Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Consider the SSL protocol in Figure 10.4. A.) Suppose that the nonces RA and RB are removed from the protocol and we define K =
Consider the SSL protocol in Figure 10.4.
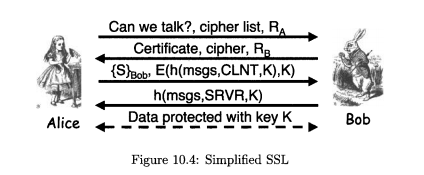
A.) Suppose that the nonces RA and RB are removed from the protocol and we define K = h(S). What effect, if any, does this have on the security of the authentication protocol?
B.) Suppose that we change message four to HMAC(msgs,SRVR,K). What effect, if any, does this have on the security of the authentication protocol?
C.) Suppose that we change message three to {S}Boh, h(msgs,CLNT,K). What effect, if any, does this have on the security of the authentication protocol?
Can we talk?, cipher list, RA Certificate, cipher, RB {S)Bob, E(h(msgs,CLNT,K),K) h(msgs,SRVR.K) Alice Data protected-ith keyK Bob Figure 10.4: Simplified SSLStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


