Question: Case Study: Information Security Risk Assessment In this case study assignment, you will perform a quantitative risk analysis for the company network shown below. Write
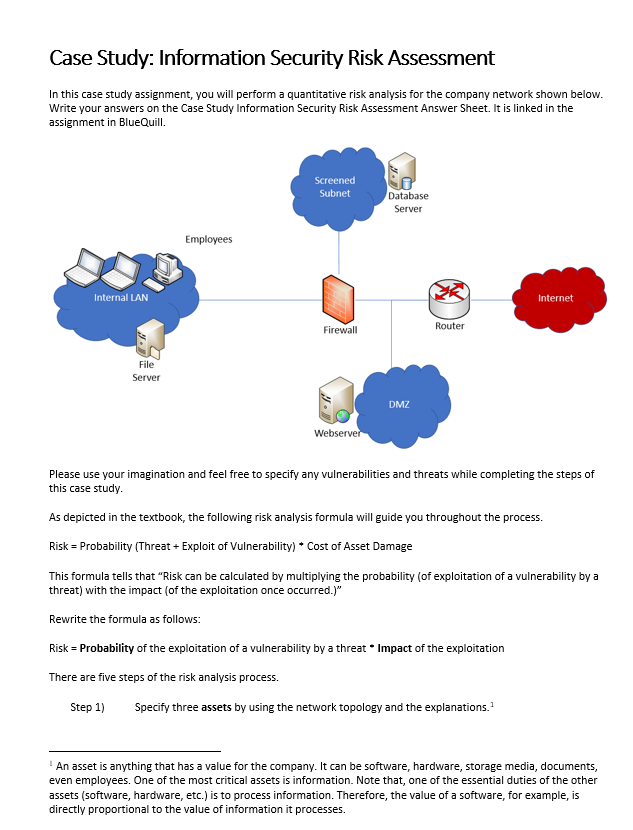
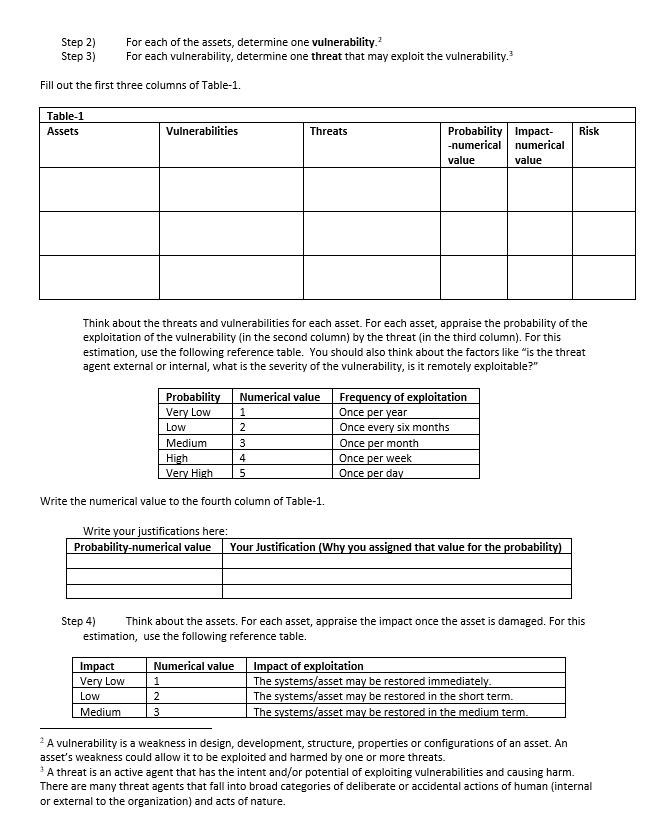
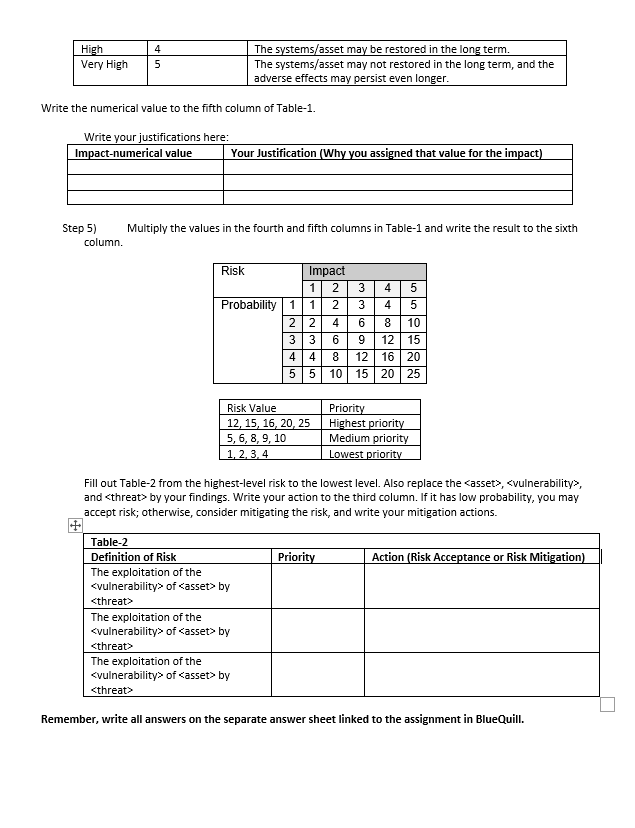
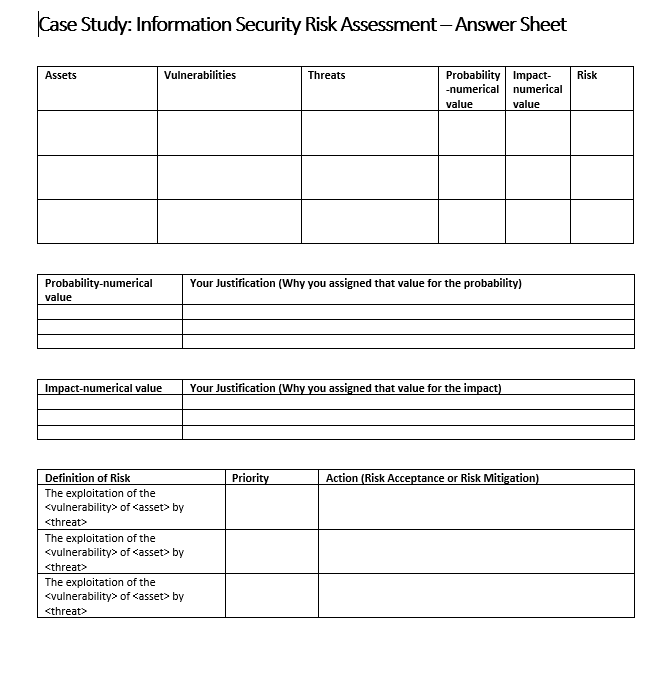
Case Study: Information Security Risk Assessment In this case study assignment, you will perform a quantitative risk analysis for the company network shown below. Write your answers on the Case Study Information Security Risk Assessment Answer Sheet. It is linked in the assignment in BlueQuill. Screened Subnet Database Server Employees Internal LAN Internet Router Firewall File Server DMZ Webserver Please use your imagination and feel free to specify any vulnerabilities and threats while completing the steps of this case study As depicted in the textbook, the following risk analysis formula will guide you throughout the process. Risk = Probability (Threat + Exploit of Vulnerability) * Cost of Asset Damage This formula tells that "Risk can be calculated by multiplying the probability (of exploitation of a vulnerability by a threat) with the impact of the exploitation once occurred.)" Rewrite the formula as follows: Risk = Probability of the exploitation of a vulnerability by a threat Impact of the exploitation There are five steps of the risk analysis process. Step 1) Specify three assets by using the network topology and the explanations. An asset is anything that has a value for the company. It can be software, hardware, storage media, documents, even employees. One of the most critical assets is information. Note that, one of the essential duties of the other assets (software, hardware, etc.) is to process information. Therefore, the value of a software, for example, is directly proportional to the value of information it processes. Step 2) Step 3) For each of the assets, determine one vulnerability? For each vulnerability, determine one threat that may exploit the vulnerability. Fill out the first three columns of Table-1. Table-1 Assets Vulnerabilities Threats Risk Probability Impact- -numerical numerical value value Think about the threats and vulnerabilities for each asset. For each asset, appraise the probability of the exploitation of the vulnerability (in the second column) by the threat (in the third column). For this estimation, use the following reference table. You should also think about the factors like "is the threat agent external or internal, what is the severity of the vulnerability, is it remotely exploitable?" Probability Very Low Low Medium High Very High Numerical value 1 2 3 4 5 