CODE IN PYTHON!!!
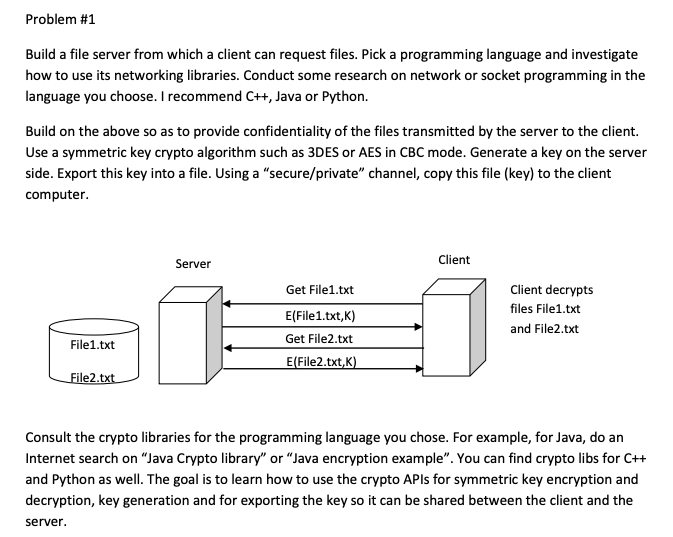
Problem #1 Build a file server from which a client can request files. Pick a programming language and investigate how to use its networking libraries. Conduct some research on network or socket programming in the language you choose. I recommend C++, Java or Python. Build on the above so as to provide confidentiality of the files transmitted by the server to the client. Use a symmetric key crypto algorithm such as 3DES or AES in CBC mode. Generate a key on the server side. Export this key into a file. Using a "secure/private" channel, copy this file (key) to the client computer. Server Client Get File1.txt E(File1.txt,K) Get File2.txt E(File2.txt,K) Client decrypts files File1.txt and File2.txt File1.txt File2.txt Consult the crypto libraries for the programming language you chose. For example, for Java, do an Internet search on "Java Crypto library" or Java encryption example". You can find crypto libs for C++ and Python as well. The goal is to learn how to use the crypto APls for symmetric key encryption and decryption, key generation and for exporting the key so it can be shared between the client and the server Problem #1 Build a file server from which a client can request files. Pick a programming language and investigate how to use its networking libraries. Conduct some research on network or socket programming in the language you choose. I recommend C++, Java or Python. Build on the above so as to provide confidentiality of the files transmitted by the server to the client. Use a symmetric key crypto algorithm such as 3DES or AES in CBC mode. Generate a key on the server side. Export this key into a file. Using a "secure/private" channel, copy this file (key) to the client computer. Server Client Get File1.txt E(File1.txt,K) Get File2.txt E(File2.txt,K) Client decrypts files File1.txt and File2.txt File1.txt File2.txt Consult the crypto libraries for the programming language you chose. For example, for Java, do an Internet search on "Java Crypto library" or Java encryption example". You can find crypto libs for C++ and Python as well. The goal is to learn how to use the crypto APls for symmetric key encryption and decryption, key generation and for exporting the key so it can be shared between the client and the server







