Question: Consider an operating system that uses hardware support for paging to provide virtual memory to applications. (a) (i) Explain how the hardware and operating system
Consider an operating system that uses hardware support for paging to provide virtual memory to applications. (a) (i) Explain how the hardware and operating system support for paging combine to prevent one process from accessing another's memory. [3 marks] (ii) Explain how space and time overheads arise from use of paging, and how the Translation Lookaside Buffer (TLB) mitigates the time overheads. [3 marks] (b) Consider a system with a five level page table where each level in the page table is indexed by 9 bits and pages are 4 kB in size. A TLB is provided that is indexed by the first 57 bits of the address provided by the process, and achieves a 90% hit rate. A main memory access takes 40 ns while an access to the TLB takes 10 ns. The maximum memory read bandwidth is 100 GB/s. (i) What is the effective memory access latency? [4 marks] (ii) A colleague suggests replacing the system above with one that provides 80 GB/s memory read bandwidth and main memory access latency of 30 ns. Explain whether you should accept the replacement or not, and why. [4 marks] (c) A creative engineer suggests structuring the TLB so that not all the bits of the presented address need match to result in a hit. Suggest how this might be achieved, and what might be the costs and benefits of doing so. [6 marks]
(a) Describe two quantitative and two qualitative techniques for analysing the usability of a software product. [4 marks] (b) Compare the costs and benefits of the quantitative techniques. [6 marks] (c) Compare the costs and benefits of the qualitative techniques. [6 marks] (d) If restricted to a single one of these techniques when designing a new online banking system, which would you choose and why? (a) Suppose that women who live beyond the age of 80 outnumber men in the same age group by three to one. How much information, in bits, is gained by learning that a person who lives beyond 80 is male? [2 marks] (b) Consider n discrete random variables, named X1, X2, . . . , Xn, of which Xi has entropy H(Xi), the largest being H(XL). What is the upper bound on the joint entropy H(X1, X2, . . . , Xn) of all these random variables, and under what condition will this upper bound be reached? What is the lower bound on the joint entropy H(X1, X2, . . . , Xn)? [3 marks] (c) If discrete symbols from an alphabet S having entropy H(S) are encoded into blocks of length n symbols, we derive a new alphabet of symbol blocks S n . If the occurrence of symbols is independent, then what is the entropy H(S n ) of this new alphabet of symbol blocks? [2 marks] (d) Consider an asymmetric communication channel whose input source is the binary alphabet X = {0, 1} with probabilities {0.5, 0.5} and whose outputs Y are also this binary alphabet {0, 1}, but with asymmetric error probabilities. Thus an input 0 is flipped with probability ?, but an input 1 is flipped with probability ?, giving this channel matrix p (i) Give the probabilities of both outputs, p(Y = 0) and p(Y = 1). [2 marks] (ii) Give all the values of (?, ?) that would maximise the capacity of this channel, and state what that capacity then would be. [3 marks] (iii) Give all the values of (?, ?) that would minimise the capacity of this channel, and state what that capacity then would be. [3 marks] (e) In order for a variable length code having N codewords with bit lengths 1 mark] (f ) The information in continuous signals which are strictly bandlimited (lowpass or bandpass) is quantised, in that such continuous signals can be completely represented by a finite set of discrete samples. Describe two theorems about how discrete samples suffice for exact reconstruction of continuous bandlimited signals, even at all the points between the sampled values. [4 mark (a) A two state Markov process emits the letters {A, B, C, D, E} with the probabilities shown for each state. Changes of state can occur when some of the symbols are generated, as indicated by the arrows. 4.2 Information sources with memory We will wish to consider sources with memory, so we also consider Markov processes. Our four event process (a symbol is generated on each edge) is shown graphically together with a two state Markov process for the alphabet fA, B, C, D, Eg in gure 17. We can then solve for the state occupancy using ow equations (this example is trivial). ess with states fS 1; S2; : : :Sng, with transition probabilities pi(j) being the probability of moving from state Si to state Sj (with the emission of some symbol). First we can dene the entropy of each state in the normal manner:
