job role c) Making sure the employee has no access at all d) Making sure all employees have the same level of access regardless of role 3. Is the response to the low risk associated with not performing a user access review appropriate? What risks are the Company exposed to if without periodic UARS? a) Yes, potential unauthorized users may be able to get away with functions or be exposed to information that may be confidential b) No, potential unauthorized users may be able to get away with functions or be exposed to information that may be confidential c) No terminated employees may retain access after their departure date d) Yes the Company is not exposed to any other risks. Type here to search Role / Privilege Employee Name Title Termination De-Provision Date Date Administrator Administrator Administrator N/A 1/12/2021 3/6/2021 N/A 1/15/2021 3/7/2021 Windows AD - Domain Administrator John Doe System Administrator Michael Maxwell IT Specialist 11 Paul Molive IT Specialist Prophecy (App) John Doe Systems Administrator Michael Maxwell IT Specialist 11 IT Security Manager N/A N/A 1/12/2021 1/15/2021 Paul Molive IT Define Users and Roles IT Define Users and Roles IT Security Manager 3/6/2021 IT Specialisti 3/7/2021 2/22/2021 2/29/2021 DBA DBA N/A 1/12/2021 1/15/2021 N/A NA Security Admin Kathleen Dixon Consultant Prophecy (Database) John Doe System Administrator Michael Maxwell IT Specialist 11 Prophecy (Operating System) John Doe Systems Administrator Michael Maxwell IT Specialist II FultiPro Derek Frapples HR Manager Anna Mull Payroll Intern 1/12/2021 1/15/2021 Security Admin 3/18/2021 1/8/2021 3/19/2021 1/12/2021 Administrator Administrator E Type here to search 4. What documentation would be needed to verify the employee's access was de provisioned timely? a. No documentation would be needed b. Only the email requesting removal of access. C. Email requesting access be removed, documented verification that the access was successfully removed. d. Email requesting access be removed, documented verification that the access was successfully removed, documentation of the employee's termination from the Compan 5. Are there any users whose user access was not terminated in accordance with Company polic e. Yes, two users. f. Yes, one user g. No, all users access was removed appropriately h. Yes, three users. 6 How would the ticketing system help streamline the de-provisioning process? Type here to search Home Insert Page Layout Formulas Data Review View Developer Help Furry Lookup X Arial 10 - ' EE General LE 2 Wiap lant Merge Center BI $ - % Delele Il Format Conditional Format set Formatting Table Styles - Co board Font Alignment Number 9 Describe in detail how the Control Operator executes the control. 5 Tested Control Tested Control Description Logical controls and are followed to property Ruthentical tertified entities access to material relevant financial Toplications and supporting systems for sale 7 level access is authored and appropriately restricted B 9 LIONSTEST mpanti 10 11 Auditor Prepared Control Documentation to Supplement Client Prepared Documentation 12 13 Name and the Control Describe us forumondott.Contes escribe the one John Doe System Admirator John Doe over 20 year of experience Manager over the structure John Doe System Antorforms periodic US Access 14 Software App Devent and was an as wined with 2014 tard and veged users 15 Identify the information (including the source used by the Control Describe how the core Operator cures macacy of Description of low carb the Operator in performing the contro info 10 System user es ist exports (showing accountty Observed a report generation and the screenshots of the recorrer ting the deet system 17 Described how the Control Operator the control include the critical steps performed by the Control Operator and site igricantes or correo eleton 20 vide or document their performance of the control 21 Shop nagement reviews and respect Step 2 angement checks that can compte 23 Step Management showing of precio del Monte 24 Step Fxconsentified by the Control Opera 25 Steps Any reviewers are greated from it and an eng 27 25 Walkthrough Procedures to Confirm Understanding 100% of Domandant Enterprise OwWwWADE MANAGER IT DERE USERS AND ROLES wis Prophecies LS 4 O Type here to search Home Insert ' 79 Arial Page Layout Formulas Data Review View Developer Help Fuzzy Lookup 10-AA Wap Test General Conditional Formatas C 0-A-Meige Cente $ - % ** Formatting Table Styles Font Alignment 5 hube Sona B TV- Cell board 3 Describe in detail how the Control Operator executes the control 27 20 Walkthrough Procedures to Confirm Understanding Samochod 100% of "Demon