Question: assenment no 4 r project is separete question but connected with each other .so i need code of both question with ruuning screenshots Data Encryption
assenment no 4 r project is separete question but connected with each other .so i need code of both question with ruuning screenshots
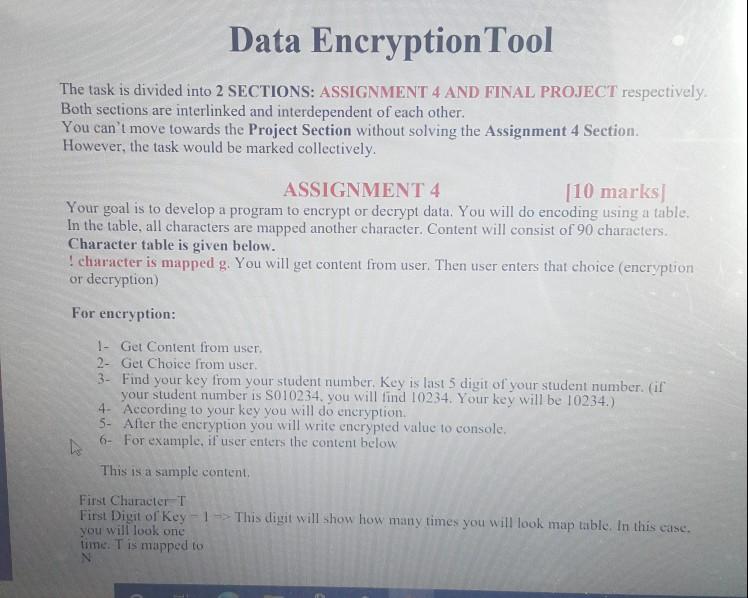
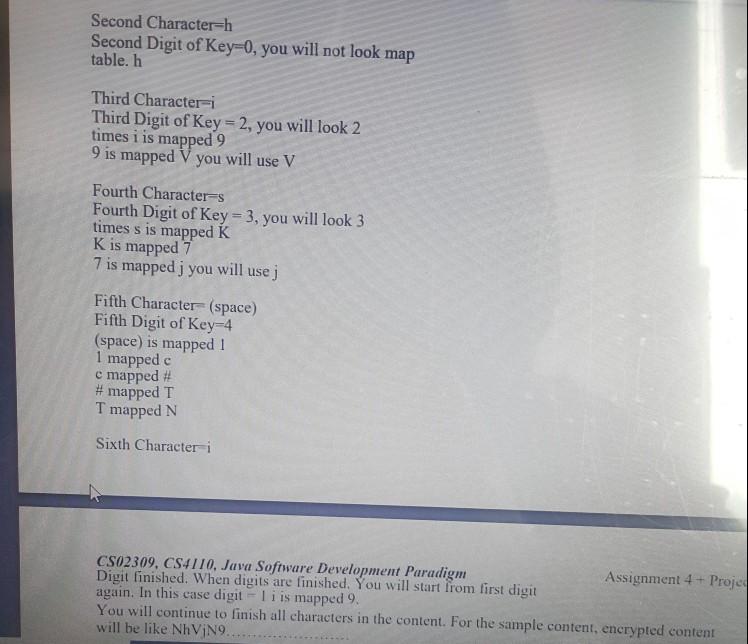
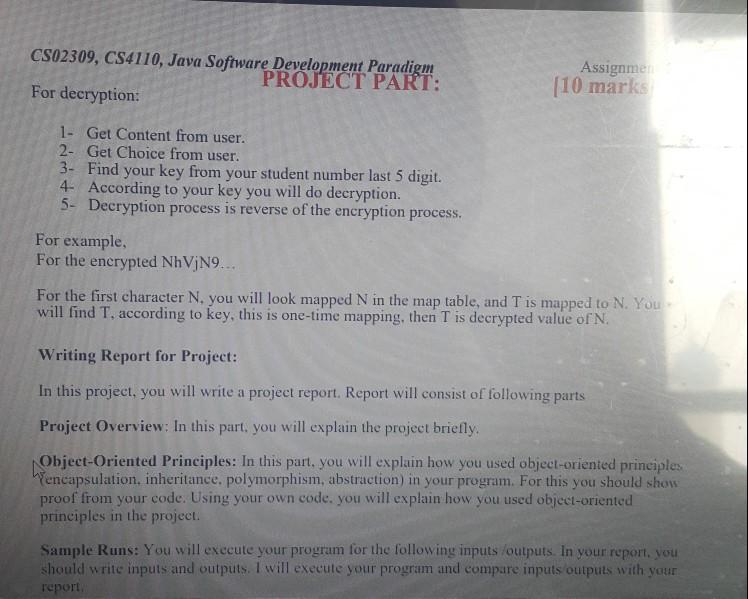
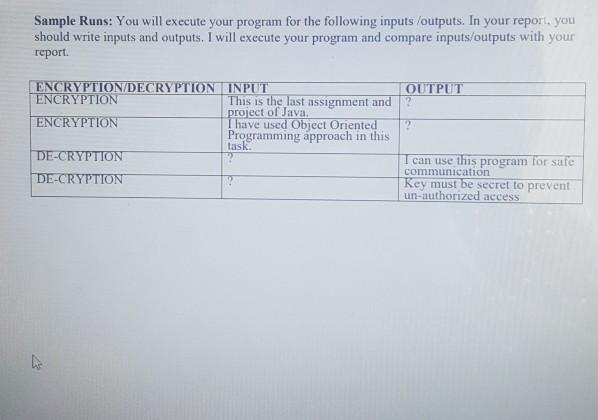
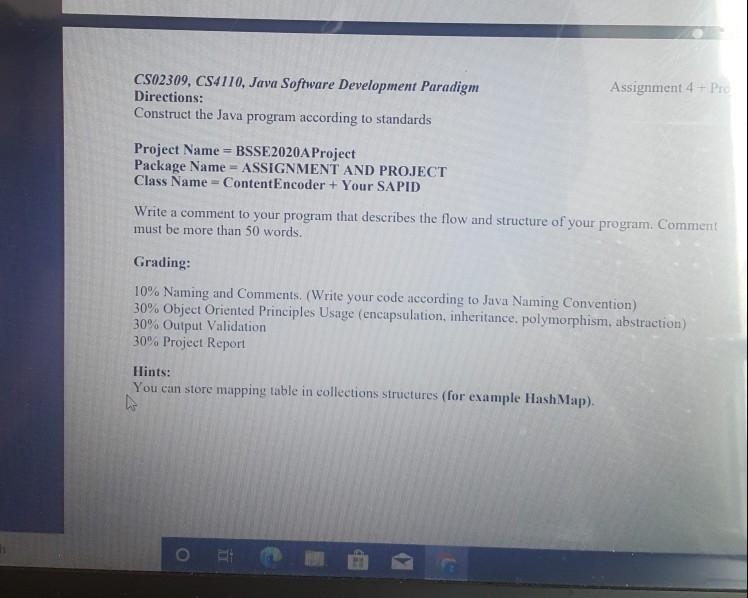
Data Encryption Tool The task is divided into 2 SECTIONS: ASSIGNMENT 4 AND FINAL PROJECT respectively Both sections are interlinked and interdependent of each other. You can't move towards the Project Section without solving the Assignment 4 Section However, the task would be marked collectively. ASSIGNMENT 4 [10 marks) Your goal is to develop a program to encrypt or decrypt data. You will do encoding using a table. In the table, all characters are mapped another character. Content will consist of 90 characters. Character table is given below. ! character is mapped g. You will get content from user. Then user enters that choice (encryption or decryption) For encryption: 1- Get Content from user 2- Get Choice from user 3. Find your key from your student number. Key is last 5 digit of your student number. (if your student number is S010234. you will find 10234. Your key will be 10234.) 4- According to your key you will do encryption 5- After the encryption you will write encrypted value to console. 6- For example, if user enters the content below This is a sample content First Character T First Digit of Key 1 -> This digit will show how many times you will look map table. In this case, you will look one time. Tis mapped to Second Character=h Second Digit of Key=0, you will not look map table. h Third Characteri Third Digit of Key = 2, you will look 2 times i is mapped 9 9 is mapped V you will use V Fourth Characters Fourth Digit of Key = 3, you will look 3 times s is mapped K Kis mapped 7 7 is mapped j you will use j Fifth Character (space) Fifth Digit of Key=4 (space) is mapped 1 1 mapped c c mapped # # mapped T T mapped N Sixth Characteri CS02309, CS4110, Java Software Development Paradigm Assignment 4+ Proje Digit finished. When digits are finished. You will start from first digit again. In this case digit -liis mapped 9. You will continue to finish all characters in the content. For the sample content, encrypted content will be like NhVjN9 CS02309, CS4110, Java Software Development Paradigm PROJECT PART: For decryption: Assignme 10 marks 1- Get Content from user. 2- Get Choice from user. 3- Find your key from your student number last 5 digit. 4. According to your key you will do decryption. 