Frequency of exploitation Once per year Once every six months Once per month Once per week Once per day Write the numerical value to the fourth column of Table-1. Write your justifications here: Probability-numerical value Your Justification (Why you assigned that value for the probability) Step 4) Think about the assets. For each asset, appraise the impact once the asset is damaged. For this estimation, use the following reference table. Impact Very Low Low Medium Numerical value 1 2 3 Impact of exploitation The systems/asset may be restored immediately. The systems/asset may be restored in the short term. The systems/asset may be restored in the medium term. 2 A vulnerability is a weakness in design, development, structure, properties or configurations of an asset. An asset's weakness could allow it to be exploited and harmed by one or more threats. A threat is an active agent that has the intent and/or potential of exploiting vulnerabilities and causing harm. There are many threat agents that fall into broad categories of deliberate or accidental actions of human (internal or external to the organization) and acts of nature. High Very High 4 5 The systems/asset may be restored in the long term. The systems/asset may not restored in the long term, and the adverse effects may persist even longer. Write the numerical value to the fifth column of Table-1. Write your justifications here: Impact-numerical value Your Justification (Why you assigned that value for the impact) Step 5) column. Multiply the values in the fourth and fifth columns in Table-1 and write the result to the sixth Risk lielis Probability 1 2 3 | Impact 1 2 3 4 5 1 2 3 4 5 2 4 6 8 10 3 6 9 12 15 4 8 12 16 20 10 15 20 25 Risk Value 12, 15, 16, 20, 25 5, 6, 8, 9, 10 1.2.3.4 Priority Highest priority Medium priority Lowest priority Fill out Table-2 from the highest-level risk to the lowest level. Also replace the casset>, by your findings. Write your action to the third column. If it has low probability, you may accept risk; otherwise, consider mitigating the risk, and write your mitigation actions. Priority Action (Risk Acceptance or Risk Mitigation) Table-2 Definition of Risk The exploitation of the by The exploitation of the of by The exploitation of the of by Remember, write all answers on the separate answer sheet linked to the assignment in Blue Quill. Case Study: Information Security Risk Assessment - Answer Sheet Assets Vulnerabilities Threats Risk Probability Impact- -numerical numerical value value Probability-numerical value Your Justification (Why you assigned that value for the probability) Impact-numerical value Your Justification (Why you assigned that value for the