Consider the following assembly code, which has 3 functions, main, func1 and func2. Fill in the stack table given from bottom to top to show the Stack when the program is at the end of func2.:
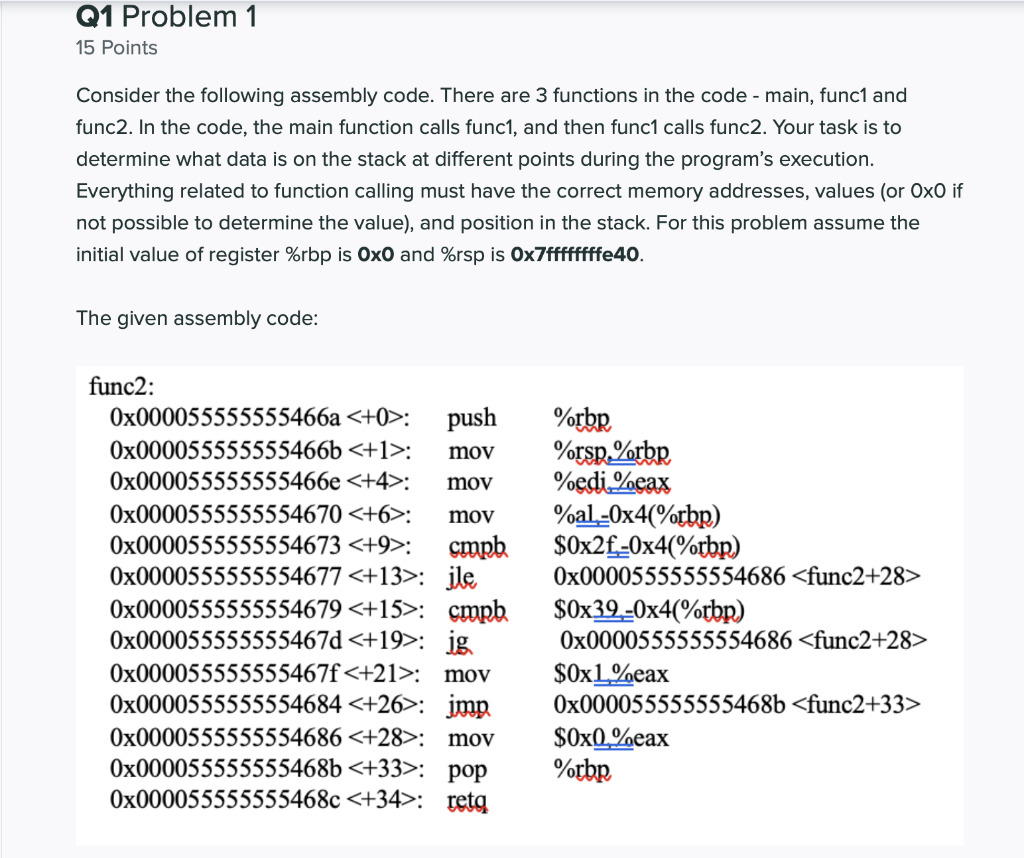

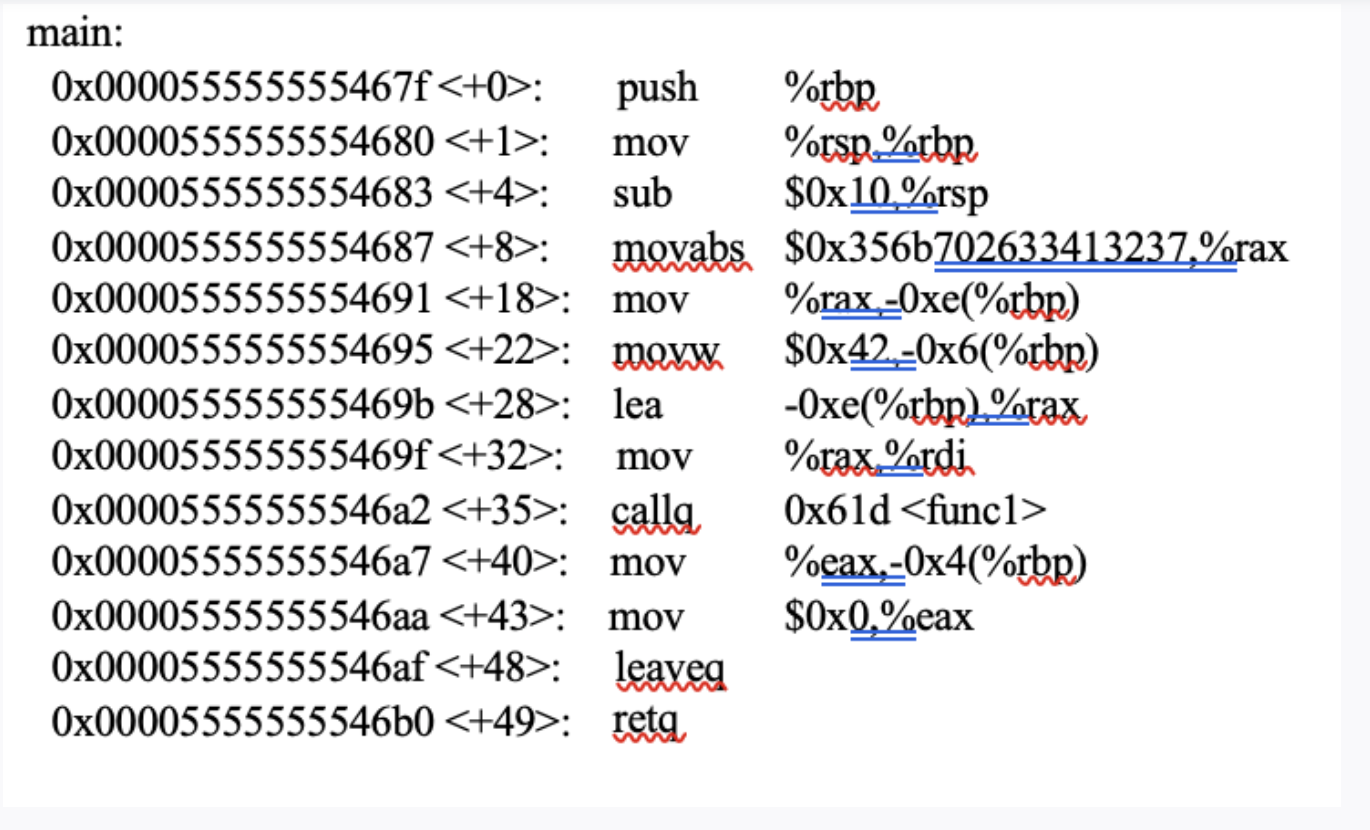
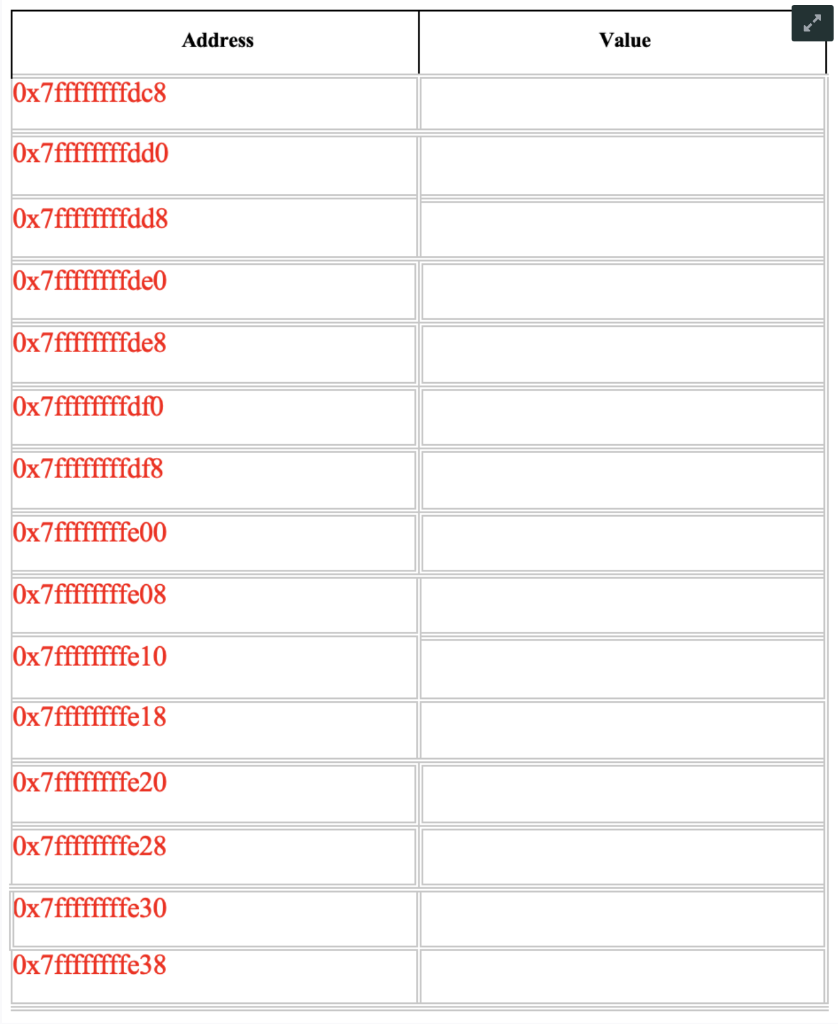
Q1 Problem 1 15 Points Consider the following assembly code. There are 3 functions in the code - main, func1 and func2. In the code, the main function calls func1, and then func1 calls func2. Your task is to determine what data is on the stack at different points during the program's execution. Everything related to function calling must have the correct memory addresses, values (or Oxo if not possible to determine the value), and position in the stack. For this problem assume the initial value of register %rbp is OxO and %rsp is Ox7ffffffffe40. The given assembly code: func2: 0x000055555555466a : push Ox000055555555466b ; mov Ox000055555555466e : mov 0x0000555555554670 : mov Ox0000555555554673 : cmpb 0x0000555555554677 : ile 0x0000555555554679 : cmpb 0x000055555555467d : jg 0x000055555555467f: mov 0x0000555555554684 : imp 0x0000555555554686 : mov 0x000055555555468b : pop 0x000055555555468c : retg %rbr %rsp,%rbr %edi Zeax %al-Ox4(%rbp) $0x2f-0x4(%rbp) Ox0000555555554686
$0x39-0x4(%rbp) Ox0000555555554686 $0x1%eax 0x000055555555468b $0x0.%eax %rbp push %rbp funcl: Ox000055555555468d 0x000055555555468e : mov 0x0000555555554691 : sub 0x0000555555554695 : mov 0x0000555555554699 : moxl 0x00005555555546a0 ; moxl 0x00005555555546a7 : moxl Ox00005555555546ae : imp Ox00005555555546b0 : mov %rspZorbp $0x18.