Question
Authentication and Password Systems Assignment In standard Unix, the /etc/passwd file contains user information. It is world-readable. Look it up and learn about it (man
Authentication and Password Systems Assignment
In standard Unix, the /etc/passwd file contains user information. It is world-readable. Look it up and learn about it (man 5 passwd). The /etc/shadow file contains user password information. It is only readable with special permissions. Look it up and read about it (man 5 shadow).
Login to the system we will use by typing ssh p53997
From the shell, acquire root privileges (type sudo su and enter your password). Then add a user to the system, call it otheruser_
Now, respond to the following:
(25 pts) Look at and provide a screenshot of the /etc/passwd and /etc/shadow files that shows the user you added. Find the field in the shadow file containing the users password. Take a screenshot and highlight the field.
(25 pts) What is the salt value?
(25 pts) What is the password hashed with? Crypt? MD5? Something else? How do you know? (This may call for a little open source googling research.)
(25 pts) From within Unix, use the mkpasswd utility (mkpasswd
Guidance: General rubric: Grading is based on three fundamental targets: soundness (is the answer correct?), completeness (is the answer responsive and comprehensive?) and writing (is the writing of good quality?).
Read and respond to the questions in their entirety. Some of questions are multi-part.
I already completed 1st question I need rest of the answer and I my answer of 1st question is attached below:
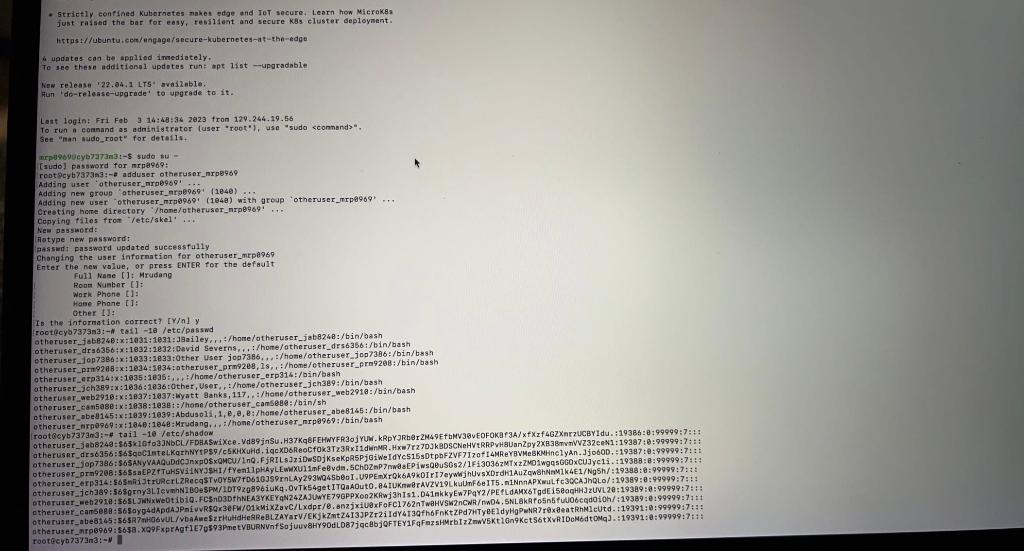
- Strictly cenfined Kubernetes makes edge and IoT secure, Learn hew Microk8s just rajsed the bar for easy, resilient and secure k8s eluster deployment. hctpst//ubuntu, cor/engageisecure-kubernetes-at-the-edge. 4. updates can be applied Imediately. To see these additianal updotes runt ept 1ist -upgradable Kew release "22,a4, 1.LT5" availebIe; Hun 'do-relense-upgrade' to upgrade to it. Lest login: Fri Feb 3.14:48:362623 fron 129.244.19.56 To run a connand as administrator (user "root"), use "sudo cconnands". see "man mudo_raot" for detallut mepelo9ueyb7ar3nit 5 sudo su - [sudo] password for mrpe969; reat9cyb7373n3:- adduser otheruser_nrpe969 Adding uset atheruser_nrpb969'... Adding new groug atheruser_arpb969- (1e4e) Adding new user otheruser_mrp69691 (1e48) with jreup otheruser_mrpe969+ .. Cresting hcre directory "Thoneyotheruser_nrpe969! .. Copying tiles fron "letelskel" ... lee passinerd: Hotype new passward: (anssand password updated suceessfully chariging the user information for otheruser_mepa> 69 Enter the new value, or press ENTER for the default FuIl Nane []t Mrudang Roun Nuaber []t Wark. Phene tis Haise phane []: Dther 114 In the information oorrect? [Y] y rootecyb7373n3:- eat l -18./etc/passud atheruser_jabe2\&8:x:1a31:1931:jeailey,r,7/hame/otheruser_jabB2 4B:/bin/bash otherusef_jop73ed:xi1633:1e33tother User jop73.86, . ,/hone/otheruser,jop7386:/bin/bssh otheruser_pri9288:x:1e94:1834;atheruser_prip2e8, 1s, i/home / otheruser_prn92e8:jbin/bash otheruser erpa14:x:1635:1e36: . i :/home/otheruser_erp 31s:/bin/bash atheruser_jch389:x:1036:1e36:0ther, User, :/ /home/otheruser_jch /B9:/hin/bash otheruser_web2916:xa2e37:1637; Wyatt 8anks, 117, :/hoee/otheruser_web2916:/bin/bash otheruser_can598e : x:1038:1638 : :/hone / otheruser_camSege //hin/sh. otheruser_abes145:x:1e39:1099: Abdusoli, 1, e, e, e:/hone/otheruser_abe8165:/bin/bash echeruser_nipog69:xi164e:1e48:Mrudang, . ihone/otheruser_mrpe969:/hin/bash irootocyb7373m3:-\#tail 10/ fetc/shadow otheraser_jch3a9:565grny3LIevmhN1D0eSPN/1DT929896iukq. OvTk54get ITQaAOuto, 84IUKnwBrAVZVI9Lkul otheruser_eeb291ai \$65LJWWWe0tibig. fCLnD3DthNEA3YKEYqN242AJUWYE79GPPXoo2KAwj3hIs1. D41nkkyEw? rootecyb7a73nat-4
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


