Answered step by step
Verified Expert Solution
Question
1 Approved Answer
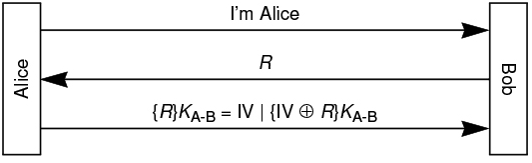
Alice and Bob use the mechanism shown in the following figure for authentication. In specific, after Alice informs Bob she wants to communicate, Bob generates
Alice and Bob use the mechanism shown in the following figure for authentication. In specific, after Alice informs Bob she wants to communicate, Bob generates a random number R and sends it back to Alice.
Assume R fits into a single block and Alice encrypts R in CBC mode, so RKAB is computed as IV xor RKAB where IV is Alice created for CBC operation. Alice then sends IV and IV xor RKAB to Bob, as shown in the rd message in the figure.
Suppose Eve sees an exchange between Alice and Bob, where the challenge is R How can Eve then impersonate Alice, during a different conversation where Bob sends a different challenge R
To get full credit, completely describe the content of messages Eve sends to Bob, and at what time. That is you need to describe the message exchange in a timeline.
Please explain it cleary and in details because I am learning about it I am confused because if Eve does R XOR RKAB and sends this to Bob, how Bob decrypts it before XOR with IV of CBC since Eve doesn't know KAB?
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


