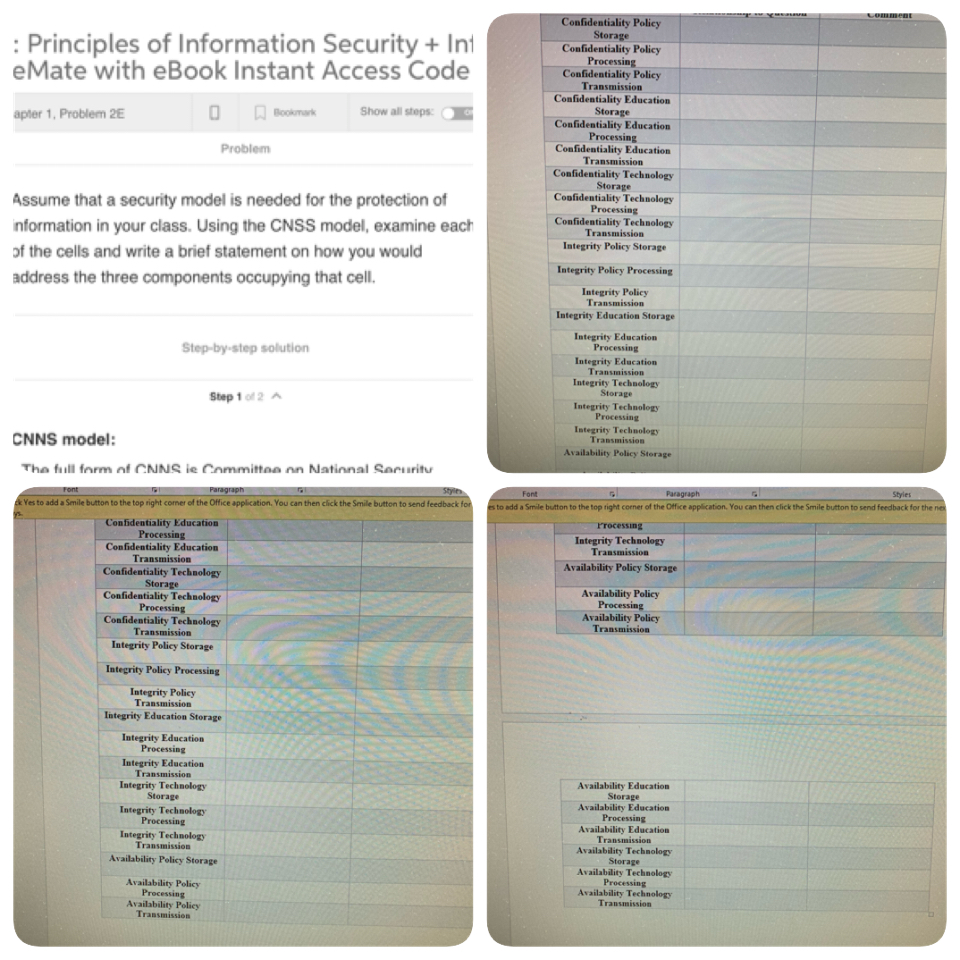
Confidentiality Policy Storage Confidentiality Policy Processing Confidentiality Policy Transmission Confidentiality Education Storage Confidentiality Education Processing Confidentiality Education Principles of Information Security+Int eMate with eBook Instant Access Code apter 1, Problem 2E Bookmark Show all steps: Problem Assume that a security model is needed for the protection of nformation in your class. Using the CNSS model, examine each of the cells and write a brief statement on how you would address the three components occupying that cell. Confidentiality Technology Storage Confidentiality Technology rocessing Confidentiality Technology Transmission Integrity Policy Storage Integrity Policy Processing Integrity Policy Transmission Integrity Education Storage Integrity Education Step-by-step solution Integrity Education Transmission Integrity Technology Storage Integrity Technology Step 1 of 2A CNNS model: Integrity Technology Transmission Availability Policy Storage The full form of CNNS le Committoa on National Saeuritu Yes to add a Smile button to the top right comer of the Office application, You can then click the Smile button to send feedback f es to add a Smile buton to the top right corner of the Office application, You can then click the Smile button to send feedback for the Confidentiality Education Processing Confidentiality Education Transmission Confidentiality Technology rrocessing Integrity Technology Transmission Confidentiality Technology Processing Confidentiality Technology Availability Policy Storage Availability Policy Availability Policy Transmission Integrity Policy Storage Integrity Policy Processing Integrity Policy Integrity Education Storage Integrity Education Integrity Education Transmission Integrity Technology Availability Education Storage Availability Education Processing Availability Education Transmission Availability Technology Storage Availability Technology Processing Availability Technology Transmission Integrity Technology Processing Integrity Technology Transmissiorn Availability Policy Storage Availability Policy Availability Policy Confidentiality Policy Storage Confidentiality Policy Processing Confidentiality Policy Transmission Confidentiality Education Storage Confidentiality Education Processing Confidentiality Education Principles of Information Security+Int eMate with eBook Instant Access Code apter 1, Problem 2E Bookmark Show all steps: Problem Assume that a security model is needed for the protection of nformation in your class. Using the CNSS model, examine each of the cells and write a brief statement on how you would address the three components occupying that cell. Confidentiality Technology Storage Confidentiality Technology rocessing Confidentiality Technology Transmission Integrity Policy Storage Integrity Policy Processing Integrity Policy Transmission Integrity Education Storage Integrity Education Step-by-step solution Integrity Education Transmission Integrity Technology Storage Integrity Technology Step 1 of 2A CNNS model: Integrity Technology Transmission Availability Policy Storage The full form of CNNS le Committoa on National Saeuritu Yes to add a Smile button to the top right comer of the Office application, You can then click the Smile button to send feedback f es to add a Smile buton to the top right corner of the Office application, You can then click the Smile button to send feedback for the Confidentiality Education Processing Confidentiality Education Transmission Confidentiality Technology rrocessing Integrity Technology Transmission Confidentiality Technology Processing Confidentiality Technology Availability Policy Storage Availability Policy Availability Policy Transmission Integrity Policy Storage Integrity Policy Processing Integrity Policy Integrity Education Storage Integrity Education Integrity Education Transmission Integrity Technology Availability Education Storage Availability Education Processing Availability Education Transmission Availability Technology Storage Availability Technology Processing Availability Technology Transmission Integrity Technology Processing Integrity Technology Transmissiorn Availability Policy Storage Availability Policy Availability Policy







