Answered step by step
Verified Expert Solution
Question
1 Approved Answer
C2. Answer the following questions: C2.1 From the diagram below, consider yourself the administrator of below networks How to reduce the attack surface from Internet
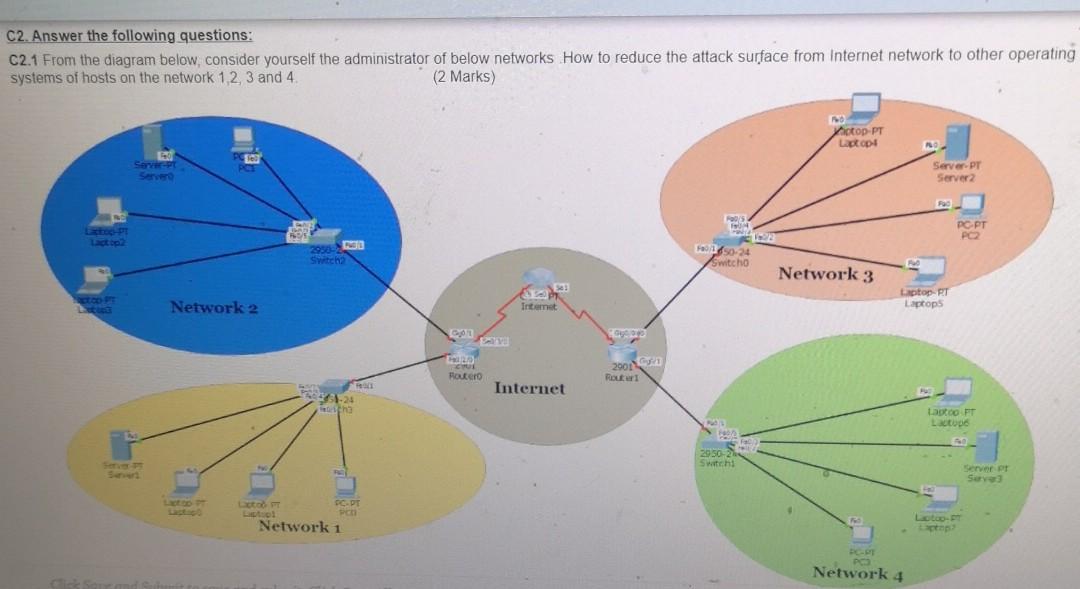
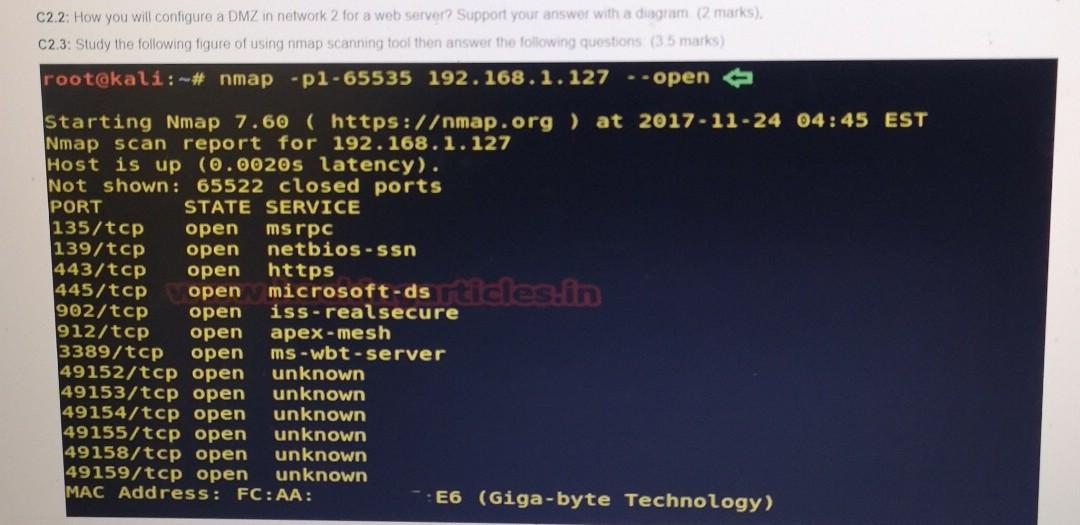
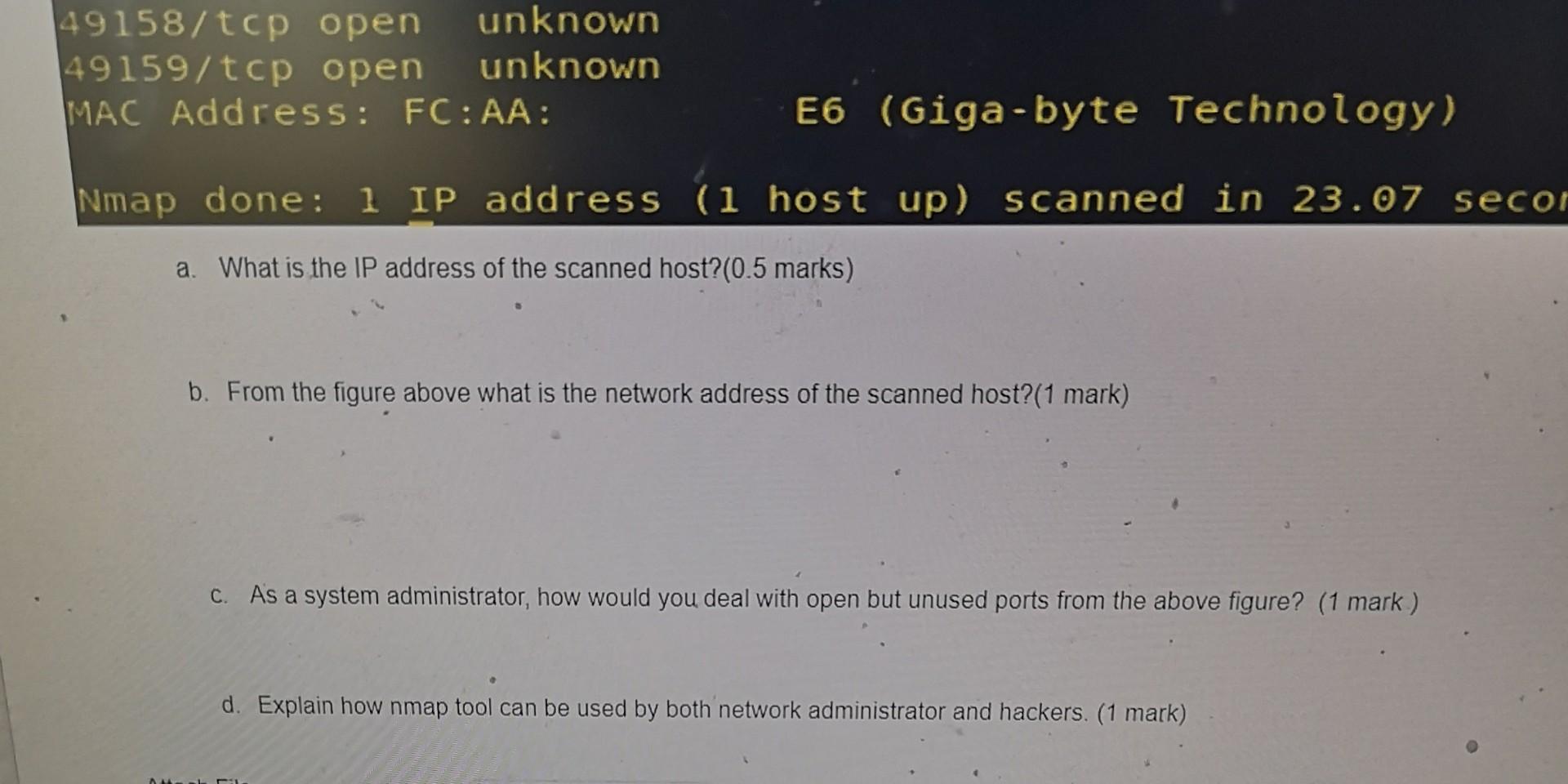
C2. Answer the following questions: C2.1 From the diagram below, consider yourself the administrator of below networks How to reduce the attack surface from Internet network to other operating systems of hosts on the network 1,2, 3 and 4. (2 Marks) Actop-PT Laptop Server PT Server2 10 PC PT 2950-2 Switch 650-24 Switcho Network 3 TOD Network 2 Laptop RT Laptops Internet Tea Houter 2001 Route Internet 1-24 ha Lagtoo FT Lactope 2950-2 Swatch Server or Serv pl Network 1 too. top Network 4 C2.2: How you will configure a DMZ in network 2 for a web server? Support your answer with a diagram (2 marks), C2.3: Study the following figure of using nmap scanning tool then answer the following questions (35 marks) root@kali:-# nmap -p1-65535 192.168.1.127 .- open Starting Nmap 7.60 ( https:/map.org ) at 2017-11-24 04:45 EST Nmap scan report for 192.168.1.127 Host is up (0.0020s latency). Not shown: 65522 closed ports PORT STATE SERVICE 135/tcp open ms rpc 139/tcp open netbios-san 443/tcp open https 445/tcp open microsoft-ds rticles.in 902/tcp open iss-realsecure 912/tcp open apex-mesh 3389/tcp open ms-wbt-server 49152/tcp open unknown 49153/tcp open unknown 49154/tcp open unknown 49155/tcp open unknown 49158/tcp open unknown 49159/tcp open unknown MAC Address: FC:AA: -E6 (Giga-byte Technology) 49158/tcp open unknown 49159/tcp open unknown MAC Address: FC:AA: E6 (Giga-byte Technology) Nmap done: 1 IP address (1 host up) scanned in 23.07 seco a. What is the IP address of the scanned host?(0.5 marks) b. From the figure above what is the network address of the scanned host?(1 mark) C. As a system administrator, how would you deal with open but unused ports from the above figure? (1 mark) d. Explain how nmap tool can be used by both network administrator and hackers. (1 mark) NV
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