impact) Priority Action (Risk Acceptance or Risk Mitigation) Definition of Risk The exploitation of the of by The exploitation of the of by The exploitation of the of by Case Study: Information Security Risk Assessment In this case study assignment, you will perform a quantitative risk analysis for the company network shown below. Write your answers on the Case Study Information Security Risk Assessment Answer Sheet. It is linked in the assignment in BlueQuill. Screened Subnet Database Server Employees Internal LAN Internet Router Firewall File Server DMZ Webserver Please use your imagination and feel free to specify any vulnerabilities and threats while completing the steps of this case study As depicted in the textbook, the following risk analysis formula will guide you throughout the process. Risk = Probability (Threat + Exploit of Vulnerability) * Cost of Asset Damage This formula tells that "Risk can be calculated by multiplying the probability (of exploitation of a vulnerability by a threat) with the impact of the exploitation once occurred.)" Rewrite the formula as follows: Risk = Probability of the exploitation of a vulnerability by a threat Impact of the exploitation There are five steps of the risk analysis process. Step 1) Specify three assets by using the network topology and the explanations. An asset is anything that has a value for the company. It can be software, hardware, storage media, documents, even employees. One of the most critical assets is information. Note that, one of the essential duties of the other assets (software, hardware, etc.) is to process information. Therefore, the value of a software, for example, is directly proportional to the value of information it processes. Step 2) Step 3) For each of the assets, determine one vulnerability? For each vulnerability, determine one threat that may exploit the vulnerability. Fill out the first three columns of Table-1. Table-1 Assets Vulnerabilities Threats Risk Probability Impact- -numerical numerical value value Think about the threats and vulnerabilities for each asset. For each asset, appraise the probability of the exploitation of the vulnerability (in the second column) by the threat (in the third column). For this estimation, use the following reference table. You should also think about the factors like "is the threat agent external or internal, what is the severity of the vulnerability, is it remotely exploitable?" Probability Very Low Low Medium High Very High Numerical value 1 2 3 4 5 Frequency of exploitation Once per year Once every six months Once per month Once per week Once per day Write the numerical value to the fourth column of Table-1. Write your