c++ code please
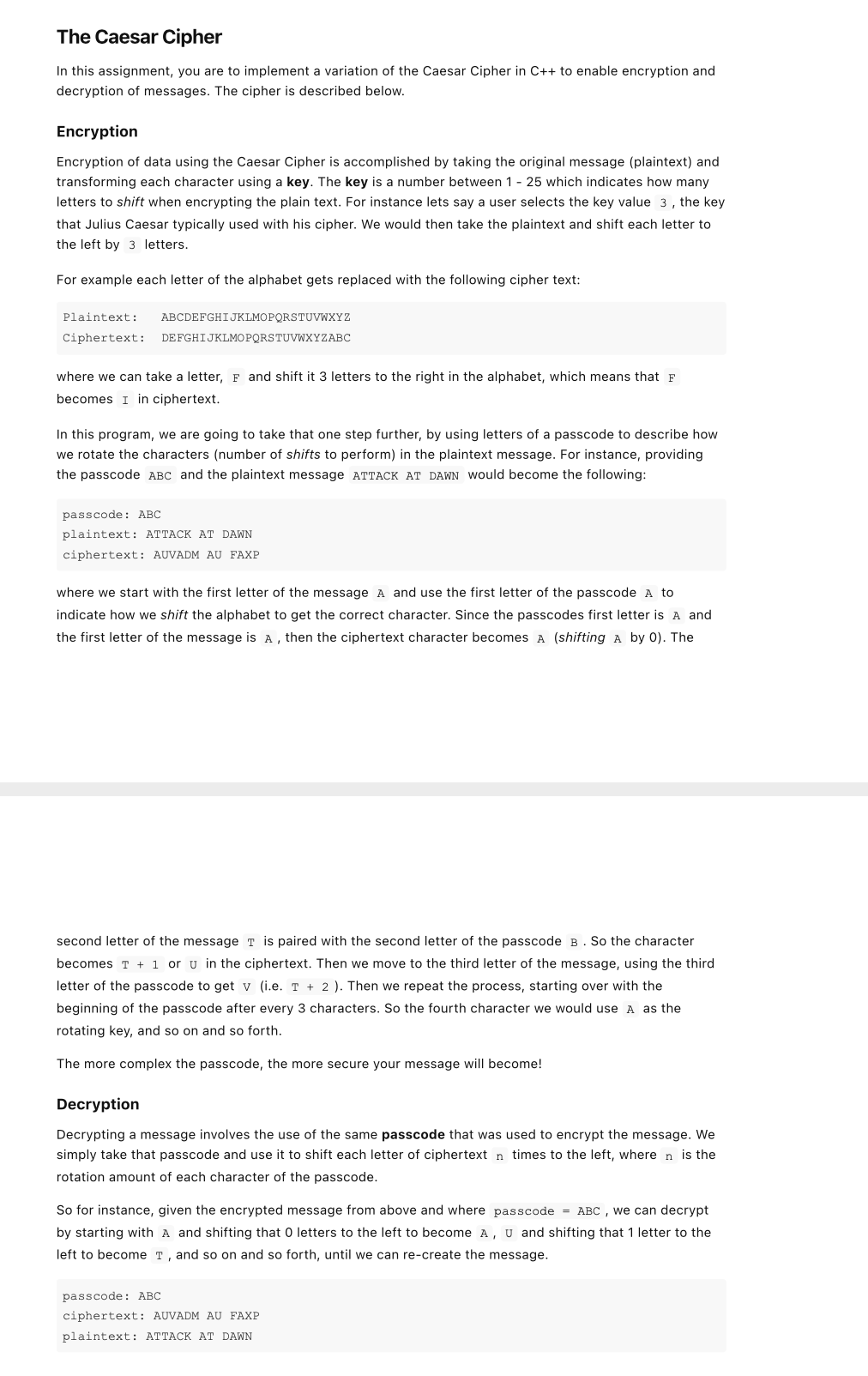
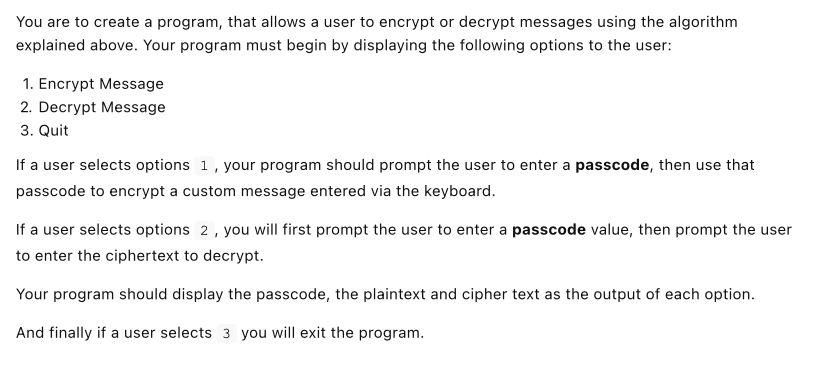

The Caesar Cipher In this assignment, you are to implement a variation of the Caesar Cipher in C++ to enable encryption and decryption of messages. The cipher is described below. Encryption Encryption of data using the Caesar Cipher is accomplished by taking the original message (plaintext) and transforming each character using a key. The key is a number between 1 - 25 which indicates how many letters to shift when encrypting the plain text. For instance lets say a user selects the key value 3, the key that Julius Caesar typically used with his cipher. We would then take the plaintext and shift each letter to the left by 3 letters. For example each letter of the alphabet gets replaced with the following cipher text: Plaintext: ABCDEFGHIJKLMOPQRSTUVWXYZ DEFGHIJKLMOPQRSTUVWXYZABC Ciphertext: where we can take a letter, F and shift it 3 letters to the right in the alphabet, which means that F becomes I in ciphertext. In this program, we are going to take that one step further, by using letters of a passcode to describe how we rotate the characters (number of shifts to perform) in the plaintext message. For instance, providing the passcode ABC and the plaintext message ATTACK AT DAWN would become the following: passcode: ABC plaintext: ATTACK AT DAWN ciphertext: AUVADM AU FAXP where we start with the first letter of the message A and use the first letter of the passcode A to indicate how we shift the alphabet to get the correct character. Since the passcodes first letter is A and the first letter of the message is A, then the ciphertext character becomes A (shifting A by 0). The second letter of the message is paired with the second letter of the passcode B. So the character becomes T + 1 or u in the ciphertext. Then we move to the third letter of the message, using the third letter of the passcode to get v i.e. T + 2 ). Then we repeat the process, starting over with the beginning of the passcode after every 3 characters. So the fourth character we would use A as the rotating key, and so on and so forth. The more complex the passcode, the more secure your message will become! Decryption Decrypting a message involves the use of the same passcode that was used to encrypt the message. We simply