Answered step by step
Verified Expert Solution
Question
1 Approved Answer
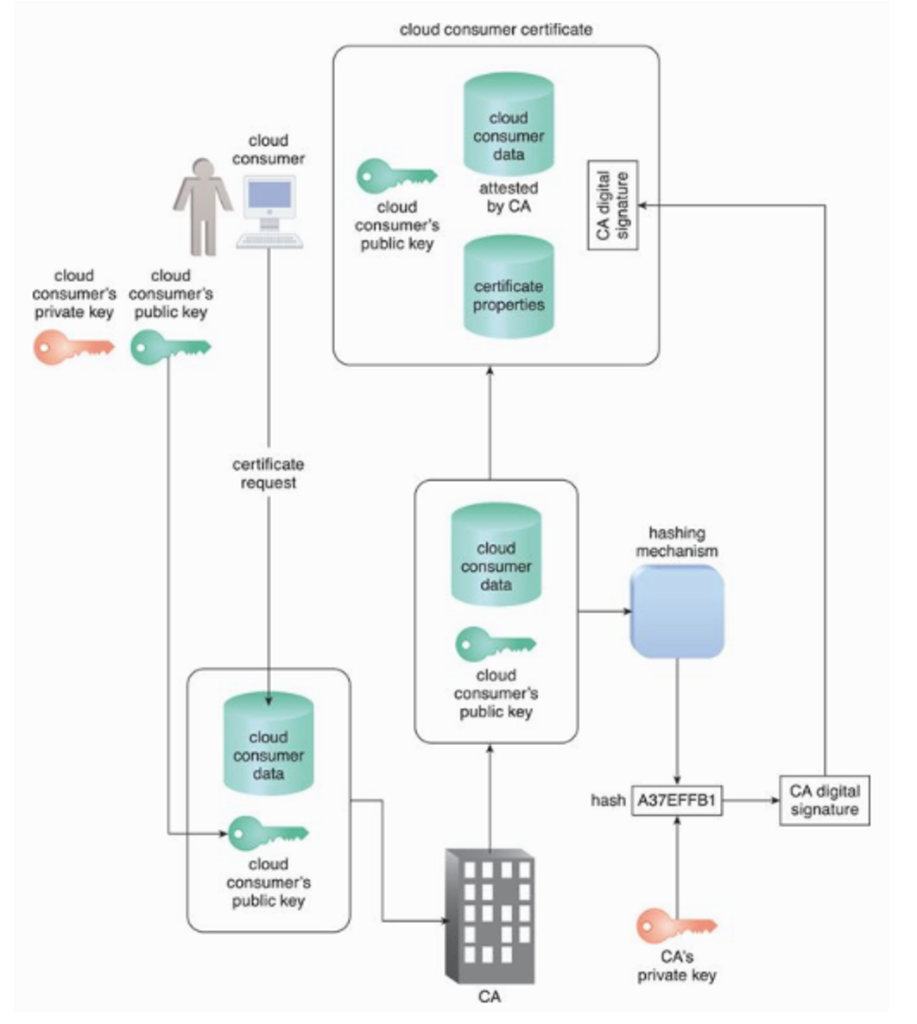
Cloud Security Fundamental What is a security mechanism used to counter a malicious intermediary? With reference to picture below, why does CA need to encrypt
Cloud Security Fundamental
- What is a security mechanism used to counter a malicious intermediary?
- With reference to picture below, why does CA need to encrypt the hash message with its private key (CAs private key)? What would happen if CA encrypted the hash with its public key?
- Is a cloud consumers public key used to encrypt cloud consumer data? If yes, explain why does a consumer need to do that? If not, what is this public key for?
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


