Question
Consider the accompanying two elective meanings of a MAC work, which gets as info an (n L)- cycle long message of the structure M =
Consider the accompanying two elective meanings of a MAC work, which gets as info an (n L)- cycle long message of the structure M = M1kM2k . . . kML with Mi ? {0, 1} n and a private key K ? {0, 1} n picked consistently at irregular, returning a label T ? {0, 1} n . Show how neither one of the definitions gives the security property of existential unforgeability. (I) Let F be a n-cycle to n-bit pseudo-irregular capacity. Return the message label T = FK(M1) ? FK(M2) ? ? FK(ML). [4 marks] (ii) Let F be a (2n)- piece to n-digit pseudo-arbitrary capacity. Return the message label T = FK(h1ikM1) ? FK(h2ikM2) ? ? FK(hLikML). [6 marks] [Documentation: k = connection of spot strings, ? = bit-wise XOR, hii = n-cycle parallel portrayal of non-negative whole number i.] (b) Your partner proposes to develop a validated encryption conspire that encodes a plain-instant message M by first ascertaining the message verification code CMACK(M) = T, and afterward frames the ciphertext by encoding MkT utilizing CFB mode with beginning vector IV = EK(T), utilizing a similar key and blockcipher EK. Does this development offer CCA security? Why or what difference would it make? [5 marks] (c) Given a square code EK with n-bit block size, where n ? 64 is a force of two, how might you use EK to develop a solid pseudo-irregular stage for n
A government agent chooses for utilize a self-synchronizing scrambler to encode his mystery message. Make sense of why this won't give him any security and why his self-synchronizing move toward would be better utilized by an interchanges engineer. [5 marks] (b) With the help of clarified graphs make sense of CSMA/CD and CSMA/CA. In your clarification, note the actual imperatives on parcels and organizations that these methodologies force. [10 marks] (c) Consider the organization cradle estimating recipe B = 2T C (I) Explain this equation. [2 marks] (ii) Discuss the organization engineering and traffic presumptions made in the utilization of this equation.
: Compose total java program that prompts the client for their name and two numbers. a program that will request that the client enter your name and your class segment
The following are four choices for further developing website page execution. Choice 1: HTTP Caching with a Forward Proxy Choice 2: CDN utilizing DNS Choice 3: CDN utilizing anycast Choice 4: CDN in view of revamping HTML URLs You have been approached to assist with diminishing the expenses for systems administration in the University. (a) The University pays its specialist organization networks'r'us, in view of the data transmission it utilizes; data transfer capacity use is overwhelmed by understudies downloading outer site pages. Which, if any, of the over four choices could lessen the transmission capacity use? Make sense of your decision. [4 marks] (b) The conveyance of online courses has turned into an enormous achievement - however this has prompted a huge expansion in network costs for the University. You should choose one of the choices above to limit load on the servers. Look at the activity of every choice and legitimize a determination that gives the best granularity of command over burden to the substance servers and a choice that will serve every client from the nearest CDN server. [12 marks] (c) You have looked into the IP address of your number one web crawler on the College organization and saw the response is unique in relation to that given to your companion when he did the query in Newfoundland, Canada. For every choice above, show why it may, or could not, be utilized by your most loved web crawler to further develop site page execution. [4 marks] 6 CST.2013.5.7 6 Computer Networking (a) Considering either TCP/IP or UDP/IP, compose a depiction of how server-port, client-port, source-port and objective port connect with one another. You might wish to give models and use charts as proper. [4 marks] (b) What is a directing circle? Remember a chart for your response. [4 marks] (c) Describe an instrument that forestalls directing circles in Ethernet organizations. [4 marks] (d) (I) Describe and, with the guide of a model, represent the IP Time-To-Live (TTL) system for limiting the effect of directing circles. [2 marks] (ii) Assuming, to some degree (d)(i), an ideal execution, portray an inconvenience of the methodology including the side effects that may be knowledgeable about a network subject to this weakness, and a test that might distinguish the issue. [2 marks] (e) Explain the specialized and design contention behind the choice in IPv6 to hold header TTL yet not a header checksum. [2 marks] (f ) Explain why there is uncertainty about taking care of parcels with TTL upsides of 1 what's more, give a useful arrangement.