Add Entre Answi Widows AD, SECURITY NA MANAGER" and "IT DEFNE USERS AND ROLES W Precy appland Admite 31 of Controlering what TOVAR 32 me fem the widerstandige resto iro, the contemples designed for control of an 14 Dec w procedures performers Per wory with John Doe (System Administrator) on TB, REMUS LUP Alive must be approved by John Dos System Anwich VW Ambedded need to accounts for access Prophecy The roles that allow seculty in the Prophecy option toghed by T SECURITY MANAGERSERS OROUS Windows Active Directory for a domain and energie there Pro: The roles that we do is the reception editing by w 36 16 DVD of proceres performed by a 37 perator There may be the same used in the woods or the 3 worcom 40 41 TO 4 Document testing to including the same internal Audit Dette Dom LS Type here to search Fide Home Insert Page Layout Formulas Data Review View Developer Help Fuzzy Loop 247 Anal - 10 ' ' E- Wraport a. A-Merge Center Al General $ - % 9 Paste Telete- Fannat Conditional Formulas C Formatting Table Styles Sys Clipboard Font A19 Describe in detail how the Control Operator executes the control Deine neue of the plant was como of the 47 Morblywende symptomer BONGOWE WARTY CUSS AND BOLSA Windows or 0935521 per 635751 (A 0335721 (2) 033572 0335521 AGR 205 40 1 word of the System Araratmetr Michael Star VR 2) One of accounts Wort - Reviewed to weaven and led necelled Testing y oth Don And which wieder af si Souryosohe Dots de POLICY OMNIS D Sted SSB Type to search - Delete - go o Home Insert Page Layout Formulas Review View Developer Help Fuery Lookup Arial OSAA Weit General 19- BIU. OA- Conditional Format Cell Mestemte $ - % 3 Formatting - - Styles Font Alig Number Describe in detail how the Control Operator executes the control C D 225 0 Prophecy FUERTO Prophecy 3) Prophecy 05 Select Sect Se Select 60 65 Seneste bydra 54 66 Tests of Operating tflectiveness 70 Testa operating sites de son of your worse 71 article these werden 72 In the 74 75 70 77 78 79 De 01 For conserve our way A dependent Testing LS-4 Type here to search th review View Developer Help Futy tookup - WE 2 Arial 10 - AN Wap tert BIU-- A. Merge Center Font Alignment $ % 9 Delete- Format Conditional Form Cell Formatting Tile Styles Styles Sort lied There 5 C board Nusbet 3 Describe in detail how the Control Operator executes the control, Operating Title Puriya Account Name Employee Name Acces Ace 37520 Y System Jomo Sym de Spec Y Y Y 104 Wich Pave 2 Mole Privilege 100 101 Windows AD - Domain Administrator Admistrator 102 103 2 Admin Admin 105 Astrator 106 Prophecy (Apel IT Security Manager 107 2 IT Detee Users and 100 IT Defne Users and 109 4 One Users and 110 Y boe A Y AM 112 Ny Dates De www 116 115 116 4 Die Lec ES 19 Type here to search SI Arial General 249.0 10 A A 39 Weapol a. A- 3. Menge Cotter BIU $ - % ST Forma Conditional Format Call Formatting Table Styles Sy pboard Font Alignment Number Eating .19 Describe in detail how the Control Operator executes the control 112 Prophecy (Database Y 03057521 OBA dont System A Spec 113 114 115 116 2 2 4 5 UBA Sym John Doe Michael Maxwell Sadetut utch Oce Y Y Y soldat batch me orciemen ICCOUNT Oracle Per our se ndodh 003452 el Syst A pel howed w Bate 117 518 Prophecy Operating System) Security Admin 115 120 Saty 121 Setud 122 Ture 123 Amor 124 Admin 125 120 He Anna NA Merethe COMENCEM 129 130 Tickmark tegen 133 132 133 NA No 2 130 13 Che HOME type to search REM View Developer Help Furry tookup X Arial 10 -A A 29 Wiap Text SE O Merge & Center BIO a. A General S.% Conditional Format Cell Formatting Table Styles Number Style Sortid F Clipboard Font Alignment A51 Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and FaltiPro password configurations 8 TestedConte Tested Contraction 155 Password curty configuration Securit and activity weet ensure that the systems are. Acested to 7 to validate that users are thod to gain Pword present they formation security cold standarte PENETIN 10 11 Auditor Prepared Control Documentation to Supplement Client Prepared Documentation 12 13 d. Ton Control Dance Quote Contrato John Don System Admin hoe over 20 year of CE Meterware John Systems A verses the Software Development and team wina w 2014 control the password as we determine Securit 14 Procedure wchwed contrast 15 dentify the information (including sourced by the Control Describe how the control Operus completeness of Opens in performing the control no Open the path 16 - 0335 74 52 et Password Setting Od screts of the 0335 74 33 Prophecy Password with a strong 17-0335 74 34 Ft Pro Password Setting 13 19 Describe in how the Control Operwore the control ce the critical steps performed by the Control