Question: Consider the following authentication protocol between a database client and server. Step 1: The user provides his/her username u and password p to the
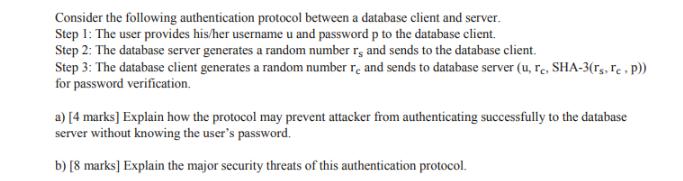
Consider the following authentication protocol between a database client and server. Step 1: The user provides his/her username u and password p to the database client. Step 2: The database server generates a random number r, and sends to the database client. Step 3: The database client generates a random number re and sends to database server (u, re, SHA-3(Ts, Te. P)) for password verification. a) [4 marks] Explain how the protocol may prevent attacker from authenticating successfully to the database server without knowing the user's password. b) [8 marks] Explain the major security threats of this authentication protocol.
Step by Step Solution
3.41 Rating (151 Votes )
There are 3 Steps involved in it
a Explanation of Prevention of Unauthorized Authentication The provided authentication protocol employs a challengeresponse mechanism that helps prevent attackers from successfully authenticating to t... View full answer

Get step-by-step solutions from verified subject matter experts