Hi = X j pi(j) log2 pi(j) and then the entropy of the system to be the sum of these individual state entropy values weighted with the state occupancy (calculated from the ow equations):
Pipi(j) log pi(j) (45) Clearly for a single state, we have the entropy of the memoryless source. 4.3 The Source Coding theorem Often we wish to eciently represent the symbols generated by some source. We shall consider encoding the symbols as binary digits. 19 (i) What are the state occupancy probabilities? [1 mark] (ii) What is the probability of the letter string AD being emitted? [1 mark] (iii) What is the entropy of State 1, what is the entropy of State 2, and what is the overall entropy of this symbol generating process? [5 marks] (b) A fair coin is secretly flipped until the first head occurs. Let X denote the number of flips required. The flipper will truthfully answer any "yes-no" questions about his experiment, and we wish to discover thereby the value of X as efficiently as possible. (i) What is the most efficient possible sequence of such questions? Justify your answer. [2 marks] (ii) On average, how many questions should we need to ask? Justify your answer. [2 marks] (iii) Relate the sequence of questions to the bits in a uniquely decodable prefix code for X. [1 mark] (c) Define complex Gabor wavelets, restricting yourself to one-dimensional functions if you wish, and list four key properties that make such wavelets useful for encoding and compressing information, as well as for pattern recognition. Explain how their self-Fourier property and their closure under multiplication (i.e. the product of any two of them is yet again a Gabor wavelet) gives them also closure under convolution. Mention one disadvantage of such wavelets for reconstructing data from their projection coefficients. [8 mark (a) Consider an alphabet of 5 symbols whose probabilities are as follows: A B C D E 1 16 1 4 1 8 1 16 1 2 One of these symbols has been selected at random and you need to discover which symbol it is by asking 'yeso' questions that will be truthfully answered. (i) What would be the most efficient sequence of such questions that you could ask in order to discover the selected symbol? [2 marks] (ii) By what principle can you claim that each of your proposed questions in the sequence is maximally informative? [2 marks] (iii) On average, how many such questions will need to be asked before the symbol is discovered? What is the entropy of the symbol set? [2 marks] (iv) Construct a uniquely decodable prefix code for the symbols. Explain why it is uniquely decodable and why it has the prefix property. [2 marks] (v) Relate the bits in the code words forming your prefix code to the 'yeso' questions that you proposed in (i). [2 marks] (b) Explain how the bits in an IrisCode are set by phase sequencing. Discuss how quantisation of the
complex plane into phase quadrants sets each pair of bits; why it is beneficial for quadrant codes to form a Gray Code; how much entropy is thereby typically extracted from iris images; and why such bit sequences enable extremely efficient identity searches and matching. [5 marks] (c) Consider a noisy analog communication channel of bandwidth ? = 1 MHz, which is perturbed by additive white Gaussian noise whose total spectral power is N0? = 1. Continuous signals are transmitted across such a channel, with average transmitted power P = 1,000. Give a numerical estimate for the channel capacity, in bits per second, of this noisy channel. Then, for a channel having the same bandwidth ? but whose signal-to-noise ratio P N0? is four times better, repeat your numerical estimate of capacity in bits per second. [5 marks] Continuous Mathematics The complex form of the Fourier series is: where ck is a complex number and ck = c??k. (a) Prove that