Answer 5,6,7 and 8
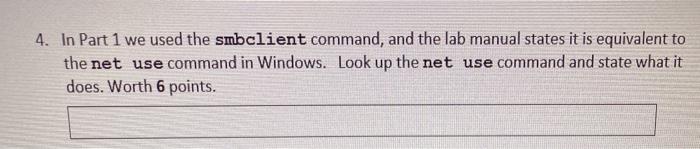
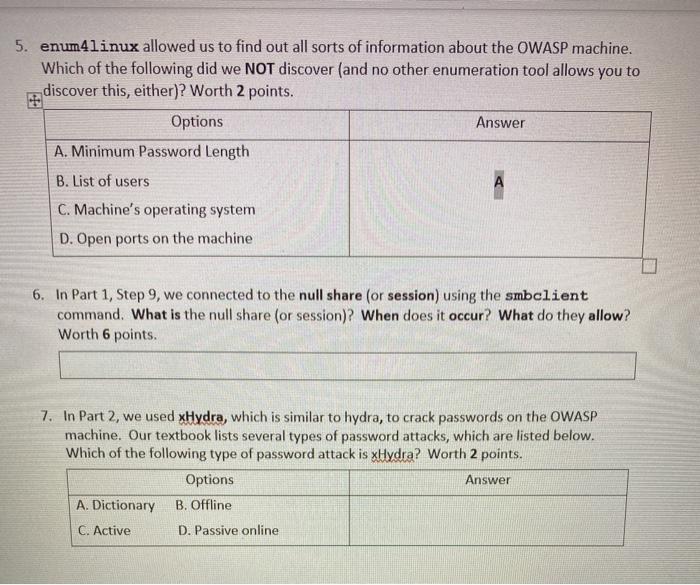
4. In Part 1 we used the smbclient command, and the lab manual states it is equivalent to the net use command in Windows. Look up the net use command and state what it does. Worth 6 points. 5. enum4linux allowed us to find out all sorts of information about the OWASP machine. Which of the following did we NOT discover (and no other enumeration tool allows you to discover this, either)? Worth 2 points. Options Answer A. Minimum Password Length A B. List of users C. Machine's operating system D. Open ports on the machine 6. In Part 1, Step 9, we connected to the null share (or session) using the smbclient command. What is the null share (or session)? When does it occur? What do they allow? Worth 6 points. 7. In Part 2, we used xHydra, which is similar to hydra, to crack passwords on the OWASP machine. Our textbook lists several types of password attacks, which are listed below. Which of the following type of password attack is xHydra? Worth 2 points. Options Answer A. Dictionary B. Offline C. Active D. Passive online 4. In Part 1 we used the smbclient command, and the lab manual states it is equivalent to the net use command in Windows. Look up the net use command and state what it does. Worth 6 points. 5. enum4linux allowed us to find out all sorts of information about the OWASP machine. Which of the following did we NOT discover (and no other enumeration tool allows you to discover this, either)? Worth 2 points. Options Answer A. Minimum Password Length A B. List of users C. Machine's operating system D. Open ports on the machine 6. In Part 1, Step 9, we connected to the null share (or session) using the smbclient command. What is the null share (or session)? When does it occur? What do they allow? Worth 6 points. 7. In Part 2, we used xHydra, which is similar to hydra, to crack passwords on the OWASP machine. Our textbook lists several types of password attacks, which are listed below. Which of the following type of password attack is xHydra? Worth 2 points. Options Answer A. Dictionary B. Offline C. Active D. Passive online