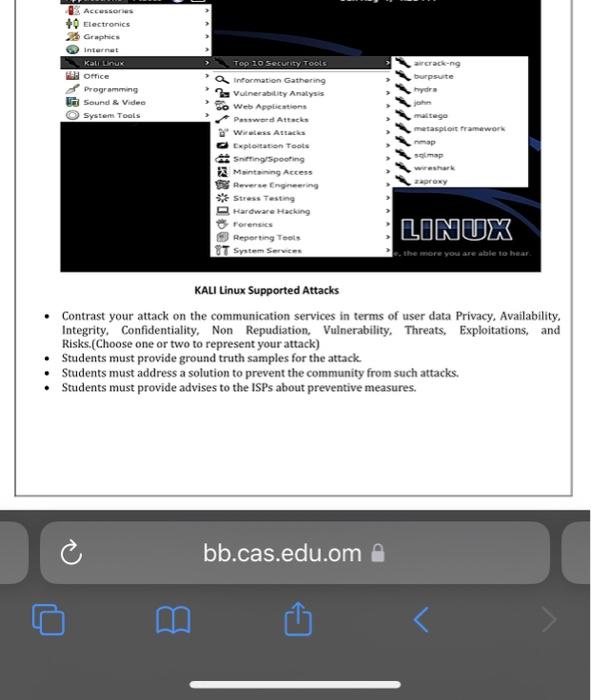
Aims of the project: - Enhance student capability to learn and research beyond the lectures. - Enhance student ability to work individually/group and represents his/her knowledge through the written report. - Enhance student ability to work as group and represents their knowledge through the presentation. - Enhance student creativity in applying all the concepts learnt in lectures and labs as core for the basic implementations needed for work environment. - Enhance student ability to evaluate and audit any given security related case study and implement the required security system practically. - Enhance student ability to work and implement within the time frame. Team Size: 2 Report Structure: Cover page with (Unique "Project Title") Project Approval Form Marking Guide sheet Introduction Objectives Survey (Give 100 words of previous/ongoing research about the topic you have chosen. Include the Sources in the References page) Project Flow Diagram Implementation Result Interpretation (Tables, Statistics, Graph, etc.) Conclusion References Appendices X Total number of pages is between 15 to 30 pages {A4}. x Follow standard typeset format for report x Use comb binding for the report, first and last page are transparent. * Copy and paste is not allowed. You are expected to produce you own report. x If there are two similar asyignments, both will receive 2 IEO. it does not matter who copied from whiom! x It is recommended that you show your progreis to your instructor to make sure you are on the right direction. x Avoid submitting on the las day as you are doing so at your drwn risk. Never leare things so the last minute. You should always account for Internet connections problems and other problems that youl might encounter an the last day. x You must upload a softcopy of your teport in Blackboard Safe Adsignment to encure no plagaram. x Submit hardoopy report during week-14, presentation at week-15. X Submit hardcopy report to the course instructor two days before the presentation. The Case Study Implementation: Telecommunication Srstem - Stadents are requested to discuss the current security system in a Telecom secters and inplement a solution to secure users' data. - Students can discuss only one of many Wired or Wireless internet telecommanicabion senices for this case stady implementation. - Student must choose "A Project Title" in relation with the attack and the prevention stratero- [Ex. "Securing User Data from Network Spoofiag? - Students must generate an attack on a user data in the telecom services using Uinat KAll and Windows Client Virtual Favironment. - Students mast choose one of the following types of attacks supported by the MALI Linus OS. for experiments. - *N Lo Internet allowed for presenting the project, Non-working or without implementation. broiects will be disaualified. KAlI Linux Supported Attacks - Contrast your attack on the communication services in terms of user data Privacy, Availability, Integrity, Confidentiality, Non Repudiation, Vulnerability, Threats, Exploitations, and Risks. (Choose one or two to represent your attack) - Students must provide ground truth samples for the attack. - Students must address a solution to prevent the community from such attacks. - Students must provide advises to the ISPs about preventive measures