Can you dram Use Case diagram for Facebook (UML)? Also, can you explain that diagram?
Based on information given below for reference:
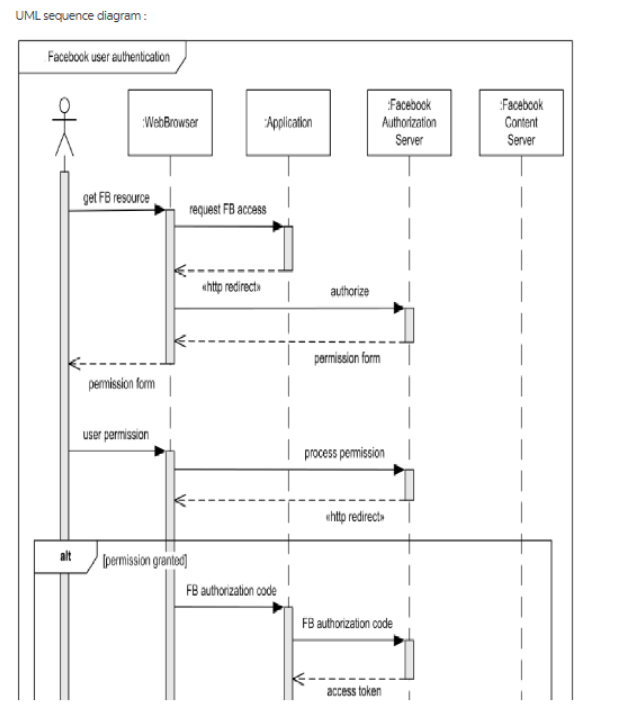
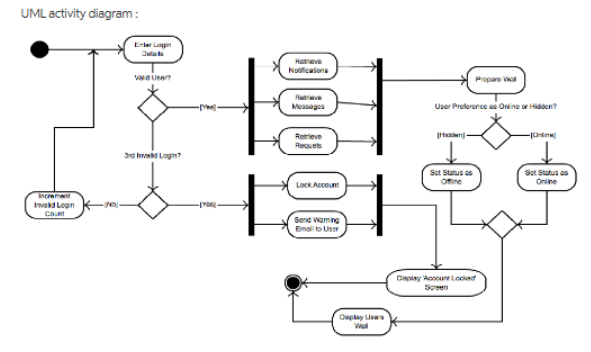
UML sequence diagram : Facebook user authenticalion Facebook Authorization Server Facebook Content Server WebBrowser Application get FB resource request FB access ehttp redirectu authorize permission form permission fom user permission process pemission ehttp redirect alt permission graniod) FB authorization code FB authorization code access token Overview: The sequence diagram depicts the activity steps of: Getting application access on browser Providing permission form to user on the browser Getting login details from user and sending to Facebook authorization server Sending authorization code to authorization server and getting access token to Facebook content server If there is no permission or authorization, no resources will be shared with the actor user on the web- browser. Detailed explanation: 1. Facebook authorization system uses OAuth 2.0 framework where the web application requests the Facebook resources on the Facebook user's behalf from the Facebook content server and authorization is saved as authorization token. 2. The user request the Facebook web application from the WebBrowser, the browser redirect the user to Facebook http:// URL which have the Facebook home page. 3. When the user submits authorization request, web browser sends the request to Authorization Server which returns the permission form. The permission form is displayed on the WebBrowser to the user. 4. User provides the permission details on the WebBrowser, which is sent to Facebook's Authorization Server. If permission granted: The browser generates an authorisation code for the user and sends the 5.1 same to Authorization Server, which generates the access token for the user on the WebBrowser. The browser application sends the request to Content Server after getting an authorization token. The Content Server sends the protected contents to application, which is further sent to WebBrowser application. The user gets his/her protected contents on the browser. If the permission not granted: The token is not generated for the user. The authorization is not 5.2 completed and the end user does not get the Facebook resource and contents on the browser. UML activity diagram : Erler Lon Rareve Noilicaiona Popare V Measeges User Preference es Onine or Hidden Hasen Retrieve Recuets d Iad Lognt Sot Status as Ofine Sot Status as Onine Lock Account Increment Ived Logn Cant Send Waming Emal to User Diplay Anonune Locint Screen Ceplay Uss UML Activity Diagram: The given activity diagram shows the flow of the Facebook user login use case. Overview: The user logs into the application after providing the Login Details. If the details are valid, the user is redirected to application else the user is asked to provide the details again till 3 attempts. After 3 attempts the account gets locked. Detailed explanation: 1. The user provides the Login Details. 2. Login Details are validated and if the details are correct, the user is redirected to the application. 3. The user can retrieve : Messages Notifications Requests Available on his/her account. 4. At background, user's wall is prepared as per the settings in user preferences. 4.1 If the user preferences are set to keep the status hidden, user's status is displayed as offline on the application. 4.2 If user preferences are set to make the status online, User's status is displayed as online on the application. 5. As per settings of above step, the user's wall is displayed to other users. 6. On the other hand, if the provided User Details at step 1 are not valid, the login counter is incremented and user is redirected to input the User Details again. 6.1 If the user provides valid details in 2nd or 3rd attempt, the user is redirected to application and steps 2 to 5 are repeated for the user. 6.2 If the user does not provide the valid details even in 3 attempts, the Account is locked along with a warning email to the user. 'Account Locked' is displayed on the user interface










