Question
ANSWER ALL The set ? is characterised as the least set such that if X is finite and X ? ? , then X ?
ANSWER ALL
The set ? is characterised as the least set such that if X is finite and X ? ? , then X ? [ X ? ? [Recall S X =def {y | ?x ? X. y ? x}.] (a) Show (i) ? ? ? , and [2 marks] (ii) if x ? ? then {x} ? x ? ? . [3 marks] (b) State the rule(s) and the principle of rule induction appropriate for the set ?. [3 marks] (c) Define a set x to be transitive iff ?z, y. z ? y & y ? x ? z ? x Prove that all elements of ? are transitive. [8 marks] (d) Describe, without proof, the elements of the set ?.
Reminder: f(n) ? ?(g(n)) ?? ? n0, c1, c2 ? R>0 such that ?n > n0 : 0 < c1g(n) ? f(n) ? c2g(n). (a) For the bubblesort algorithm, state its best-case ? complexity and describe, for any given input of arbitrary size n, one permutation that would trigger this best-case behaviour. Then give the corresponding permutation of . Then repeat the above for the worst case: state the ? complexity, saying when it is achieved, and exhibit as a concrete example a permutation of the 10 numbers given. [4 marks] (b) Repeat Part (a) for the heapsort algorithm. [4 marks] (c) Repeat Part (a) for the basic quicksort algorithm, where the pivot is simply chosen as the last element in the range. [4 marks] (d) Write clear and efficient pseudocode to eliminate all duplicates from a linked list of n elements, without changing the order of the remaining elements. Then derive and justify its ? complexity. [4 marks] (e) [Hint: The ? notation, like the ? notation, is typically used to describe the asymptotic behaviour of a worst-case cost function f(n). When we say, by extension, that a certain task has a complexity bound of ?(g(n)), we mean that this bound applies to the worst-case cost function of every possible algorithm that could solve that task.] Give a formula for f(n) ? ?(g(n)), in a format similar to that of the Reminder above, and briefly explain it. Then derive, with a clear justification, a tight ? complexity bound for the task of eliminating all duplicates from a linked list of n elements. [4 marks]
A software engineer is developing computer-aided design software for an architect who works with designs for three different types of building: Contemporary, Victorian, and Roman. When laying out buildings, the architect places windows, doorways, walls and roofs in the appropriate style for the building on which she is working. Explain, including all the Java interfaces and code fragments, how the software can use the Abstract Factory design pattern to construct and maintain its internal data structures representing a building. [6 marks] (b) In terms of software testing, what is equivalence partitioning, how can it be done, and how can the partitioned sets be used to select test patterns? [6 marks] (c) What are decision coverage and condition coverage? [2 marks] (d) Describe Java's Remote Method Invocation (RMI) system, including the means by which objects and servers are named, how clients perform binding, and the CodeBase. [6 marks]
What is meant by a serializable order for two or more transactions? [2 marks] (b) Explain how timestamp ordering (TSO) enforces isolation. [5 marks] (c) Draw and explain a history graph for two transactions whose invocations of a set of conflicting operations are serializable but which are rejected by TSO. [5 marks] (d) Considering Optimistic Concurrency Control (OCC): (i) State the properties of a transaction's set of shadow copies that must be verified at commit time. [2 marks] (ii) Carefully explain the algorithm used by a single-threaded commit-time validator. [4 marks] (e) Consider a system in which the transactions cause updates to objects which are not all located on a single server but which are distributed widely around the Internet. What factors would influence your choice of using TSO or OCC to enforce isolation? [2 marks
) Give a brief description of the three segments that make up the Global Positioning System (GPS), and their main software, hardware and information components. [5 marks] (b) What are the main timing observables from the GPS signals, and how can they be processed to give time, position and velocity? [5 marks] (c) What data is broadcast in the GPS signals, and how is it used by receivers? [5 marks] (d) Explain some of the ways in which an additional communication channel can be used to assist a GPS receiver, and what advantages the user might observe. [5 marks]
an object-oriented language, such as Java, that does not provide a coroutine
mechanism. [5 marks]
6 Compiler Construction
(a) Describe one possible structure
answer by considering the form of object fifile which might result from the
following C program.
int a = 1, b = -1;
extern int g(int);
extern int c;
int f() { return g(a-b) + c; }
It is not necessary to consider the exact instruction sequence, just issues
concerning its interaction with the object fifile format. [10 marks]
(b) Describe how a linker takes a sequence of such programs and produces an
executable fifile. [4 marks]
(c) Compare and contrast static and dynamic linking in a system using your object
fifile format. [6 marks]
4CST.2001.6.5
7 Prolog for Artifificial Intelligence
A weighted binary tree can be defifined using compound terms in the following way.
A node of the tree is represented by the term n(V, L, R), where V stands for the
value of the node, and L and R stand for the left and right branches, respectively.
A terminal node has the R and L components instantiated to the null list.
Given an input tree T, write a Prolog program that constructs a tree of the same
shape as T, but in which the value of each node has been set to the value of the
maximum value node in T.
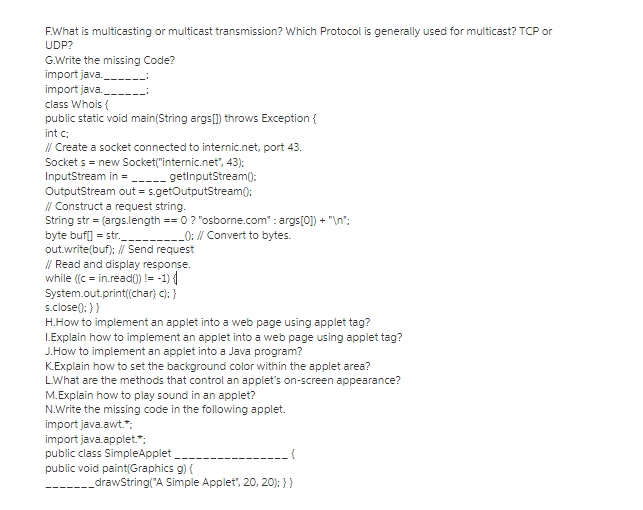

F.What is multicasting or multicast transmission? Which Protocol is generally used for multicast? TCP or UDP? G.Write the missing Code? import java.___ import java. class Whois { public static void main(String args[]) throws Exception { int c; // Create a socket connected to internic.net, port 43. Socket s = new Socket("internic.net", 43); InputStream in =_____getInputStream(): OutputStream out=s.getOutputStream(): // Construct a request string. String str = (args.length == 0 ? "osborne.com" : args[0]) + " "%; byte buf[] = str._____________0: // Convert to bytes. out.write(buf); //Send request // Read and display response. while ((c = in.read()) != -1){| System.out.print((char) c); } s.close(): >> H.How to implement an applet into a web page using applet tag? 1.Explain how to implement an applet into a web page using applet tag? J.How to implement an applet into a Java program? K.Explain how to set the background color within the applet area? L.What are the methods that control an applet's on-screen appearance? M.Explain how to play sound in an applet? N.Write the missing code in the following applet. import java.awt.*: import java.applet.*: public class Simple Applet public void paint(Graphics g) { .{ ____drawstring("A Simple Applet", 20, 20); }}
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


