Create your own unique, full example for each of the 2 vulnerabilities in this category. It doesnt have to be a large, overly complex application, but it needs to be complete, and runnable and demonstrate how this vulnerability may appear in the real world.
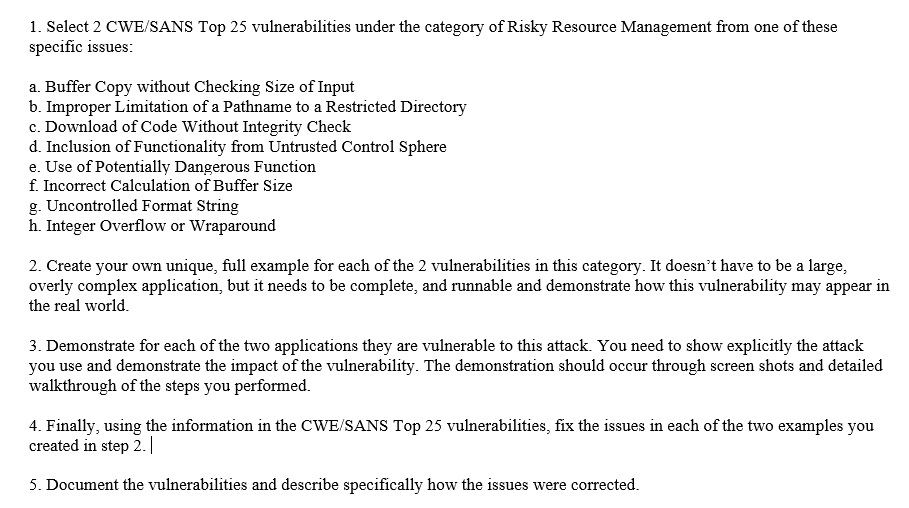
1. Select 2 CWE/SANS Top 25 vulnerabilities under the category of Risky Resource Management from one of these specitic issues a. Buffer Copy without Checking Size of Input b. Improper Limitation of a Pathname to a Restricted Directory c. Download of Code Without Integrity Check d. Inclusion of Functionality from Untrusted Control Sphere e. Use of Potentially Dangerous Function f. Incorrect Calculation of Buffer Size g. Uncontrolled Format String h. Integer Overflow or Wraparound 2. Create your own unique, full example for each of the 2 vulnerabilities in this category. It doesn't have to be a large, overly complex application, but it needs to be complete, and runnable and demonstrate how this vulnerability may appear in the real world 3. Demonstrate for each of the two applications they are vulnerable to this attack. You need to show explicitly the attack you use and demonstrate the impact of the vulnerability. The demonstration should occur through screen shots and detailed walkthrough of the steps you performed. 4. Finally, using the information in the CWE/SANS Top 25 vulnerabilities, fix the issues in each of the two examples you created in step 2. | 5. Document the vulnerabilities and describe specifically how the issues were corrected. 1. Select 2 CWE/SANS Top 25 vulnerabilities under the category of Risky Resource Management from one of these specitic issues a. Buffer Copy without Checking Size of Input b. Improper Limitation of a Pathname to a Restricted Directory c. Download of Code Without Integrity Check d. Inclusion of Functionality from Untrusted Control Sphere e. Use of Potentially Dangerous Function f. Incorrect Calculation of Buffer Size g. Uncontrolled Format String h. Integer Overflow or Wraparound 2. Create your own unique, full example for each of the 2 vulnerabilities in this category. It doesn't have to be a large, overly complex application, but it needs to be complete, and runnable and demonstrate how this vulnerability may appear in the real world 3. Demonstrate for each of the two applications they are vulnerable to this attack. You need to show explicitly the attack you use and demonstrate the impact of the vulnerability. The demonstration should occur through screen shots and detailed walkthrough of the steps you performed. 4. Finally, using the information in the CWE/SANS Top 25 vulnerabilities, fix the issues in each of the two examples you created in step 2. | 5. Document the vulnerabilities and describe specifically how the issues were corrected







