Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Can someone help me write the project? it's very difficult for me, I didnt have any idea for this. Background Caesar cipher The Caesar cipher




Can someone help me write the project? it's very difficult for me, I didnt have any idea for this.
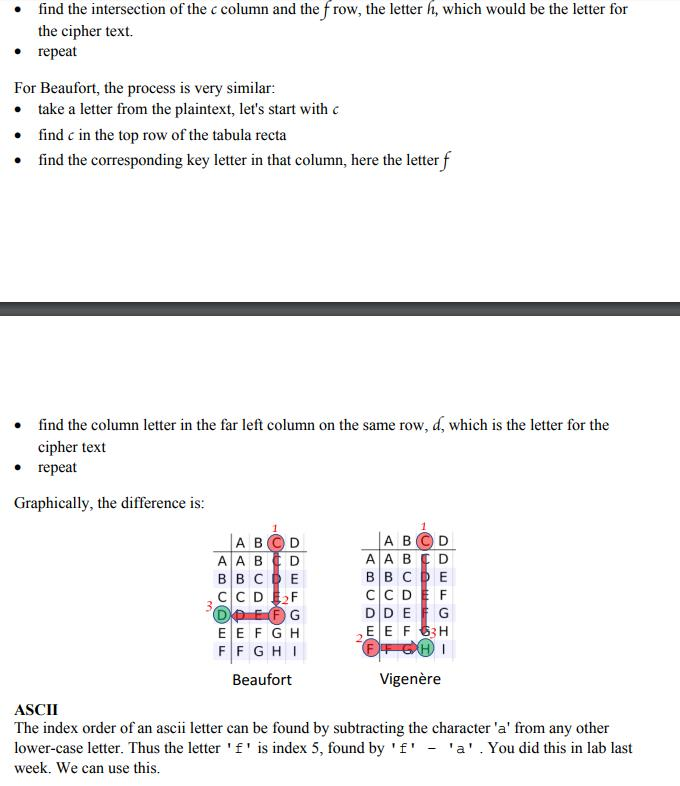
Background Caesar cipher The Caesar cipher is named after Julius Caesar who used this type of encryption to keep his military communications secret. There are a couple of ways to think about how this works, but one is the idea of a string rotation. A single left rotation of a string moves all the letters down (to the left) one index, and the letter at the front is moved to the end of the string. A rotation of 3 does this three times. For example left rotation left rotation left rotation abcdefg bcdefga cde fgab de fgabc A Caesar cipher left rotates the alphabet being used by some number, say a rotation of 3, and aligns the rotated alphabet with the original alphabet. The number of rotations is a fixed number is called the key. The plain-text is your original message; the cipher-text is the encrypted message. We create a rotation of the original alphabet, below a left-3-rotation, and align the letters of the original alphabet and the rotated alphabet Here is the complete mapping for a left rotation of three Original alphabet left rotation 3 alphabet: defghijklmnopqrstuvwxyzabc abcdefghijklmnopgrstuvwxyz To encrypt a message simply substitute the plain-text letters with the corresponding rotated letters. For example, here is an encryption of "the quick brown fox jumps over the lazy dog" using our three-rot cipher (case is ignored and spaces are preserved, not the case for the project!!) Plaintext the quick brown fox jumps over the lazy dog Ciphertext: wkh txlfn eurz ira mxpsv ryhu wkh odbc grj To decrypt the message simply reverse the process. Beaufort and Vigenre cipher It turns out the Caesar cypher can be cracked pretty easily. Two improved versions of a Caesar cipher are the Beaufort http://practicalcryptography.com/ciphers/classical-era/beaufort/ and Background Caesar cipher The Caesar cipher is named after Julius Caesar who used this type of encryption to keep his military communications secret. There are a couple of ways to think about how this works, but one is the idea of a string rotation. A single left rotation of a string moves all the letters down (to the left) one index, and the letter at the front is moved to the end of the string. A rotation of 3 does this three times. For example left rotation left rotation left rotation abcdefg bcdefga cde fgab de fgabc A Caesar cipher left rotates the alphabet being used by some number, say a rotation of 3, and aligns the rotated alphabet with the original alphabet. The number of rotations is a fixed number is called the key. The plain-text is your original message; the cipher-text is the encrypted message. We create a rotation of the original alphabet, below a left-3-rotation, and align the letters of the original alphabet and the rotated alphabet Here is the complete mapping for a left rotation of three Original alphabet left rotation 3 alphabet: defghijklmnopqrstuvwxyzabc abcdefghijklmnopgrstuvwxyz To encrypt a message simply substitute the plain-text letters with the corresponding rotated letters. For example, here is an encryption of "the quick brown fox jumps over the lazy dog" using our three-rot cipher (case is ignored and spaces are preserved, not the case for the project!!) Plaintext the quick brown fox jumps over the lazy dog Ciphertext: wkh txlfn eurz ira mxpsv ryhu wkh odbc grj To decrypt the message simply reverse the process. Beaufort and Vigenre cipher It turns out the Caesar cypher can be cracked pretty easily. Two improved versions of a Caesar cipher are the Beaufort http://practicalcryptography.com/ciphers/classical-era/beaufort/ andStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


