Question
Applied Cryptography In any language --------------------------------------------- rsa.data Problem 1 part (b) =================== RSA public key (e,N) and plaintext m is given by e := 3
Applied Cryptography
In any language
---------------------------------------------
rsa.data
Problem 1 part (b) =================== RSA public key (e,N) and plaintext m is given by
e := 3
N := 505653012503429218243943633705672380046318162980074400525290686010978535210508251025371556786334751948415457926276892598751961027794016968235973613925881804782472056690499897096340749266251887257171654630228493856549694979043602485084236106517977998198816346622004351187096835097200490691844506811161067102443 m := 427680787658796414495478412765818481773700031964971550032485995462094541318172071699678633526190831000613031464300541848882252073989630802044992230370499993349891121354055409063481101792420859297579606741599372692821291104228771117776673746157967849667351681259816188574800065511460953723930836865732656293632
Problem 1 part (c) =================== RSA public key (e,N) and plaintext m is given by
e := 179769313486231590772930519078902473361797697894230657273430081157732675805500963132708477322407536021120113879871393357658789768814416622492847430639474124377767893424865485276302219601246094119453082952085005768838150682342462881473913110540827237163350510684586298239947245938479716304835356329624224137235
N := 265395747779081530877606237236349849228314744900899433856115970650569628926732597441099813244463093724241524668073327069367685544353023894309092930986368718041241356517138905842047363627287275378041992895737394917902969620822954148050418803997890441829764379787051809840244543961639445759733471607073670456391
m := 169051735219277475590231826992974517584441289846373794226549986850732257294817560343439820742236655054611741163389887885546533767164727501809070917083967679791988612511599825319307291827649611965899446561279620094290833000580211022270963614195517284629675578909864668070831108552374275648786037092684278007819
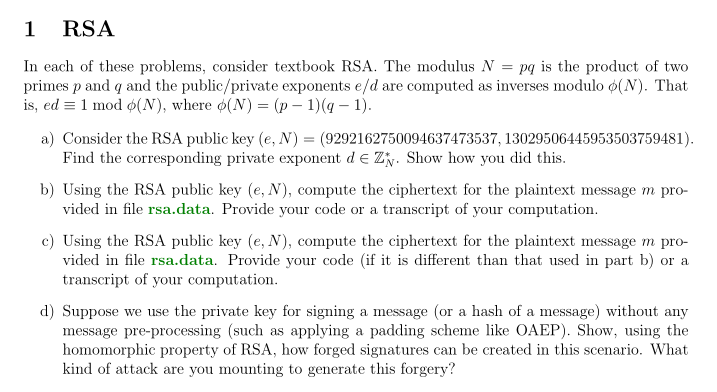
1 RSA In each of these problems, consider textbook RSA. The modulus N = pq is the product of two primes p and q and the public/private exponents e d are computed as inverses modulo (N That is, ed-1 mod (N), where (N) = (p-1)(q-1). a) Consider the RSA public key (e, N) (9292162750094637473537, 13029506445953503759481). Find the corresponding private exponent dE Z. Show how you did this b) Using the RSA public key (e, V), compute the ciphertext for the plaintext message m pro- vided in file rsa.data. Provide your code or a transcript of your computation. c) Using the RSA public key (e, N), compute the ciphertext for the plaintext message m pro- vided in file rsa.data. Provide your code (if it is different than that used in part b) or a transcript of your computation. d) Suppose we use the private key for signing a message (or a hash of a message) without any message pre-processing (such as applying a padding scheme like OAEP). Show, using the homomorphic property of RSA, how forged signatures can be created in this scenario. What kind of attack are you mounting to generate this forgeryStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


