Question
ANSWER in your own words Case Scenario: CreditSolutions v FTC Read the case scenario at https://www.ftc.govews-events/press-releases/2006/02/cardsystems-solutions-settles-ftc-charges the article is ALSO attached to the assignment. Based
ANSWER in your own words
Case Scenario: CreditSolutions v FTC Read the case scenario at https://www.ftc.govews-events/press-releases/2006/02/cardsystems-solutions-settles-ftc-charges the article is ALSO attached to the assignment.
 Based upon PCI DSS Security Standards, summarized above, answer the following questions
Based upon PCI DSS Security Standards, summarized above, answer the following questions
Who do you think is negligent in this case and why?
Explain which requirements werent met and how those violate the Federal Trade Commission Act.
Recommend two or three mitigation remedies to prevent the same thing from happening at another organization.
What are the possible consequences associated with the data loss?
Who do you think is ultimately responsible for the CardSystems Solutions lack of PCI DSS compliance? Why?
Utilize an Internet search and explain bitcoin?
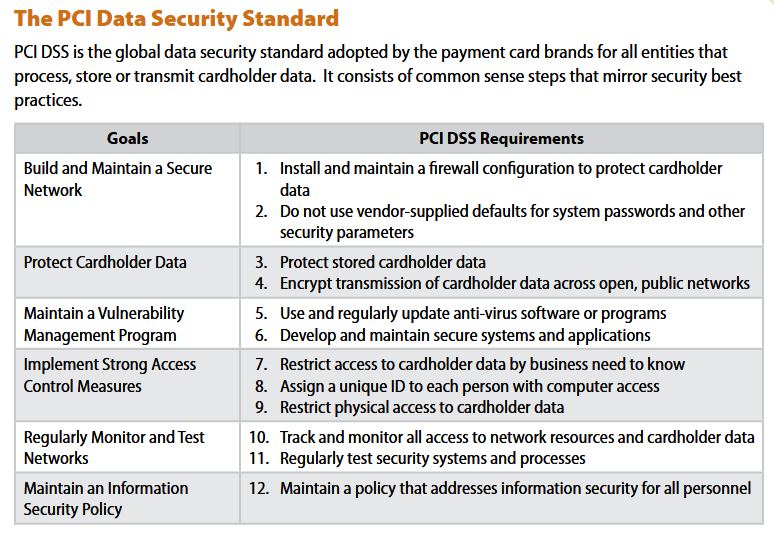
The PCI Data Security Standard PCI DSS is the global data security standard adopted by the payment card brands for all entities that process, store or transmit cardholder data. It consists of common sense steps that mirror security best practices. Goals PCI DSS Requirements Build and Maintain a Secure 1. Install and maintain a firewall configuration to protect cardholder Network data 2. Do not use vendor-supplied defaults for system passwords and other security parameters Protect Cardholder Data 3. Protect stored cardholder data 4. Encrypt transmission of cardholder data across open, public networks Maintain a Vulnerability 5. Use and regularly update anti-virus software or programs Management Program 6. Develop and maintain secure systems and applications Implement Strong Access 7. Restrict access to cardholder data by business need to know Control Measures 8. Assign a unique ID to each person with computer access 9. Restrict physical access to cardholder data Regularly Monitor and Test 10. Track and monitor all access to network resources and cardholder dat Networks 11. Regularly test security systems and processes Maintain an Information 12. Maintain a policy that addresses information security for all personnel Security PolicyStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


