Question: Answer all for a thumbs up! QUESTION 1 Internet Control Message Protocol (ICMP) is a method of IP address assignment that uses an alternate, public
 Answer all for a thumbs up!
Answer all for a thumbs up!
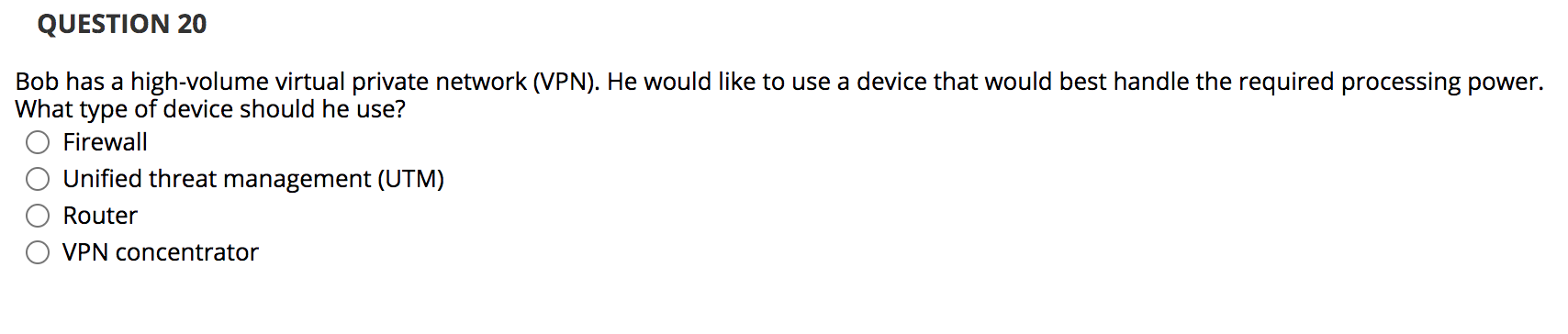
QUESTION 1 Internet Control Message Protocol (ICMP) is a method of IP address assignment that uses an alternate, public IP address to hide a system's real IP address. True False QUESTION 2 Implicit deny is when firewalls look at message addresses O True determine whether a message is being sent around an unending loop. False QUESTION 3 A border router can provide enhanced features to internal networks and help keep subnet traffic separate. True False QUESTION 4 The Transport Layer of the OSI Reference Model creates, maintains, and disconnects communications that take place between processes over the network. True False QUESTION 5 Internet Small Computer System Interface (iSCSI) is a storage networking standard used to link data storage devices to networks using IP for its transport layer. True False QUESTION 6 A network protocol governs how networking equipment interacts to deliver data across the network. True False QUESTION 7 A wireless access point (WAP) is the connection between a wired and wireless network. O True False QUESTION 8 IP addresses are eight-byte addresses that uniquely identify every device on the network. O True False QUESTION 9 TCP/IP is a suite of protocols that operates at both the Network and Transport layers of the OSI Reference Model. O True O False QUESTION 10 A subnet mask is a partition of a network based on IP addresses. True False QUESTION 11 Henry would like to create a different firewall rule that allows encrypted web traffic to reach a web server. What port is used for that communication? 80 143 443 3389 QUESTION 12 Hilda is troubleshooting a problem with the encryption of data. At which layer of the OSI Reference Model is she working? O Application Presentation Session Data Link QUESTION 13 What wireless security technology contains significant flaws and should never be used? Wired Equivalent Privacy (WEP) Wi-Fi Protected Access (WPA) WPA2 Remote Authentication Dial-In User Service (RADIUS) QUESTION 14 What type of network connects systems over the largest geographic area? Wide area network (WAN) Metropolitan area network (MAN) Local area network (LAN) Storage area network (SAN) QUESTION 15 Gary is configuring a Smartphone and is selecting a wireless connectivity method. Which approach will provide him with the highest speed wireless connectivity? Wi-Fi 3G 4G Digital subscriber line (DSL) QUESTION 16 Norm recently joined a new organization. He noticed that the firewall technology used by his new firm opens separate connections between the devices on both sides of the firewall. What type of technology is being used? Packet filtering Application proxying Stateful inspection Network address translation QUESTION 17 What protocol is responsible for assigning IP addresses to hosts on most networks? O Dynamic Host Configuration Protocol (DHCP) Transport Layer Security (TLS) Virtual LAN (VLAN) Simple Mail Transfer Protocol (SMTP) QUESTION 18 Henry's last firewall rule must allow inbound access to a Windows Terminal Server. What port must he allow? 143 443 989 3389 QUESTION 19 Val would like to isolate several systems belonging to the product development group from other systems on the network, without adding new hardware. What technology can she use? Firewall Virtual LAN (VLAN) Virtual private network (VPN) Transport Layer Security (TLS) QUESTION 20 Bob has a high-volume virtual private network (VPN). He would like to use a device that would best handle the required processing power. What type of device should he use? Firewall Unified threat management (UTM) Router VPN concentrator
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


