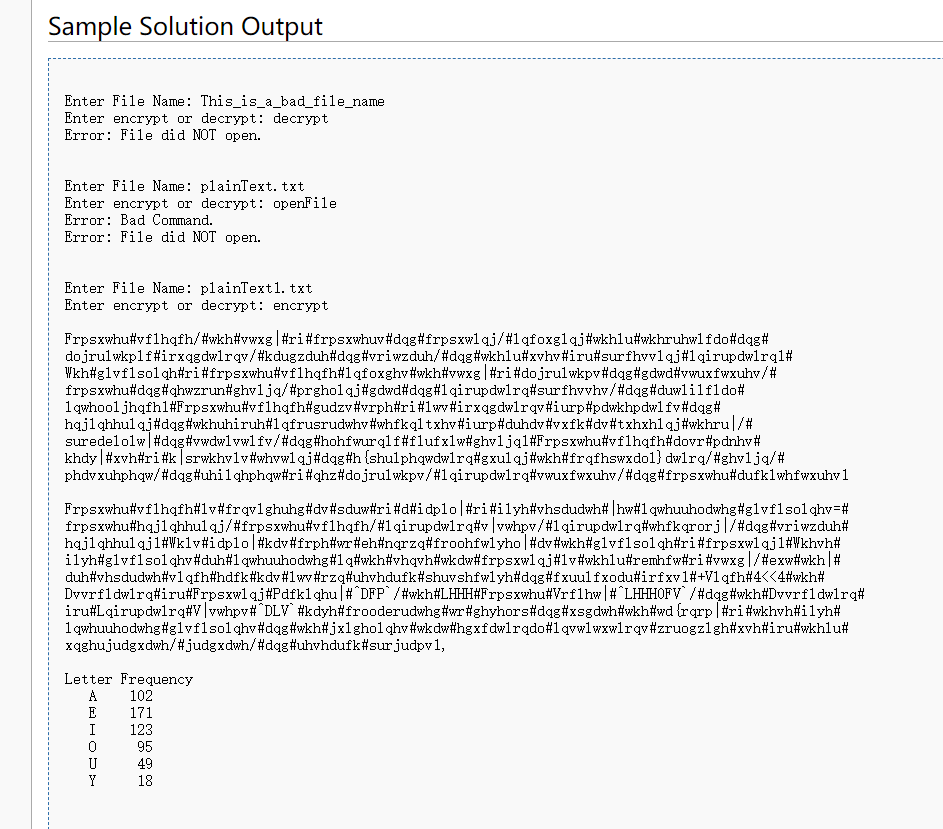
CaesarCipher Videos [edit] Introduction Hiding the meaning of messages by putting them in some kind of code is something we have all done, from the "coding rings" and secret symbols of childhood to the top secrecy of military and commercial establishments' secret data. In fact, some of the earliest uses of computers were for coding messages and for breaking the enemy's coded messages. Newer coding methods are among the most interesting research areas in computer science today. The Caesar Cipher One of the simplest examples of a substitution cipher is the Caesar Cipher, which is said to have been used by Julius Caesar to communicate with his army. Caesar is considered to be one of the first persons to have ever employed encryption for the sake of securing messages. Caesar decided that shifting each letter in the message would be his standard algorithm, and so he informed all of his generals of his decision, and was then able to send them secured messages. Using the Caesar Shift (3 to the right), the message, RETURNTOROME = would be encrypted as UHWXUQWRURPH In this example, 'R' = 'U','E' => 'H', and so on. Now, even if the enemy did intercept the message, it would be useless, since only Caesar' s generals could read it. The Assignment Write a program to implement the Caesar Cipher Problem Write a program that will ask the user to enter the name of a file. Your program should then ask the user to enter 'encrypt' or 'decrypt'. If the user enters anything else your program should print an error message and exit. If they entered 'encrypt' your program should open the file and encrypt it by shifting each character (including white space) 3 values to the right. If they entered 'decrypt' your program should open the file and decrypt it by shifting each character (including white space) 3 values to the left. If the file fails to open your program should print an error message and exit. The decrypted or encrypted message should be displayed on the screen and also written to an output file named "message" . Also report the frequency of the vowels (A,E,I,O,U, Y) in input message. Sample Solution Output Enter File Name: This_is_a_bad_file_name Enter encrypt or decrypt: decrypt Error: File did NOT open. Enter File Name: plaintext. txt Enter encrypt or decrypt: openFile Error: Bad Command. Error: File did NOT open. Enter File Name: plaintextl. txt Enter encrypt or decrypt: encrypt Frpsxwhu#vflhqfh/#wkh#vwxg|#ri#frpsxwhuv#dqg#frpsxwlqj/#1qfoxglqj #wkhlu#wkhruhwlf do#dqg# dojrulwkplf#irxqgdwlrqv/#kdugzduh#dag#vriwzduh/#dqg#wkhlu#xvhv#iru#surfhvvlqj#1 qirupdwlrq1# Wkh#glvilsol gh#ri#frpsxwhukvilhqfhf1qfpxght #wkh#vwxg| #ri#dojrulwkpy #dag#gdwdkywuxfwxuhy/# frpsxwhu#dqg#chwzrun#ghvljq/#prgholqj#gdwd#dqg#1qirupdwlrq#surfhvvhv/#dqg#duwlilfldo# 1 qwhooljhqfh1#Frpsxwhu#vflhqfh#gudzv#vrph#ri#1wv#irxqgdwlrq#iurp#pdwkhpdwlfv#dag# hajlqhhulqj#dqg#wkhuhiruh#1qfrusrudwhv#whfkqltxhv#iurp#duhdv#vxfk#dv#txhxhl qj#wkhru[/# suredelolw #dqg#vwdwlywlfv/#dqg#hohfwurqlf#flufxlw#ghvljq1#Frpsxwhu#vflhqfh#dovr#pdnhv# khdy | #xvh#ri #k|srwkhvlv#whywlqj#dqg#h(shulphqwdwlrq#gxulqj #wkh#frqfhswxdol} dwlrg/#ghvljq/# phdvxuhphqw/#dqg#uhilqhphqw#ri#qhz#dojrulwkpv/#1qirupdwlrq#vwuxfwxuhv/#dqg#frpsxwhu#dufklwhfwxuhv1 Frpsxwhu#vf1hqfh#1v#frqvlghuhg#dv#sduw#ri#d#idplo #ri#ilyh#vhsdudwh#|hw#1 qwhuuhodwhg#glvf1solghy=# frpsxwhu#hqjlqhhulqj/#frpsxwhu#vflhqfh/#1 qirupdwlrq#v|vwhpv/#1 qirupdwlrq#whfkqrorj//#dqg#vriwzduh# hajiqhhulqj1#Wklv#idplo #kdy#frph#wr#eh#narzq#froohfwlyho | #dv#wkh#glvflsol qh#ri#frpsxwlqj1#Wkhvh# ilyh#glvflsolchv#duh#1 qwhuuhodwhg#1 q#wkh#vhqvh#wkdw#frpsxwlqj#1v#wkhlu#remhfw#ri#vwxg|/#exw#wkh|# duh#vhsdudwh#v1qfh#hdfk#kdv#1w#rzq#uhvhdufk#shuvshfwlyh#dqg#fxuulfxodu#irfxv1#+V1qfh#4








