Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Conduct research on a technical (information systems related) topic of your choice. Task 1: Find a tech topic (should be information technology/information systems related)

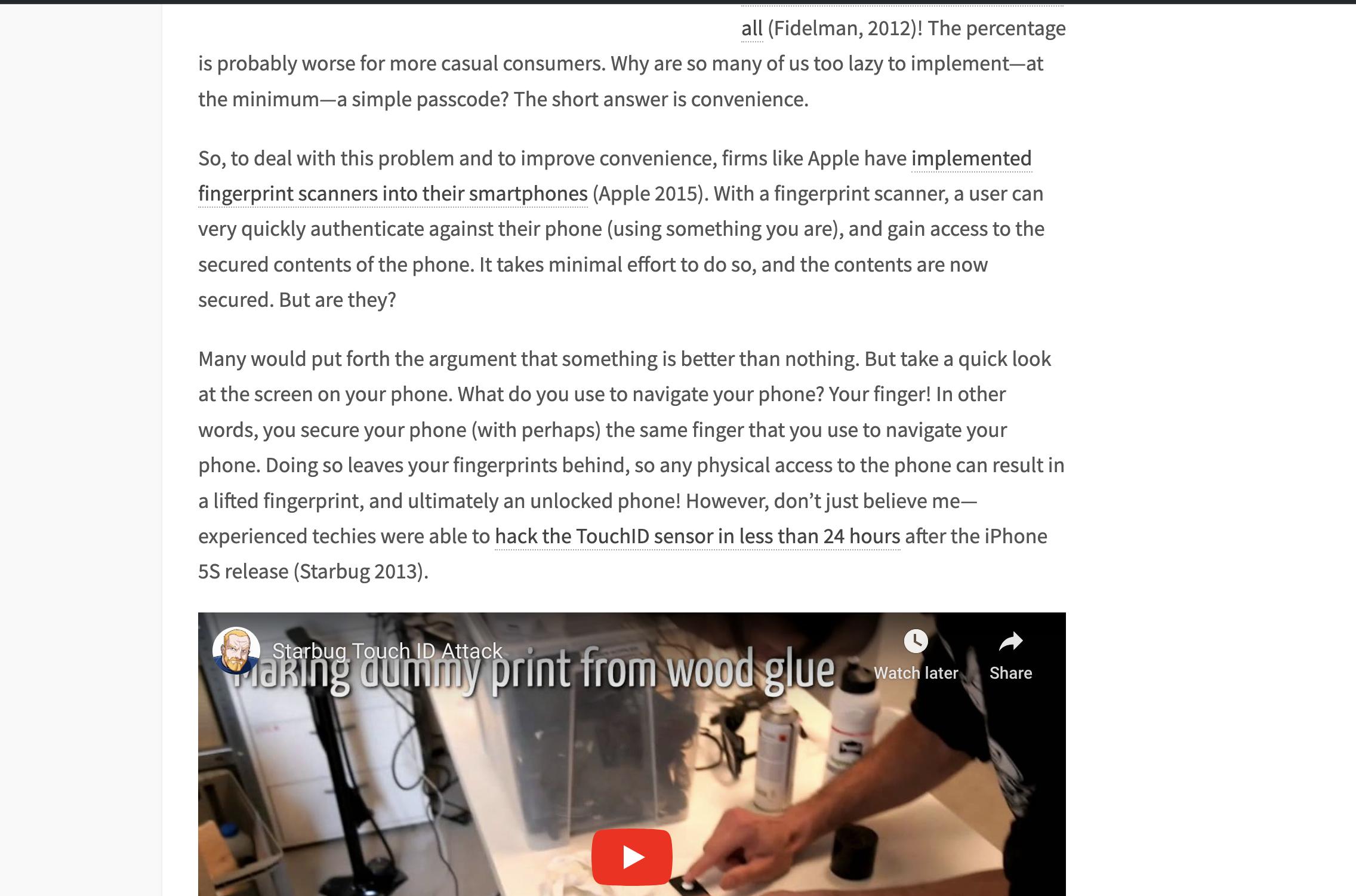
Conduct research on a technical (information systems related) topic of your choice. Task 1: Find a tech topic (should be information technology/information systems related) that you think is interesting and relevant for the class! 2. Task 2: As you conduct your research on the topic, you will find useful articles, videos, websites that provide valuable source material. a. Provide us with at least 2 references (typically website research, but it can be traditional print material). Use a standard citation format. b. Find an image that you think will go along well with your write up. Tell us why you felt this image was relevant. c. Also tell us where you found the image (the website / URL) d. Share with us at least 1 link to a video related to the tech topic. The video should be from YouTube or Vimeo. 3. Task 3: Write a 1-2-page summary of your tech talk using the supplied template document (12-point font, single-spaced, 1" margins). Include in your write-up: a. Why did you choose this topic including why is it important and relevant? b. List the important points about the topic. Use bullet points when appropriate. My Tech Talk Topic: Hacking Fingerprint Scanners! Authentication is an important topic that has gained significant attention in the past couple of years. There are three common factors used to authenticate with a device or service (Valacich and Schneider, 2016). These include: 1. What you know (e.g., a password) 2. What you have (e.g., a token, key card) 3. What you are (e.g., fingerprint, retina scan) We have always had usernames and passwords (authentication method #1 above), but other factors of authentication have recently gained popularity because of advancements in technology. Also, passwords have gained a lot of negative attention because all of the problems we have heard about with passwords being stolen. For example, one can easily search the web for information about stolen passwords on LinkedIn, Sony, Zappos, Adobe, etc., the list goes on and on. Unfortunately, when a username and password list are stolen, it takes very little time and effort to match passwords-including those that are encrypted-with their unencrypted counterparts. In other words, it is my opinion that passwords may be nearing the maximum of their usefulness, at least in their current incarnation. http://www.bitcuantico.com/2014/12/05/symantec- soluciones-en-seguridad-para-smartphones/ Now, let's take the password problem and apply it to a piece of technology many of us use every all (Fidelman, 2012)! The percentage is probably worse for more casual consumers. Why are so many of us too lazy to implement-at the minimum-a simple passcode? The short answer is convenience. So, to deal with this problem and to improve convenience, firms like Apple have implemented fingerprint scanners into their smartphones (Apple 2015). With a fingerprint scanner, a user can very quickly authenticate against their phone (using something you are), and gain access to the secured contents of the phone. It takes minimal effort to do so, and the contents are now secured. But are they? Many would put forth the argument that something is better than nothing. But take a quick look at the screen on your phone. What do you use to navigate your phone? Your finger! In other words, you secure your phone (with perhaps) the same finger that you use to navigate your phone. Doing so leaves your fingerprints behind, so any physical access to the phone can result in a lifted fingerprint, and ultimately an unlocked phone! However, don't just believe me- experienced techies were able to hack the TouchID sensor in less than 24 hours after the iPhone 5S release (Starbug 2013). Starbug Touch ID Making dummy print from wood glue Watch later Share Watch on YouTube Now, Apple was one of the first firms to gain notoriety regarding fingerprint scanning, but it would be foolish to believe that any of their competitors are any safer. So what does this mean for you? Use some kind of security-something is better than nothing! Whether you use passcodes, patterns, or fingerprints, it does not matter. Please just don't use slide to unlock! Of course, a powerful way to address the problem is by combining factors, often known as two- factor authentication. However, we'll save that topic for another day... List of References: 1. Apple, "About Touch ID security on iPhone and iPad," Apple Support, May 5, 2015. (https://support.apple.com/en-us/HT5949). 2. Fidelman, M. "The Latest Infographics: Mobile Business Statistics For 2012," Forbes, May 2, (http://www.forbes.com/sites/markfidelman/2012/05/02/the-latest-infographics- 2012. . mobile-business-statistics-for-2012/) 3. "Starbug's Touch ID Attack," YouTube, Sept. 25, 2013. (https://youtu.be/DJvgiMX1pv4). 4. Valacich, J., and Schneider, C. "Information Systems Today: Managing in the Digital World (CH10: Securing Information Systems)," 7th Edition. Pearson Education, 2016. Advorticomontr
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