5- Decryption process is reverse of the encryption process. For example, For the encrypted NhVjN9... For the first character N. you will look mapped N in the map table, and T is mapped to N. You will find T. according to key, this is one-time mapping, then T is decrypted value of N. Writing Report for Project: In this project, you will write a project report. Report will consist of following parts Project Overview: In this part. you will explain the project briefly. Object-Oriented Principles: In this part, you will explain how you used object-oriented principles Wencapsulation, inheritance, polymorphism, abstraction in your program. For this you should show proof from your code. Using your own code, you will explain how you used object-oriented principles in the project Sample Runs: You will execute your program for the following inputs/outputs. In your report, you should write inputs and outputs. I will execute your program and compare inputs outputs with your report, Sample Runs: You will execute your program for the following inputs /outputs. In your report, you should write inputs and outputs. I will execute your program and compare inputs/outputs with your report. OUTPUT 2 ENCRYPTION/DECRYPTION INPUT ENCRYPTION This is the last assignment and project of Java, ENCRYPTION I have used Object Oriented Programming approach in this DE-CRYPTION task DE-CRYPTION I can use this program for sale communication Key must be secret to prevent un-authorized access z CS02309, CS4110, Java Software Development Paradigm Directions: Construct the Java program according to standards Assignment 4-Pro Project Name = BSSE 2020A Project Package Name = ASSIGNMENT AND PROJECT Class Name = ContentEncoder + Your SAPID Write a comment to your program that describes the flow and structure of your program. Comment must be more than 50 words. Grading: 10% Naming and Comments. (Write your code according to Java Naming Convention) 30% Object Oriented Principles Usage (encapsulation, inheritance, polymorphism, abstraction) 30% Output Validation 30% Project Report Hints: You can store mapping table in collections structures (for example Hash Map). Data Encryption Tool The task is divided into 2 SECTIONS: ASSIGNMENT 4 AND FINAL PROJECT respectively Both sections are interlinked and interdependent of each other. You can't move towards the Project Section without solving the Assignment 4 Section However, the task would be marked collectively. ASSIGNMENT 4 [10 marks) Your goal is to develop a program to encrypt or decrypt data. You will do encoding using a table. In the table, all characters are mapped another character. Content will consist of 90 characters. Character table is given below. ! character is mapped g. You will get content from user. Then user enters that choice (encryption or decryption) For encryption: 1- Get Content from user 2- Get Choice from user 3. Find your key from your student number. Key is last 5 digit of your student number. (if your student number is S010234. you will find 10234. Your key will be 10234.) 4- According to your key you will do encryption 5- After the encryption you will write encrypted value to console. 