Attached is the risk register for Sheffield University one of the top universities in the UK) in the year 2016. Analyse the document to highlight the risks affecting the students directly, and how to mitigate each risk?
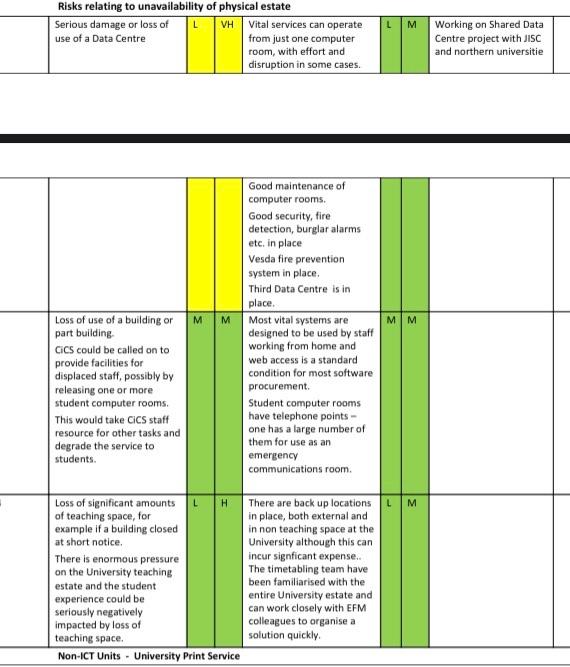
student Risk Register February 2016 CICS manages the risks to the ICT infrastructure that supports most of the vital functions of the University. Our internal risk management information will have a more complex structure than the register layout suggested. Each system of service supports various types of vital activity in the University and is at risk from many causes, each with its own preventive measures. Systems are also heavily interdependent. The recommended Risk Register layout has too few dimensions to express this complexity and can only provide a simple summary Loss or degradation of any ITC system would clearly be categorised as an infrastructure risk, but this could be misleading as learning, financial processes, research etc could all be affected equally. Instead we have given more than one category, as a number against most risks. To give them in order of risk exposure would be almost meaningless and this has not been attempted. We have not listed planned actions against most is. Many major actions were identified earlier and are now complete. They are shown as controls in the register These are either major investments in equipment and facilities or ongoing processes within Olcs. Further actions are likely to be identified as the new assessment process develops CCS has a Business Continuity Plan and a great deal of other information to be used when various types of incidents occur. This has not been mentioned in the Register as it applies to every risk We have not listed opportunities alongside the risks. They are a very different type of use in this area. Categories - Most is items relate to 1. 4. 6 and 7 1 Estates Infrastructure. IT Business Continuity 2. External relationships and partners 3. Financial 4. Learning. Teaching, Student experience 5. Organisational development and strategy 6. Research and innovation 7. Service quality 8 Staffing and Human Resources L M Risks relating to unavailability of physical estate Serious damage or loss of L VH Vital services can operate use of a Data Centre from just one computer room, with effort and disruption in some cases. Working on Shared Data Centre project with JISC and northern universitie M M MM Loss of use of a building or part building CiCs could be called on to provide facilities for displaced staff, possibly by releasing one or more student computer rooms This would take CCS staff resource for other tasks and degrade the service to students. Good maintenance of computer rooms. Good security, fire detection, burglar alarms etc. in place Vesda fire prevention system in place. Third Data Centre is in place. Most vital systems are designed to be used by staff working from home and web access is a standard condition for most software procurement Student computer rooms have telephone points - one has a large number of them for use as an emergency communications room. L M Loss of significant amounts H of teaching space, for example if a building closed at short notice. There is enormous pressure on the University teaching estate and the student experience could be seriously negatively impacted by loss of teaching space. Non-ICT Units - University Print Service There are back up locations in place, both external and in non teaching space at the University although this can incur signficant expense. The timetabling team have been familiarised with the entire University estate and can work closely with EFM colleagues to organise a solution quickly