justifications here: Probability-numerical value Your Justification (Why you assigned that value for the probability) Step 4) Think about the assets. For each asset, appraise the impact once the asset is damaged. For this estimation, use the following reference table. Impact Very Low Low Medium Numerical value 1 2 3 Impact of exploitation The systems/asset may be restored immediately. The systems/asset may be restored in the short term. The systems/asset may be restored in the medium term. 2 A vulnerability is a weakness in design, development, structure, properties or configurations of an asset. An asset's weakness could allow it to be exploited and harmed by one or more threats. A threat is an active agent that has the intent and/or potential of exploiting vulnerabilities and causing harm. There are many threat agents that fall into broad categories of deliberate or accidental actions of human (internal or external to the organization) and acts of nature. High Very High 4 5 The systems/asset may be restored in the long term. The systems/asset may not restored in the long term, and the adverse effects may persist even longer. Write the numerical value to the fifth column of Table-1. Write your justifications here: Impact-numerical value Your Justification (Why you assigned that value for the impact) Step 5) column. Multiply the values in the fourth and fifth columns in Table-1 and write the result to the sixth Risk lielis Probability 1 2 3 | Impact 1 2 3 4 5 1 2 3 4 5 2 4 6 8 10 3 6 9 12 15 4 8 12 16 20 10 15 20 25 Risk Value 12, 15, 16, 20, 25 5, 6, 8, 9, 10 1.2.3.4 Priority Highest priority Medium priority Lowest priority Fill out Table-2 from the highest-level risk to the lowest level. Also replace the casset>, by your findings. Write your action to the third column. If it has low probability, you may accept risk; otherwise, consider mitigating the risk, and write your mitigation actions. Priority Action (Risk Acceptance or Risk Mitigation) Table-2 Definition of Risk The exploitation of the by The exploitation of the of by The exploitation of the of by Remember, write all answers on the separate answer sheet linked to the assignment in Blue Quill. Case Study: Information Security Risk Assessment - Answer Sheet Assets Vulnerabilities Threats Risk Probability Impact- -numerical numerical value value Probability-numerical value Your Justification (Why you assigned that value for the probability) Impact-numerical value Your Justification (Why you assigned that value for the impact) Priority Action (Risk Acceptance or Risk Mitigation) Definition of Risk The exploitation of the of by The exploitation of the of by The exploitation of the of by







