

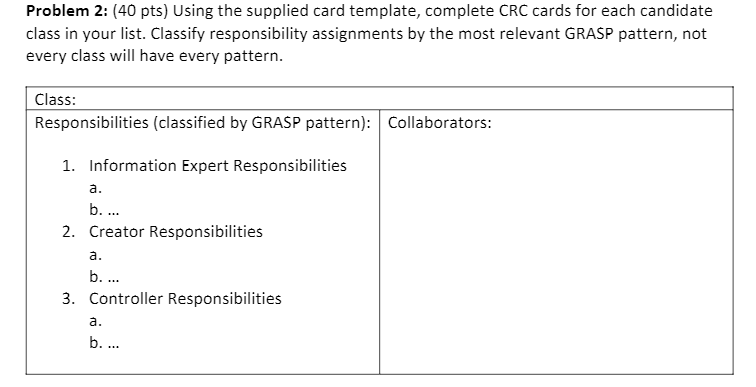
Consider the following use case that describes how a Bank Customer uses an ATM to withdraw money from a bank account. It is adapted from the book Use Case Modeling by Kurt Bittner and lan Spence. Use Case Name: Withdraw Cash Primary Actor: Customer Triggering Event: Customer visits ATM to withdraw cash. Stakeholders and Interests: Service Administrator, Security Administrator, ATM Engineer, ATM Operator, Bank System Preconditions: The bank Customer must possess a bank card. The network connection to the Bank System must be active. The system must have at least some cash that can be dispensed. The cash withdrawal service option must be available. Success Guarantee: Customer has received cash and their account balance is reduced appropriately. Main Success Scenario: 1. Customer inserts a bank card into the card reader on the ATM. 2. System allocates an ATM session identifier to enable errors to be tracked and synchronized between the ATM and the Bank System. 3. System reads the bank card information from the card. 4. System contacts Bank System to authenticate the use of the bank card by the individual using the machine. 5. System displays the different service options that are currently available on the machine. 6. Customer selects to withdraw cash. 7. System prompts for the amount to be withdrawn by displaying the list of standard withdrawal amounts. 8. Customer selects an amount to be withdrawn. 9. System confirms with Bank System that the Customer has sufficient funds. 10. Bank System conducts the transaction. 11. System ejects the Customer's bank card. 12. Customer takes the bank card from the machine. 13. System dispenses the requested amount to the Customer. 14. System records a transaction log entry for the withdrawal. Alternative Flows: *a. At any time, system detects an attempt to gain physical access to the currency dispenser. 1. System starts to video the Customer. 2. System creates an event log entry to record the fact that the ATM has detected an attack. 3. System sends the event log entry to the Security Administrator, the Service Administrator, and the Bank System to inform them that the ATM is being attacked. 4. System confiscates the bank card. 5. System cancels any pending transaction. 6. System creates an event log entry to record the actions taken. The event log entry includes the bank card information (excluding the PIN). 7. System sends the event log entry to the Security Administrator, the Service Administrator, and the Bank System to inform them what action has been taken. 8. Customer is informed that the card has been confiscated and the transaction ended. 9. System saves the video recording with the session ID. 12a. Customer does not remove the bank card from the ATM within 30 seconds. 1. System beeps to alert the Customer. 2.a. Customer takes the bank card from the machine. 2.b. System detects the card has still not been removed within a minute 1. System retrieves the card and adds it to the confiscated cards. 3. System creates and event log entry to record the fact that the cart was left behind in the ATM. The event log entry includes the bank card information (excluding the PIN). 4. The system sends the event log entry to the Bank System to inform it that the card has been left in the ATM. 5. System turns off the alert. Problem 2: (40 pts) Using the supplied card template, complete CRC cards for each candidate class in your list. Classify responsibility assignments by the most relevant GRASP pattern, not every class will have every pattern. Class: Responsibilities (classified by GRASP pattern): Collaborators: 1. Information Expert Responsibilities a. 2. Creator Responsibilities a. b.... 3. Controller Responsibilities a. b.... Consider the following use case that describes how a Bank Customer uses an ATM to withdraw money from a bank account. It is adapted from the book Use Case Modeling by Kurt Bittner and lan Spence. Use Case Name: Withdraw Cash Primary Actor: Customer Triggering Event: Customer visits ATM to withdraw cash. Stakeholders and Interests: Service Administrator, Security Administrator, ATM Engineer, ATM Operator, Bank System Preconditions: The bank Customer must possess a bank card. The network connection to the Bank System must be active. The system must have at least some cash that can be dispensed. The cash withdrawal service option must be available. Success Guarantee: Customer has received cash and their account balance is reduced appropriately. Main Success Scenario: 1. Customer inserts a bank card into the card reader on the ATM. 2. System allocates an ATM session identifier to enable errors to be tracked and synchronized between the ATM and the Bank System. 3. System reads the bank card information from the card. 4. System contacts Bank System to authenticate the use of the bank card by the individual using the machine. 5. System displays the different service options that are currently available on the machine. 6. Customer selects to withdraw cash. 7. System prompts for the amount to be withdrawn by displaying the list of standard withdrawal amounts. 8. Customer selects an amount to be withdrawn. 9. System confirms with Bank System that the Customer has sufficient funds. 10. Bank System conducts the transaction. 11. System ejects the Customer's bank card. 12. Customer takes the bank card from the machine. 13. System dispenses the requested amount to the Customer. 14. System records a transaction log entry for the withdrawal. Alternative Flows: *a. At any time, system detects an attempt to gain physical access to the currency dispenser. 1. System starts to video the Customer. 2. System creates an event log entry to record the fact that the ATM has detected an attack. 3. System sends the event log entry to the Security Administrator, the Service Administrator, and the Bank System to inform them that the ATM is being attacked. 4. System confiscates the bank card. 5. System cancels any pending transaction. 6. System creates an event log entry to record the actions taken. The event log entry includes the bank card information (excluding the PIN). 7. System sends the event log entry to the Security Administrator, the Service Administrator, and the Bank System to inform them what action has been taken. 8. Customer is informed that the card has been confiscated and the transaction ended. 9. System saves the video recording with the session ID. 12a. Customer does not remove the bank card from the ATM within 30 seconds. 1. System beeps to alert the Customer. 2.a. Customer takes the bank card from the machine. 2.b. System detects the card has still not been removed within a minute 1. System retrieves the card and adds it to the confiscated cards. 3. System creates and event log entry to record the fact that the cart was left behind in the ATM. The event log entry includes the bank card information (excluding the PIN). 4. The system sends the event log entry to the Bank System to inform it that the card has been left in the ATM. 5. System turns off the alert. Problem 2: (40 pts) Using the supplied card template, complete CRC cards for each candidate class in your list. Classify responsibility assignments by the most relevant GRASP pattern, not every class will have every pattern. Class: Responsibilities (classified by GRASP pattern): Collaborators: 1. Information Expert Responsibilities a. 2. Creator Responsibilities a. b.... 3. Controller Responsibilities a. b