%rsp %rdi.-0x18(%rbp) $0xQ_-Ox8(%rbp) $0x0-0x4(%rbp) $0x0-0x4%rbp) 0x00005555555546d6 -Ox4(%rbr). %eax 0x00005555555546b3 : movslg %eax.%rdx 0x00005555555546b6 : mov -0x18(%rbr),%rax Ox00005555555546ba : add %rdx%rax 0x00005555555546bd : movzbl (%rax),%eax 0x00005555555546c0 ; movsbl%al,%eax 0x00005555555546c3 : mov %eax,medi 0x00005555555546c5 : calla 0x000055555555466a Ox00005555555546ca : test %eax,%eax 0x00005555555546cc : je 0x00005555555546d2 0x00005555555546ce ; addi $0x1,_0x8(%rbr) 0x00005555555546d2 ; addl $0x1,-0x4(%rbr) 0x00005555555546d6 : mov -0x4%rbr..%eax 0x00005555555546d9 : movsla %eax.%rdx 0x00005555555546dc: mov -Ox18(%rbp),%rax 0x00005555555546e0 add %rdx.%rax 0x00005555555546e3 : moyzbl (%rax), %eax 0x00005555555546e6 : test %a1%a! Ox00005555555546e8 ; jne 0x00005555555546b0 Ox00005555555546ea : mov -0x8(%rbr),%eax Ox00005555555546ed : leaveg 0x00005555555546ee : reta main: Ox000055555555467f : push %rbp Ox0000555555554680 : mov %rsp%rbp 0x0000555555554683 : sub $0x10 %rsp 0x0000555555554687 : movabs $0x3566702633413237,%rax 0x0000555555554691 mov %rax-Oxe(%rbp) 0x0000555555554695 : movw $0x42-0x6(%rbp) 0x000055555555469b : lea -Oxe(%rbp).%rax Ox000055555555469f : mov %rax. %rdi 0x00005555555546a2 : calla, Ox61d 0x00005555555546a7 : mov %eax.