Answered step by step
Verified Expert Solution
Question
1 Approved Answer
(b) Analyze the following code in Figure Q2(b). #include void main() char place; char *systemcommand; place (char *)malloc (10), systemcommand= (char *)malloc (32); printf(Memory
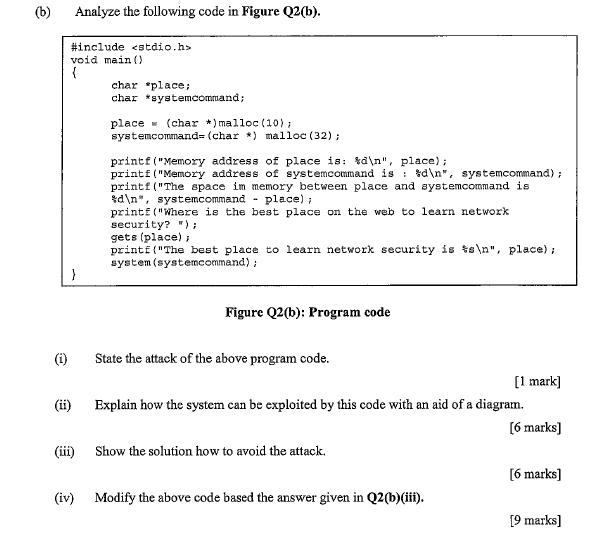
(b) Analyze the following code in Figure Q2(b). #include void main() char "place; char *systemcommand; place (char *)malloc (10), systemcommand= (char *)malloc (32); printf("Memory address of place is: %d ", place); printf("Memory address of systemcommand is %d ", systemcommand); printf("The space im memory between place and systemcommand is %d ", systemcommand place); printf("Where is the best place on the web to learn network security? "); gets (place); printf("The best place to learn network security is %s ", place); system (systemcommand); } Figure Q2(b): Program code (i) State the attack of the above program code. [1 mark] (ii) Explain how the system can be exploited by this code with an aid of a diagram. [6 marks] (iii) Show the solution how to avoid the attack. [6 marks] (iv) Modify the above code based the answer given in Q2(b)(iii). [9 marks]
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