take that passcode and use it to shift each letter of ciphertext n times to the left, where n is the rotation amount of each character of the passcode. So for instance, given the encrypted message from above and where passcode = ABC , we can decrypt by starting with A and shifting that O letters to the left to become A, u and shifting that 1 letter to the left to become t, and so on and so forth, until we can re-create the message. passcode: ABC ciphertext: AUVADM AU FAXP plaintext: ATTACK AT DAWN You are to create a program, that allows a user to encrypt or decrypt messages using the algorithm explained above. Your program must begin by displaying the following options to the user: 1. Encrypt Message 2. Decrypt Message 3. Quit If a user selects options 1 , your program should prompt the user to enter a passcode, then use that passcode to encrypt a custom message entered via the keyboard. If a user selects options 2 , you will first prompt the user to enter a passcode value, then prompt the user to enter the ciphertext to decrypt. Your program should display the passcode, the plaintext and cipher text as the output of each option. And finally if a user selects 3 you will exit the program. Your Program must follow the following guidelines and adhere to the following criteria Your program must re-prompt the user for a list of options after every encrypted or decrypted message is completed. Your program must account for incorrect options entered by a user (you may assume the user will always enter a valid number). Your program must contain at least 3 functions . You must implement a function using pass by value o You must implement a function using pass by reference All functions must have a function prototype defined above main(), with the implementation defined below main(). You must validate the passcode according to the following: . Must be at least 1 letter Must only contain alpha characters (a - Z, A - Z). o If whitespace is included, you may ignore it (i.e. convert My Password to MyPassword to use in your encryption / decryption algorithm) If whitespace or punctuation is included in the message, you may ignore encrypting those characters. Only encrypt alpha characters (i.e. a - z and A - Z) The output of your encrypted message must be in ALL CAPS (as the examples below show)









