Answered step by step
Verified Expert Solution
Question
1 Approved Answer
C Programming LAB: In this lab, you are asked to complete similars.c program file which has been already given in LMS . In this program,
C Programming LAB: In this lab, you are asked to complete similars.c program file which has been already given in LMS In this program, there are four functions, namely, main, hashtext, strongsimilar, and weaksimilar. main function is already provided, and it is supposed to remain as it is you should not change it You are required to implement hashtext, strongsimilar, and weaksimilar functions.Here are the operations performed in main function:
An array of strings with name list with the size is created to hold name and surname data in namesurname format and the elements are read into it
An array of integers with name hashedvals is created to hold hashed values of name and and surname in unsigned integer format.
A twodimensional array of integers to keep the mapping of similarities between each name surname pair.
hashedvals array is initialize by calling hashtext function to calculate the hash values of full name and surname pair.
strongsimilar function is called to find the same names and fill the twodimensional array called same to keep the mapping of similarities.
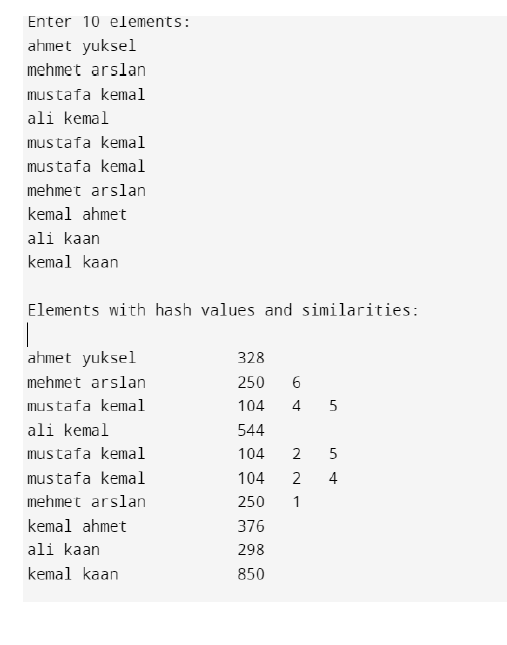
The name surname pairs, the calculated hash values and similarity mapping is printed on the standard output.
weaksimilar function is called to calculate the hash values of each name and surname separately, then build the similarity map using hash values.
The name surname pairs, and weakly similarity mapping is printed on the standard output.
Totalcharacters function calculates the total number of characters in each string and prints Task : Implement hashtext function.
unsigned int hashtext char list ;
A character pointer holding names and surnames is sent as an input, and the hash value of the input text is returned. During the calculation a basic formula is used as follows when the name is ali. The ascii code for a is for l is and for i is The function calculates the hash value by the following formula; hash
The algorithm should be applied to all symbols including whitespaces between name and surname. At the end mod of hash value should be returned.
hash hash mod Task : Implement strongsimilar function.
void strongsimilar int hvalMAXELEM int mapMAXELEMMAXELEM ;
Calculated hash values of all namessurnames pair are sent to the function. The function modifies and returns the map of exact matches. Exact matching of the entries is calculated only by using hashed values. Task : Implement weaksimilar function.
void weaksimilar char listMAXELEMSTRLENint mapMAXELEMMAXELEM ;
Array of names and surnames list is sent as input and previously calculated similarity map is sent as inputoutput parameter.
During the execution of the function strtok function is used to split names and surnames by using the space between them. To store the splitted names and surnames a threedimensional array is created. First dimension is same as the list in main function, second dimension is two either to point name string or surname string. Similarly, twodimensional array is created to keep hash values of names and surnames for each pair.
The function then calculates hash values of names and surnames for each pair by calling hashtext function. Once the hash values of all names and surnames are calculated the function updates the map array to mark the weak similarities either names or surnames are same For example;
ali kemal and mustafa kemal are weakly similar. They both are weakly similar to kemal ahmet.
Task : Implement printstringlengths function
printstringlengths, calculates the length of the each string while excluding spaces. Then print out with this format: ali kemal
Sample Run:
See the next page for sample run. I attached the sample runs Here is the similars.c program structure that needs to be completed: I will upload attach it
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