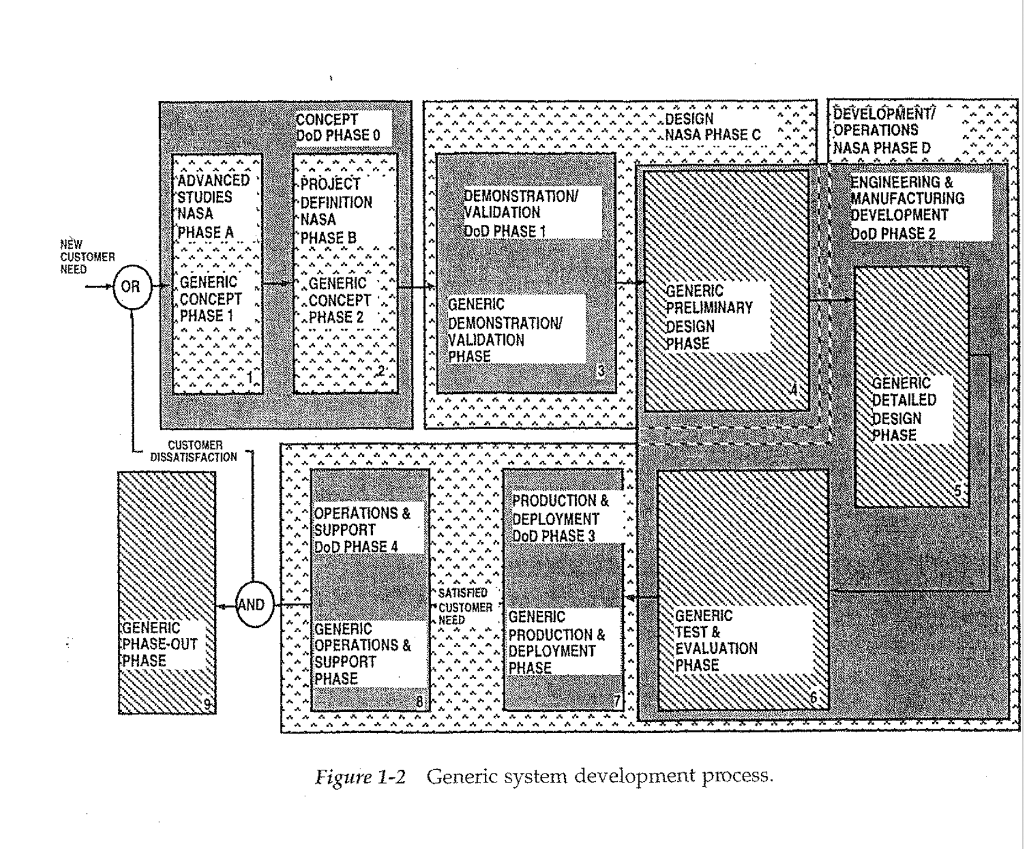
NEW CUSTOMER NEED -OR A ADVANCED STUDIES NASA PHASE A GENERIC CONCEPT PHASE 1 CUSTOMER DISSATISFACTION GENERIC PHASE-OUT PHASE AND CONCEPT DOD PHASE 0 PROJECT DEFINITION NASA PHASE B GENERIC CONCEPT PHASE 2 OPERATIONS & SUPPORT DOD PHASE 4 GENERIC OPERATIONS & SUPPORT PHASE DEMONSTRATION/ VALIDATION DOD PHASE 1 MEN GENERIC DEMONSTRATION/ VALIDATION PHASE SATISFIED CUSTOMER NEED PRODUCTION & DEPLOYMENT DOD PHASE 3 GENERIC PRODUCTION & DEPLOYMENT PHASE DESIGN NASA PHASE C GENERIC PRELIMINARY DESIGN PHASE NOWO GENERIC TEST & EVALUATION PHASE Figure 1-2 Generic system development process. DEVELOPMENTI OPERATIONS NASA PHASE D ENGINEERING & MANUFACTURING DEVELOPMENT DOD PHASE 2 GENERIC DETAILED DESIGN PHASE
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