-0x4(%rbp) 0x00005555555546aa : mov $0x0,%eax 0x00005555555546af : leaveg Ox00005555555546b0 : reta W Address Value 0x7ffffffffdc8 0x7ffffffffddo 0x7ffffffffdd8 0x7ffffffffdeo Ox7ffffffffde8 0x7ffffffffdfo 0x7ffffffffdf8 0x7ffffffffe00 0x7ffffffffe08 0x7ffffffffe10 0x7ffffffffe18 0x7ffffffffe20 0x7ffffffffe28 0x7ffffffffe30 0x7ffffffffe38 Q1 Problem 1 15 Points Consider the following assembly code. There are 3 functions in the code - main, func1 and func2. In the code, the main function calls func1, and then func1 calls func2. Your task is to determine what data is on the stack at different points during the program's execution. Everything related to function calling must have the correct memory addresses, values (or Oxo if not possible to determine the value), and position in the stack. For this problem assume the initial value of register %rbp is OxO and %rsp is Ox7ffffffffe40. The given assembly code: func2: 0x000055555555466a : push Ox000055555555466b ; mov Ox000055555555466e : mov 0x0000555555554670 : mov Ox0000555555554673 : cmpb 0x0000555555554677 : ile 0x0000555555554679 : cmpb 0x000055555555467d : jg 0x000055555555467f: mov 0x0000555555554684 : imp 0x0000555555554686 : mov 0x000055555555468b : pop 0x000055555555468c : retg %rbr %rsp,%rbr %edi Zeax %al-Ox4(%rbp) $0x2f-0x4(%rbp) Ox0000555555554686 $0x39-0x4(%rbp) Ox0000555555554686 $0x1%eax 0x000055555555468b $0x0.%eax %rbp push %rbp funcl: Ox000055555555468d 0x000055555555468e : mov 0x0000555555554691 : sub 0x0000555555554695 : mov 0x0000555555554699 : moxl 0x00005555555546a0 ; moxl 0x00005555555546a7 : moxl Ox00005555555546ae : imp Ox00005555555546b0 : mov %rspZorbp $0x18.%rsp %rdi.-0x18(%rbp) $0xQ_-Ox8(%rbp) $0x0-0x4(%rbp) $0x0-0x4%rbp) 0x00005555555546d6 -Ox4(%rbr). %eax 0x00005555555546b3 : movslg %eax.