Answered step by step
Verified Expert Solution
Question
1 Approved Answer
BST Implementation errors An error in a BST implementation may result in a variety of problems. Ex: Key - related problems include: A node x
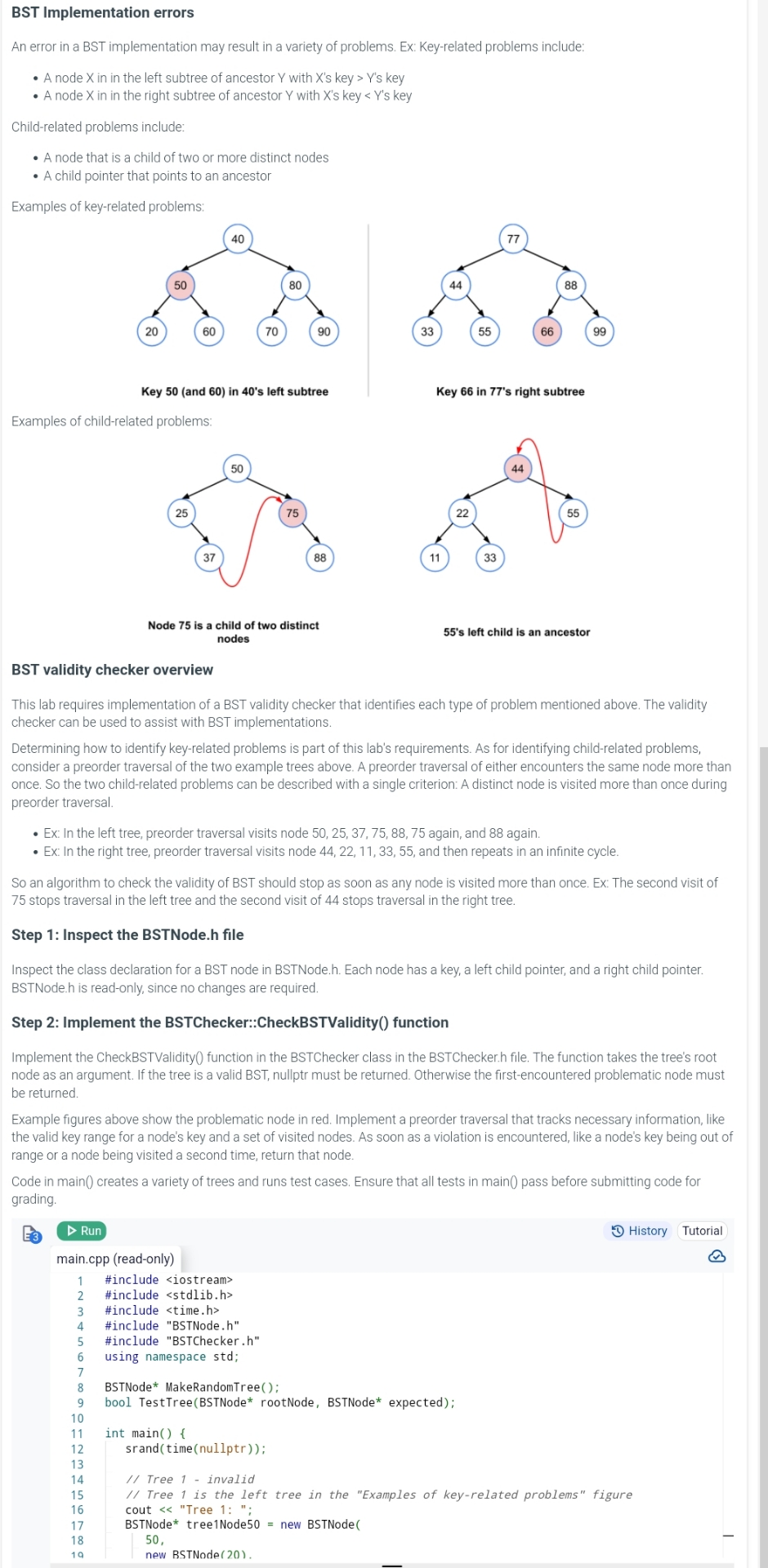
BST Implementation errors
An error in a BST implementation may result in a variety of problems. Ex: Keyrelated problems include:
A node in in the left subtree of ancestor with s key s key
A node in in the right subtree of ancestor with s key key
Childrelated problems include:
A node that a child two more distinct nodes
A child pointer that points ancestor
Examples keyrelater nrnhleme
Key left subtree
Key right subtree
Examples childrelated problems:
Node a child two distinct
nodes
left child ancestor
validity checker overview
This lab requires implementation a validity checker that identifies each type problem mentioned above. The validity checker can used assist with implementations.
Determining how identify keyrelated problems part this lab's requirements. for identifying childrelated problems, consider a preorder traversal the two example trees above. A preorder traversal either encounters the same node more than once. the two childrelated problems can described with a single criterion: A distinct node visited more than once during preorder traversal.
: the left tree, preorder traversal visits node again, and again.
: the right tree, preorder traversal visits node and then repeats infinite cycle
algorithm check the validity should stop soon any node visited more than once. : The second visit stops traversal the left tree and the second visit stops traversal the right tree.
Step : Inspect the BSTNode. file
Inspect the class declaration for a node BSTNode. Each node has a key, a left child pointer, and a right child pointer. BSTNode. readonly, since changes are required.
Step : Implement the BSTChecker::CheckBSTValidity function
Implement the CheckBSTValidity function the BSTChecker class the BSTChecker. file. The function takes the tree's root node argument. the tree a valid nullptr must returned. Otherwise the firstencountered problematic node must returned.
Example figures above show the problematic node red. Implement a preorder traversal that tracks necessary information, like the valid key range for a node's key and a set visited nodes. soon a violation encountered, like a node's key being out range a node being visited a second time, return that node.
Code main creates a variety trees and runs test cases. Ensure that all tests main pass before submitting code for grading.
Run
main.only
History
Tutorial
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