the complex coeffiffifficient, ck, encodes the amplitude and phase coeffiffifficients, Ak and ?k, in the alternative form: An interprocess communication environment is based on synchronous message passing. A server is to be designed to support a moderate number of simultaneous client requests. Clients send a request message to the server, continue in parallel with server operation, then wait for the server's reply message. Discuss the design of the server's interaction with the clients. Include any problems you foresee and discuss alternative solutions to them. [20 marks] 2CST.2001.4.3 3 Further Java (a) Describe how mutual-exclusion locks provided by the synchronized keyword can be used to control access to shared data structures. In particular you
should be clear about the behaviour of concurrent invocations of difffferent synchronized methods on the same object, or of the same synchronized method on difffferent objects. [6 marks] (b) Consider the following class defifinition: class Example implements Runnable { public static Object o = new Object(); int count = 0; public void run() { while (true) { synchronized (o) { Show how to start two threads, each executing this run method. [2 marks] (c) When this program is executed, only one of the count fifields is found to increment, even though threads are scheduled preemptively. Why might this be? [2 marks] (d) Defifine a new class FairLock. Each instance should support two methods, lock and unlock, which acquire and release a mutual exclusion lock such that calls to unlock never block the caller, but will allow the longest-waiting blocked thread to acquire the lock. The lock should be recursive, meaning that the thread holding the lock may make multiple calls to lock without blocking. The lock is released only when a matched number of unlock operations have been made. You may wish to make use of the fact the Thread.currentThread() returns
the instance of Thread that is currently executing. [10 marks] 3 [TURN OVERCST.2001.4.4 4 Compiler Construction Consider the following grammar giving the concrete syntax of a language: where C repeatwhile E has the same meaning as do C while E in C or Java. (a) List the terminals and non-terminals of this grammar and explain the signifificance of S. [3 marks] (b) Identify any ambiguities in the above grammar and recontriveit to remove them, ensuring that your new grammar generates exactly the same set of strings. [4 marks] (c) Specify a suitable abstract syntax, for example by giving a type declaration in a programming language of your choice, which might be used to hold parse trees for this language. [3 marks] (d) Give either a recursive descent parser or a characteristic fifinite state machine (e.g. for SLR(1)) with associated parser for your grammar. Your parser need not return a parse tree?it suffiffiffices for your parser either to accept or to reject the input string. [10 marks] 4CST.2001.4.5 5 Data Structures and Algorithms (a) Outline how you would determine whether the next line segment turns left or right during the Graham scan phase of the standard method of computing the
convex hull of a set of points in a plane. [5 marks] (b) Describe in detail an effiffifficient algorithm to determine how often the substring ABRACADABRA occurs in a vector of 106 characters. Your algorithm should be as effiffifficient as possible. [10 marks] (c) Roughly estimate how many character comparisons would be made when your algorithm for part (b) is applied to a vector containing 106 characters uniformly distributed from the 26 letters A to Z. [5 marks] 6 ECAD (a) When designing clocked circuits there are times when asynchronous inputs have to be sampled which may result in metastable behaviour in state holding elements. How might metastability be avoided when sampling asynchronous inputs? [5 marks] (b) An optical shaft encoder (e.g. used on the internal rollers of a mechanical mouse) consists of a disk with an evenly spaced alternating transparent and opaque grating around the circumference. Two optical sensors are positioned such that when one sensor is at the middle of an opaque region, the other is at the edge. Consequently, the following Gray code sequence is produced, depending upon the direction of rotation: positive rotation negative rotation A shaft decoder module is required to convert the Gray code into an 8-bit position. The 8-bit position should be incremented every time the input