6- For example, if user enters the content below This is a sample content First Character T First Digit of Key 1 -> This digit will show how many times you will look map table. In this case, you will look one time. Tis mapped to Second Character=h Second Digit of Key=0, you will not look map table. h Third Characteri Third Digit of Key = 2, you will look 2 times i is mapped 9 9 is mapped V you will use V Fourth Characters Fourth Digit of Key = 3, you will look 3 times s is mapped K Kis mapped 7 7 is mapped j you will use j Fifth Character (space) Fifth Digit of Key=4 (space) is mapped 1 1 mapped c c mapped # # mapped T T mapped N Sixth Characteri CS02309, CS4110, Java Software Development Paradigm Assignment 4+ Proje Digit finished. When digits are finished. You will start from first digit again. In this case digit -liis mapped 9. You will continue to finish all characters in the content. For the sample content, encrypted content will be like NhVjN9 CS02309, CS4110, Java Software Development Paradigm PROJECT PART: For decryption: Assignme 10 marks 1- Get Content from user. 2- Get Choice from user. 3- Find your key from your student number last 5 digit. 4. According to your key you will do decryption. 5- Decryption process is reverse of the encryption process. For example, For the encrypted NhVjN9... For the first character N. you will look mapped N in the map table, and T is mapped to N. You will find T. according to key, this is one-time mapping, then T is decrypted value of N. Writing Report for Project: In this project, you will write a project report. Report will consist of following parts Project Overview: In this part. you will explain the project briefly. Object-Oriented Principles: In this part, you will explain how you used object-oriented principles Wencapsulation, inheritance, polymorphism, abstraction in your program. For this you should show proof from your code. Using your own code, you will explain how you used object-oriented principles in the project Sample Runs: You will execute your program for the following inputs/outputs. In your report, you should write inputs and outputs. I will execute your program and compare inputs outputs with your report, Sample Runs: You will execute your program for the following inputs /outputs. In your report, you should write inputs and outputs. I will execute your program and compare inputs/outputs with your report. OUTPUT 2 ENCRYPTION/DECRYPTION INPUT ENCRYPTION This is the last assignment and project of Java, ENCRYPTION I have used Object Oriented Programming approach in this DE-CRYPTION task DE-CRYPTION I can use this program for sale communication Key must be secret to prevent un-authorized access z CS02309, CS4110, Java Software Development Paradigm Directions: Construct the Java program according to standards Assignment 4-Pro Project Name = BSSE 2020A Project Package Name = ASSIGNMENT AND PROJECT Class Name = ContentEncoder + Your SAPID Write a comment to your program that describes the flow and structure of your program. Comment must be more than 50 words. Grading: 10% Naming and Comments. (Write your code according to Java Naming Convention) 30% Object Oriented Principles Usage (encapsulation, inheritance, polymorphism, abstraction) 30% Output Validation 30% Project Report Hints: You can store mapping table in collections structures (for example Hash Map)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


