Can anyone provide the solution by using c++?
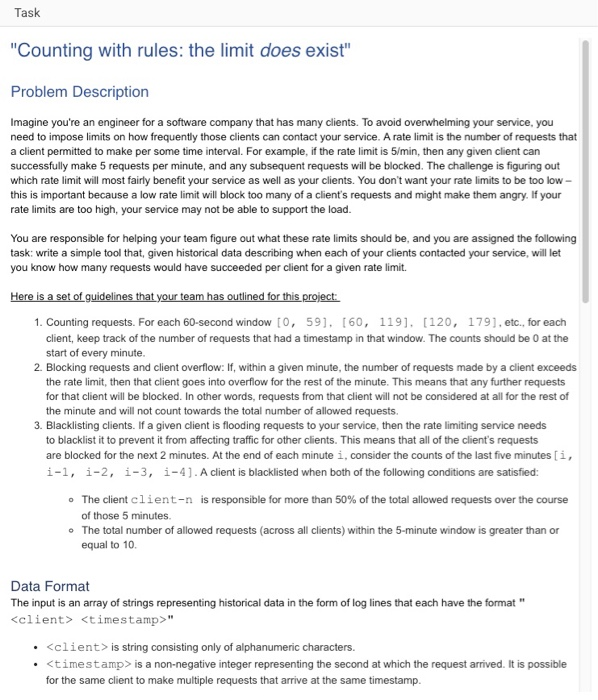
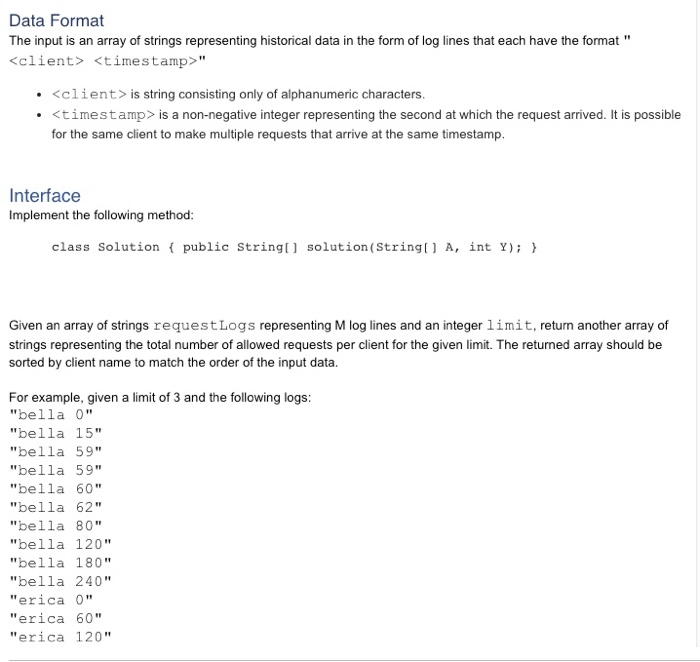
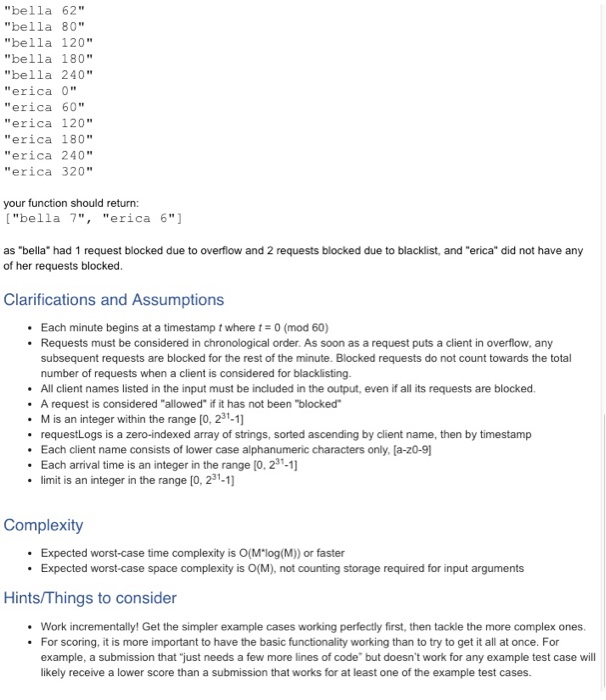
Task Counting with rules: the limit does exist" Problem Description Imagine you're an engineer for a software company that has many clients. To avoid overwhelming your service, you need to impose limits on how frequently those clients can contact your service. A rate limit is the number of requests that a client permitted to make per some time interval. For example, if the rate limit is 5/min, then any given client can successfully make 5 requests per minute, and any subsequent requests will be blocked. The challenge is figuring out which rate limit will most fairly benefit your service as well as your clients. You don't want your rate limits to be too low- this is important because a low rate limit will block too many of a client's requests and might make them angry. If your rate limits are too high, your service may not be able to support the load You are responsible for helping your team figure out what these rate limits should be, and you are assigned the following task: write a simple tool that, given historical data describing when each of your clients contacted your service, will let you know how many requests would have succeeded per client for a given rate limit. 1. Counting requests. For each 60-second window [0, 59], [60, 119. [120, 1791, etc., for each client, keep track of the number of requests that had a timestamp in that window. The counts should be 0 at the start of every minute 2. Blocking requests and client overflow: If, within a given minute, the number of requests made by a client exceeds the rate limit, then that client goes into overflow for the rest of the minute. This means that any further requests for that client will be blocked. In other words, requests from that client will not be considered at all for the rest of the minute and will not count towards the total number of allowed requests. 3. Blacklisting clients. If a given client is flooding requests to your service, then the rate limiting service needs to blacklist it to prevent it from affecting traffic for other clients. This means that all of the client's requests are blocked for the next 2 minutes. At the end of each minute i, consider the counts of the last five minutes [i, i-1, i-2, i-3, i-4].A client is blacklisted when both of the following conditions are satisfied: The client cl ient-n of those 5 minutes. is responsible for more than 50% of the total allowed requests over the course o o The total number of allowed requests (across all clients) within the 5-minute window is greater than or equal to 10. Data Format The input is an array of strings representing historical data in the form of log lines that each have the format