changes from one state to another in a positive direction (e.g. from 00 to 01, or from 10 to 00). Similarly, the 8-bit position should be decremented every time the input changes from one state to another in a negative direction (e.g. from 00 to 10, or from 01 to 00). Contriveand comment a Verilog module which performs the function of a shaft decoder. [15 marks]
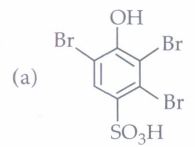
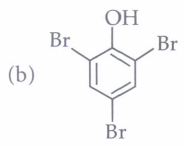
Although chlorobenzene is inert to nucleophilic substitution, however it gives quantitative yield of phenol when heated with aq. NaOH at high temperature and under high pressure. As far as electrophilic substitution in phenol is concerned the - OH group is an activating group, hence, its presence enhances the electrophilic substitution at o- and p-positions. The following questions are multiple choice questions. Choose the most appropriate answer: (i) Conversion of chlorobenzene into phenol involves
| (a) modified SN1 mechanism | (b) modified SN2 mechanism |
| (c) both (a) and (b) | (d) elimination-addition mechanism. |
(ii) Phenol undergoes electrophilic substitution more readily than benzene because
| (a) the intermediate carbo cation is a resonance hybrid of more resonating structures than that from benzene |
| (b) the intermediate is more stable as it has positive charge on oxygen, which can be better accommodated than on carbon |
| (c) in one of the canonical structures, every atom (except hydrogen) has complete octet |
| (d) the -OH group is o, p-directing which like all other o, p-directing group, is activating. |
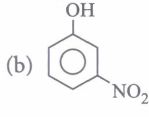
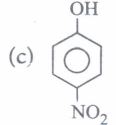
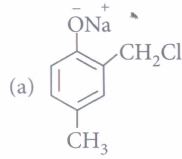
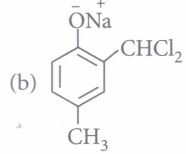
(iii) Phenol on treatment with excess of conc. HNO3gives
| (a) o-nitrophenol | (b) p-nitrophenol |
| (c) o-and p-nitrophenol | (d) 2,4,6-trinitrophenol |
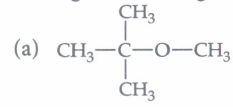
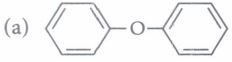
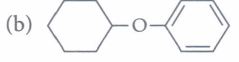
(iv) The major product of the following reaction is
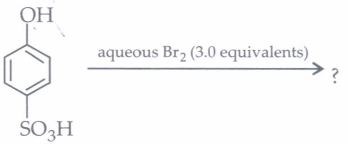
![memory. [3 marks] (ii) Explain how space and time overheads arise from](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464bd78ce2_02966e464bd655ce.jpg)
![time overheads. [3 marks] (b) Consider a system with a five level](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464be18182_02966e464bdf26ed.jpg)
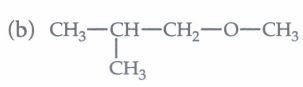
![is the effective memory access latency? [4 marks] (ii) A colleague suggests](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464c05e9cc_03266e464c02ee4e.jpg)
![should accept the replacement or not, and why. [4 marks] (c) A](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464c16072c_03366e464c14c88e.jpg)
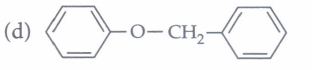
 Describe two quantitative and two qualitative](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464c2aff2c_03466e464c298f87.jpg)
![techniques for analysing the usability of a software product. [4 marks] (b)](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464c308329_03466e464c2e94a3.jpg)
![Compare the costs and benefits of the quantitative techniques. [6 marks] (c)](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464c34fc3b_03566e464c34035c.jpg)
![Compare the costs and benefits of the qualitative techniques. [6 marks] (d)](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464c394499_03566e464c37cea5.jpg)
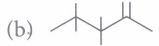
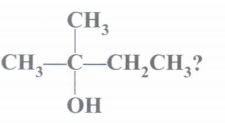
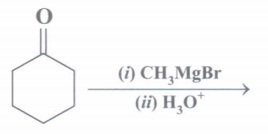
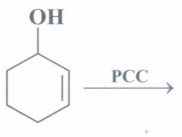
![is male? [2 marks] (b) Consider n discrete random variables, named X1,](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66e464c5667a0_03766e464c545e63.jpg)
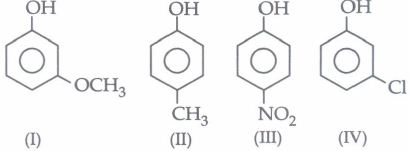
\f\f\f\f\f\f\fOH OH OH OH OCH3 Cl CH3 NO2 II) III) (IV)\f\f\f\f\f\f\f\f\f\f\f\f\fCH CH OH 44144412504 CH CH H O a = 3 2 433-443 K 3 3 + 1 conc. H 50 2CH3CH20H $1249 CH3CH2 0 CH2CH3 + [-120 \f\f\f\f\f\f\f
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


