choose any topic from the first pic
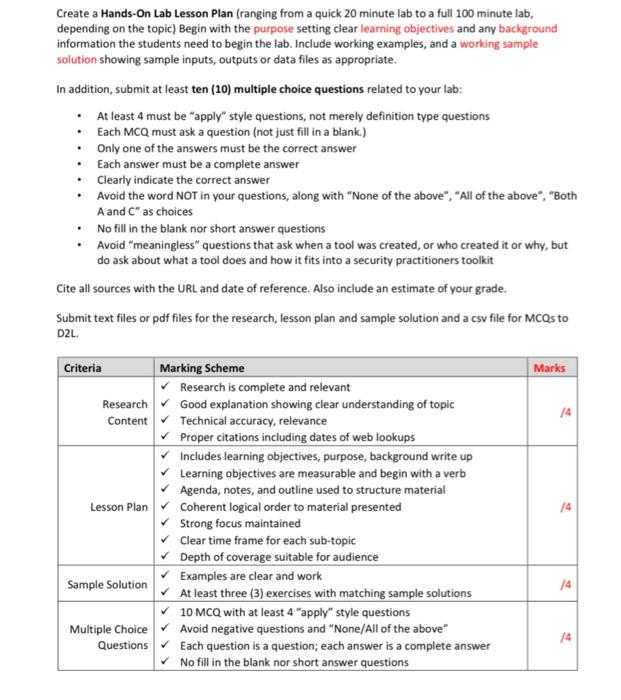
Prepare a Security Lab Lesson Plan on one of the following computer Security Tools. Most of these tools are in the Kali Linux Tools. You need to choose a topic and get confirmation by your instructor before starting to work on it. # Task Student 1. Aircrack-ng suite and Fern Wifi Cracker 2. Armitage Interface to Metasploit Framework 3. Bettercap 4. Burp Suite 5. Crunch 6. DIRB 7. Fluxion 8. FindMyHash 9. HT-Hack or Pixie WPS 10. John the Ripper 11. JoomScan + Skipfish + WPscan 12. SQL 13. King Phisher 14. Kismet 15. Lynis 16. Machanger 17. Maltego 18. mitmProxy 19. nc Netcat 20. Ncrack 21. Nessus 22. Nikto 23. Nmap 24. OWASP-ZAP 25. SET Social-Engineer Toolkit 26. Snort 27. SQLMap 28. SSLsplit 29. SSL Strip 30. THC-Hydra 31. Trace Route and Wireshark 32. WhatWeb Create a Hands-On Lab Lesson Plan (ranging from a quick 20 minute lab to a full 100 minute lab, depending on the topic) Begin with the purpose setting clear learning objectives and any background information the students need to begin the lab. Include working examples, and a working sample solution showing sample inputs, outputs or data files as appropriate. In addition, submit at least ten (10) multiple choice questions related to your lab: At least 4 must be "apply" style questions, not merely definition type questions Each MCQ must ask a question (not just fill in a blank.) Only one of the answers must be the correct answer Each answer must be a complete answer Clearly indicate the correct answer Avoid the word NOT in your questions, along with "None of the above", "All of the above", "Both A and C" as choices No fill in the blank nor short answer questions Avoid "meaningless" questions that ask when a tool was created, or who created it or why, but do ask about what a tool does and how it fits into a security practitioners toolkit Cite all sources with the URL and date of reference. Also include an estimate of your grade. Submit text files or pdf files for the research, lesson plan and sample solution and a csv file for MCQs to D2L. Marks 14 14 Criteria Marking Scheme Research is complete and relevant Research Good explanation showing clear understanding of topic Content Technical accuracy, relevance Proper citations including dates of web lookups Includes learning objectives, purpose, background write up Learning objectives are measurable and begin with a verb Agenda, notes, and outline used to structure material Lesson Plan Coherent logical order to material presented Strong focus maintained Clear time frame for each sub-topic Depth of coverage suitable for audience Sample Solution At least three (3) exercises with matching sample solutions Examples are clear and work 10 MCQ with at least 4 "apply" style questions Multiple Choice Avoid negative questions and "None/All of the above" Questions Each question is a question; each answer is a complete answer No fill in the blank nor short answer questions 14 14