" . is string consisting only of alphanumeric characters. * is a non-negative integer representing the second at which the request arrived. It is possible for the same client to make multiple requests that arrive at the same timestamp Task Counting with rules: the limit does exist" Problem Description Imagine you're an engineer for a software company that has many clients. To avoid overwhelming your service, you need to impose limits on how frequently those clients can contact your service. A rate limit is the number of requests that a client permitted to make per some time interval. For example, if the rate limit is 5/min, then any given client can successfully make 5 requests per minute, and any subsequent requests will be blocked. The challenge is figuring out which rate limit will most fairly benefit your service as well as your clients. You don't want your rate limits to be too low- this is important because a low rate limit will block too many of a client's requests and might make them angry. If your rate limits are too high, your service may not be able to support the load You are responsible for helping your team figure out what these rate limits should be, and you are assigned the following task: write a simple tool that, given historical data describing when each of your clients contacted your service, will let you know how many requests would have succeeded per client for a given rate limit. 1. Counting requests. For each 60-second window [0, 59], [60, 119. [120, 1791, etc., for each client, keep track of the number of requests that had a timestamp in that window. The counts should be 0 at the start of every minute 2. Blocking requests and client overflow: If, within a given minute, the number of requests made by a client exceeds the rate limit, then that client goes into overflow for the rest of the minute. This means that any further requests for that client will be blocked. In other words, requests from that client will not be considered at all for the rest of the minute and will not count towards the total number of allowed requests. 3. Blacklisting clients. If a given client is flooding requests to your service, then the rate limiting service needs to blacklist it to prevent it from affecting traffic for other clients. This means that all of the client's requests are blocked for the next 2 minutes. At the end of each minute i, consider the counts of the last five minutes [i, i-1, i-2, i-3, i-4].A client is blacklisted when both of the following conditions are satisfied: The client cl ient-n of those 5 minutes. is responsible for more than 50% of the total allowed requests over the course o o The total number of allowed requests (across all clients) within the 5-minute window is greater than or equal to 10. Data Format The input is an array of strings representing historical data in the form of log lines that each have the format " . is string consisting only of alphanumeric characters. * is a non-negative integer representing the second at which the request arrived. It is possible for the same client to make multiple requests that arrive at the same timestamp