pertanian started 20 evidence of door therBromance at the con 21 22 24 24 2 Waugh Procedures to confirm Understanding 15- Type here to search nur Arial 10 - A A SE 2 Wrap Test General $ - % **- Paste BIU- 3 Meige Center format Conditional Format Formatting Table Styles Styles Chpboard Font Alignment Number C ASI Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and Fultipro password configurations 27 28 Walkthrough Procedures to Confirm Understanding 29 30 Sample sched NIA Full population Med 31 Name of Control Oranged with D model Roy.com 32 Did the procedures sont the understanding stone? Vesti the controleerd ghed for com defesa de come 34 Documentational walitog procedures performed centre con espected and tons of the Per inquiry we John Doe (System Administrator) on (telRSMUS ULP Unique D's are used for all user accounts, and no shared accounts (otside of bullen we account for each cupes RSS LLPced the ring of use of ique Ds See LS-2 regarding NATO signing uniques and accountably being and for eachers The following password requirements are then the Password Policy03067 - Must be at least characters length - Must contain characters from three of the following algunes English ease, Englewoon Cannot contain the user's accountname e parts of the var's name that we had must be changed every 90 days Cannot be changed more than once within 24 hours Cannot have been used within a review changes 35 transcendente Documentation of where performed may be enhanced by the there are the coffectivement 40 41 44 Document testing plan including me samples and one of L3 19 Type here to search Developer Help Fuzzy Loop Arial General aste BIV - 10 AM 2 Wrap lect a. Ata Menge di Center Font Alignment 5 - %9 23-28 Udele Conditional Formats Cell Formatting Table Styles format Sort fie upboard 19 Number 51 Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and FultiPro password configurations 39 the control desgned effectively and effe 40 to the site for control deficiency, and remainder of forma nature 41 42 SECTION OLIVE 43 44 Document testing plan including the sample size and use of internal Audit 45 45 Define the nature of the poputong won an occurrence of the como powerpoint 47 Identity the source le system reporta) used to defy the population WOTE WGO Password Properties Fol System Security Setting 48 49 50 Describe the procedures performed by the store.com Outined the current Password Policy, and screenshots of the current Windows AD Prophecy, FutPro possword configurations 53 54 __ 0 Tests of Operating Effectiveness 87 66 Tests of operating effects includes combination of natyrspection, bere were spectre premier 15 O Type here to search Insert Page Layout Formulas Data Review View Developer Help Fuzzy Lookup Shure Arial AA 29 Wrap Test General $ - % Merge & Center - Format Conditional Formatas Cel Formatting - Table Styles Shles Sto da Sed A De Font Alignment 5 Number Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and FultiPro password configurations of Operating effectiveness of operating effectiveness nude combustion of inquiry, spection, observation and reperformance Wien performing of operating euro Eins of the controls defined above) were performed and any oto end above were dete Step 2 Step p4 Step 5 Descroton Test to Dich was perford by the Contacted Alert Hures for Rent Osona. DE System generated into secology and ped report onder report parameters to content meer as een spect the user to determosed to Chand Bags W O cory of NATO's word standarde conformen scury spect decat the password Gepard Diode Selections Tested by Internal Audit Bucand appropriate but I should be for so by Password ett Cum Autos independent Testing 2 Arcy and Voor Application use of que MIA 101 Type here to search Arial - B TV- 10 Az Wrap Text General Delet- A.A. 23 Merge Center $ - % 9 51 Conditional Formats Cel Formatting Table Styles Format Anment Number Obtained the current Password Policy. Obtained screenshots of the current Windows AD, Prophecy, and FultiPro password configurations card Font x 102 Windows Server Windows SQL 103 Server 2012 Authentication figured vi Windows Active Directory (AD) Single Sign-On Si Reference Windows AD testing above 100 Summit in any trenden testing below 1111 112 Tickmark legend Y 115 116 NA Notes Note 2 Yes Testing comed the Copercuted the contep No Tesling did not even the contre parte de contrast Hotectie Pace specific needed Pace Chord 119 500 101 12. 103 164 is the control operating effectively resto] 106 Motel Gevist observed that the wedding for the conclude the 100 19 170 171 2 13 53 14 O Type here to search
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