%rdx 0x00005555555546b6 : mov -0x18(%rbr),%rax Ox00005555555546ba : add %rdx%rax 0x00005555555546bd : movzbl (%rax),%eax 0x00005555555546c0 ; movsbl%al,%eax 0x00005555555546c3 : mov %eax,medi 0x00005555555546c5 : calla 0x000055555555466a Ox00005555555546ca : test %eax,%eax 0x00005555555546cc : je 0x00005555555546d2 0x00005555555546ce ; addi $0x1,_0x8(%rbr) 0x00005555555546d2 ; addl $0x1,-0x4(%rbr) 0x00005555555546d6 : mov -0x4%rbr..%eax 0x00005555555546d9 : movsla %eax.%rdx 0x00005555555546dc: mov -Ox18(%rbp),%rax 0x00005555555546e0 add %rdx.%rax 0x00005555555546e3 : moyzbl (%rax), %eax 0x00005555555546e6 : test %a1%a! Ox00005555555546e8 ; jne 0x00005555555546b0 Ox00005555555546ea : mov -0x8(%rbr),%eax Ox00005555555546ed : leaveg 0x00005555555546ee : reta main: Ox000055555555467f : push %rbp Ox0000555555554680 : mov %rsp%rbp 0x0000555555554683 : sub $0x10 %rsp 0x0000555555554687 : movabs $0x3566702633413237,%rax 0x0000555555554691 mov %rax-Oxe(%rbp) 0x0000555555554695 : movw $0x42-0x6(%rbp) 0x000055555555469b : lea -Oxe(%rbp).%rax Ox000055555555469f : mov %rax. %rdi 0x00005555555546a2 : calla, Ox61d 0x00005555555546a7 : mov %eax.-0x4(%rbp) 0x00005555555546aa : mov $0x0,%eax 0x00005555555546af : leaveg Ox00005555555546b0 : reta W Address Value 0x7ffffffffdc8 0x7ffffffffddo 0x7ffffffffdd8 0x7ffffffffdeo Ox7ffffffffde8 0x7ffffffffdfo 0x7ffffffffdf8 0x7ffffffffe00 0x7ffffffffe08 0x7ffffffffe10 0x7ffffffffe18 0x7ffffffffe20 0x7ffffffffe28 0x7ffffffffe30 0x7ffffffffe38










