Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Consider an attacker who aims to compromise a university's server to gain unauthorized access to sensitive data, disrupt operations, and potentially steal intellectual property. The
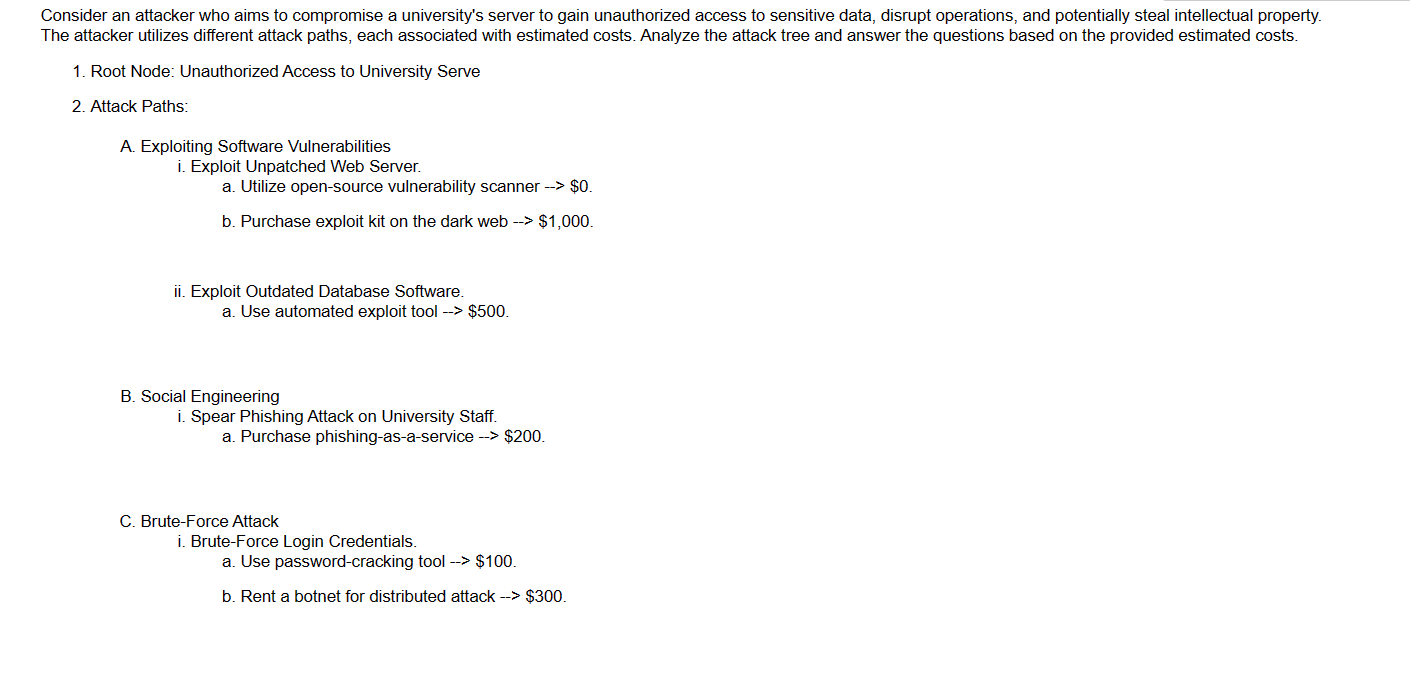
Consider an attacker who aims to compromise a university's server to gain unauthorized access to sensitive data, disrupt operations, and potentially steal intellectual property.
The attacker utilizes different attack paths, each associated with estimated costs. Analyze the attack tree and answer the questions based on the provided estimated costs.
Root Node: Unauthorized Access to University Serve
Attack Paths:
A Exploiting Software Vulnerabilities
i Exploit Unpatched Web Server.
a Utilize opensource vulnerability scanner $
b Purchase exploit kit on the dark web $
ii Exploit Outdated Database Software.
a Use automated exploit tool $
B Social Engineering
i Spear Phishing Attack on University Staff.
a Purchase phishingasaservice
C BruteForce Attack
i BruteForce Login Credentials.
a Use passwordcracking tool $
b Rent a botnet for distributed attack $
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


