Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Cryptography Homework 10 TLS Following a TLS Connection The file, brcc.edu.png, is a Wireshark packet capture file (pcap) that includes a TLS 1.2 session
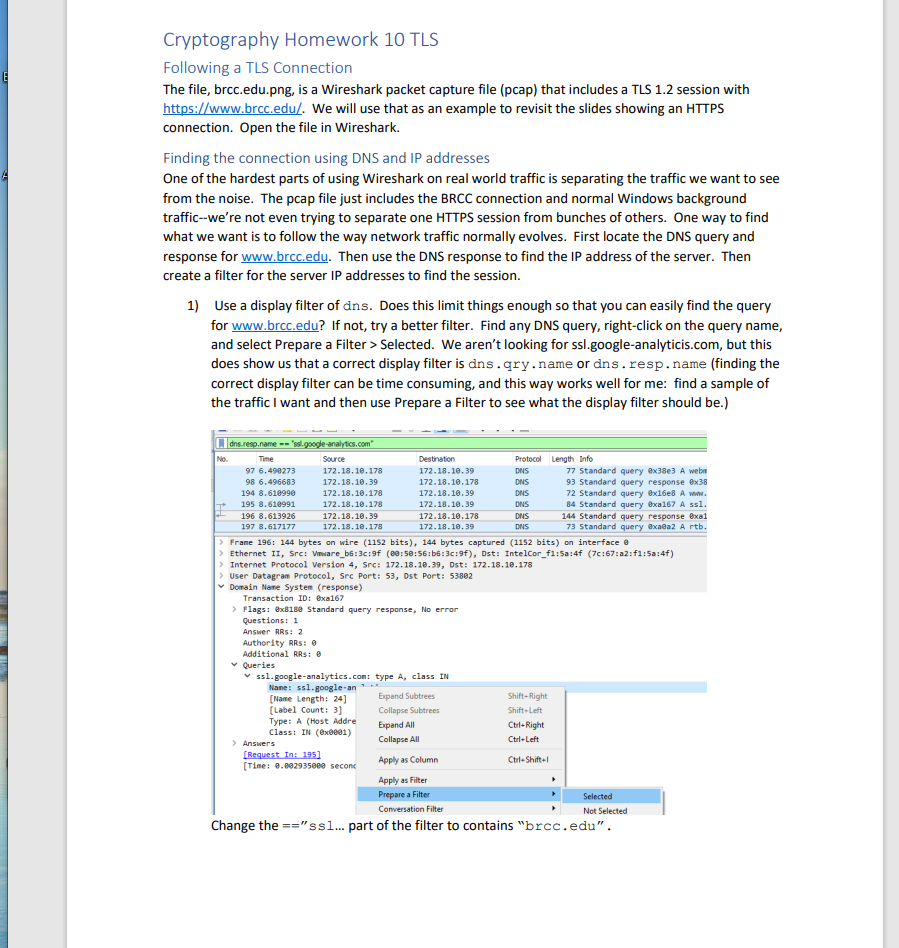
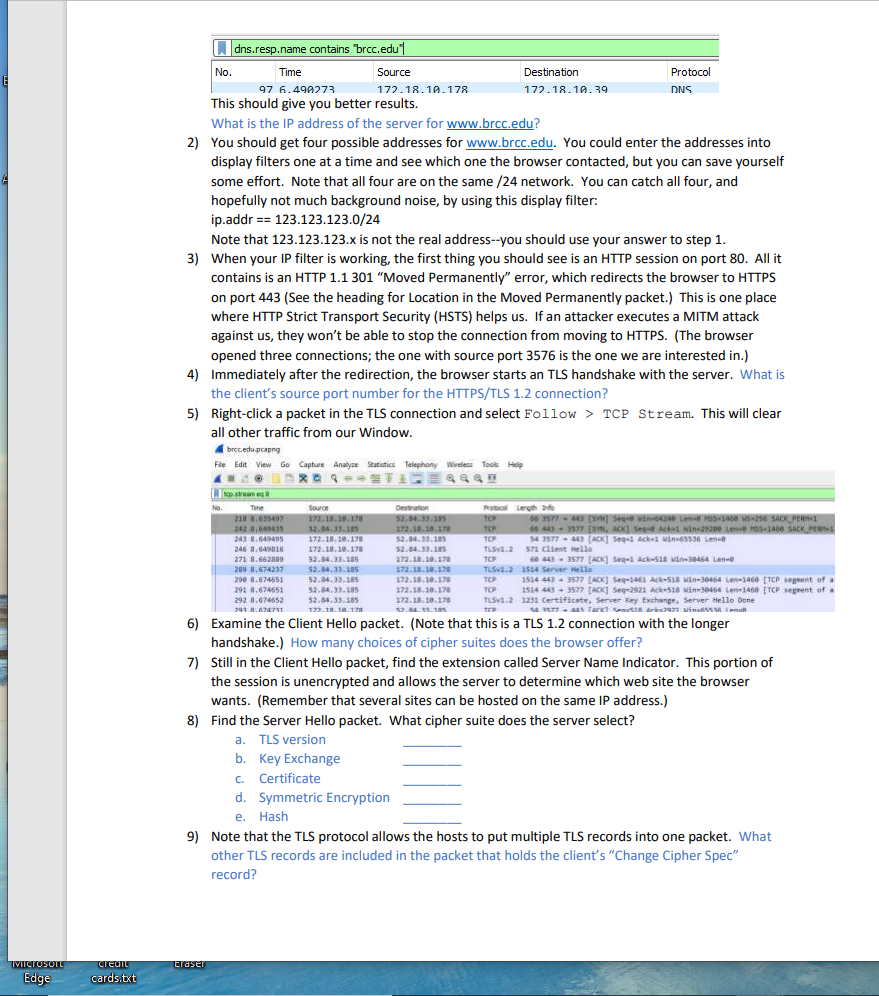
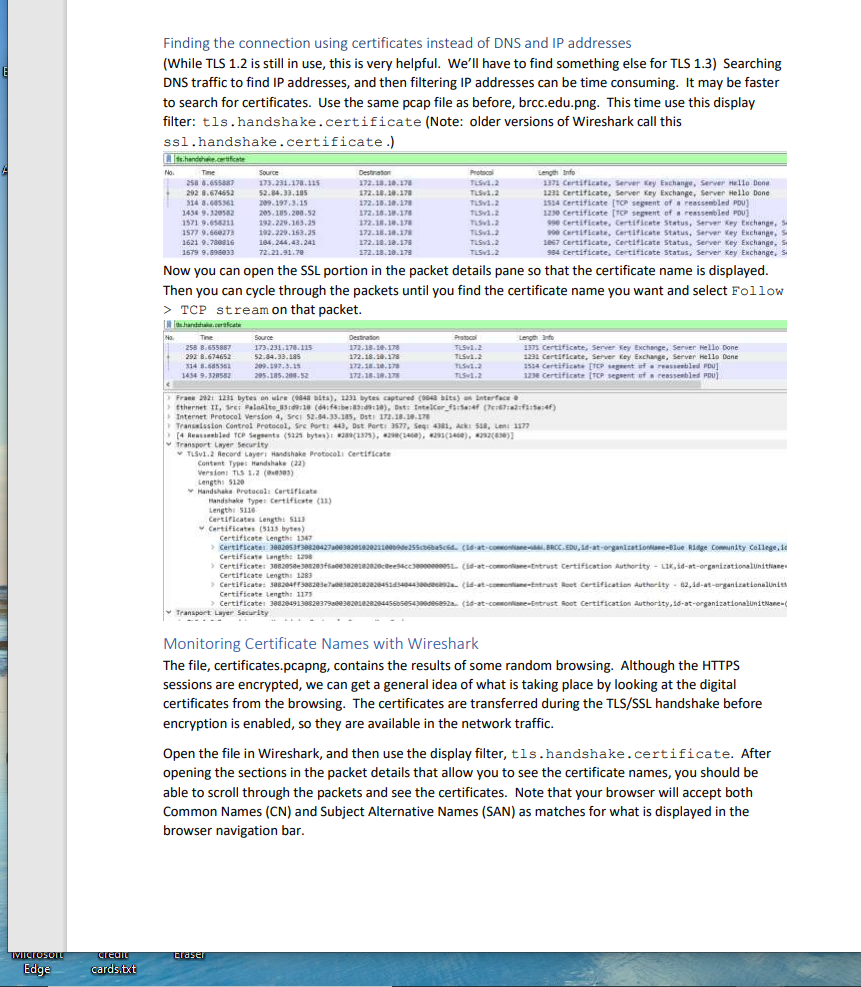
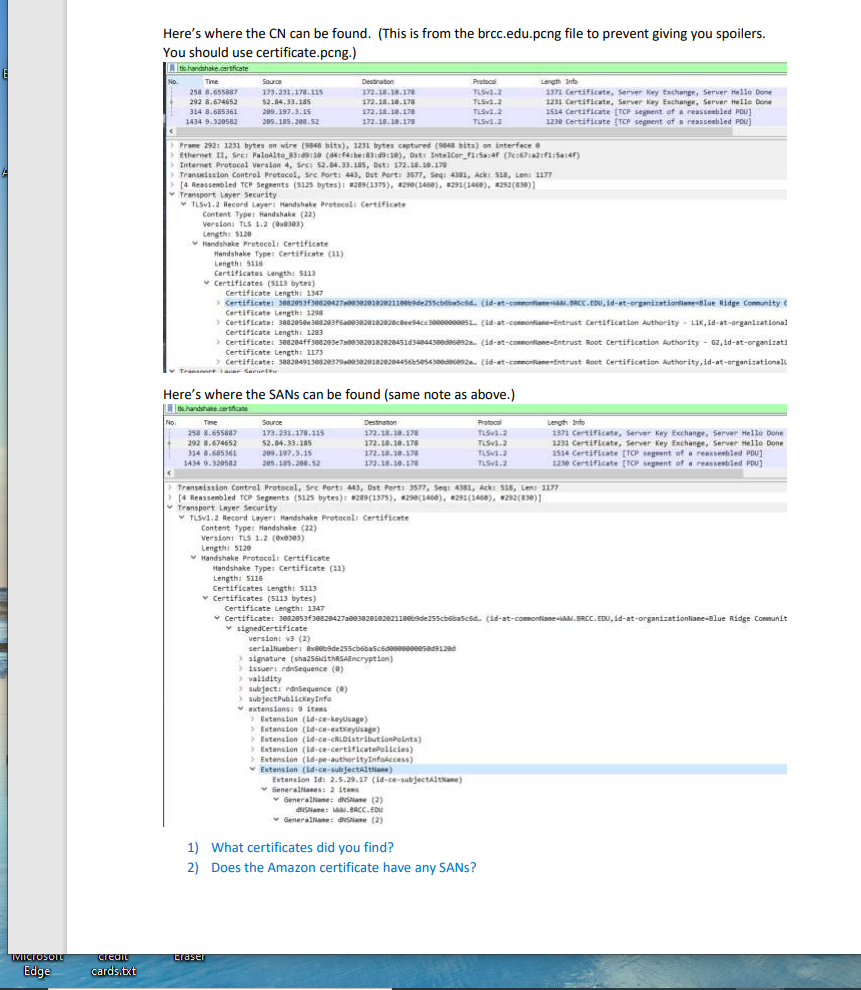
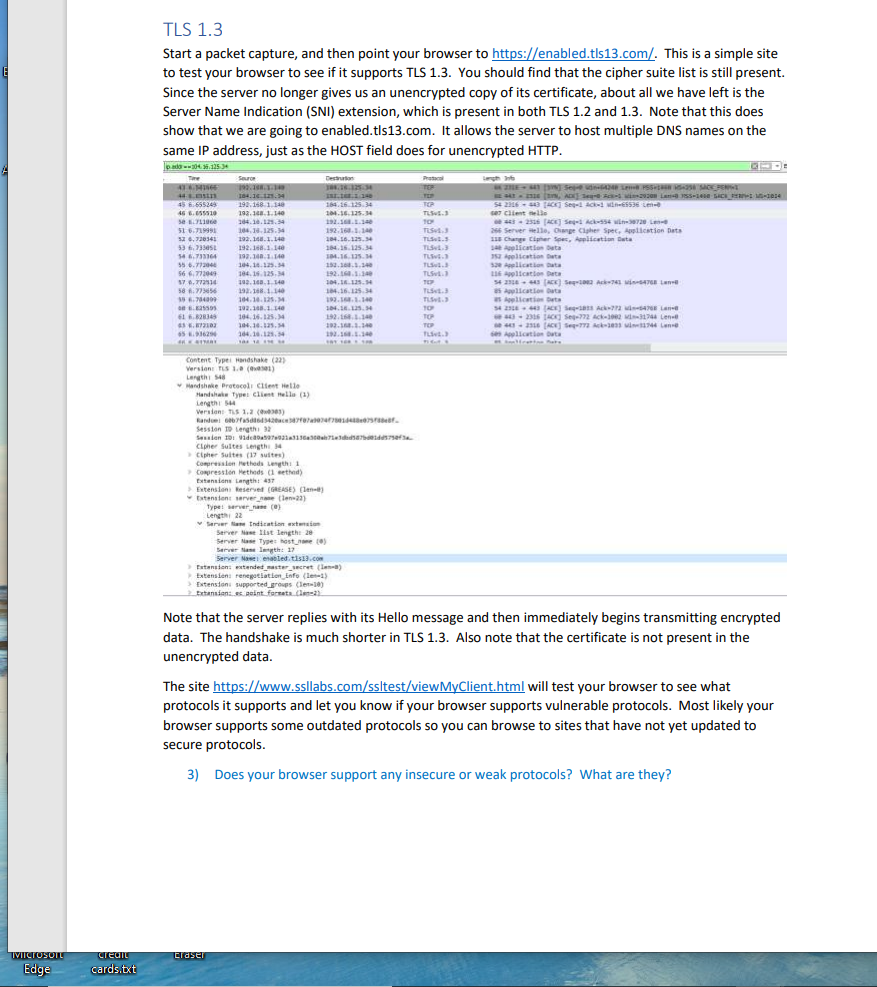
Cryptography Homework 10 TLS Following a TLS Connection The file, brcc.edu.png, is a Wireshark packet capture file (pcap) that includes a TLS 1.2 session with https://www.brcc.edu/. We will use that as an example to revisit the slides showing an HTTPS connection. Open the file in Wireshark. Finding the connection using DNS and IP addresses One of the hardest parts of using Wireshark on real world traffic is separating the traffic we want to see from the noise. The pcap file just includes the BRCC connection and normal Windows background traffic--we're not even trying to separate one HTTPS session from bunches of others. One way to find what we want is to follow the way network traffic normally evolves. First locate the DNS query and response for www.brcc.edu. Then use the DNS response to find the IP address of the server. Then create a filter for the server IP addresses to find the session. 1) Use a display filter of dns. Does this limit things enough so that you can easily find the query for www.brcc.edu? If not, try a better filter. Find any DNS query, right-click on the query name, and select Prepare a Filter > Selected. We aren't looking for ssl.google-analyticis.com, but this does show us that a correct display filter is dns.qry.name or dns. resp. name (finding the correct display filter can be time consuming, and this way works well for me: find a sample of the traffic I want and then use Prepare a Filter to see what the display filter should be.) [.dns.resp.name == "ssl.google-analytics.com" Source 172.18.10.178 172.18.10.39 172.18.10.178 172.18.10.178 172.18.10.39 172.18.10.178 No. Time 97 6.490273 98 6.496683 194 8.610990 195 8.610991 196 8.613926 197 8.617177 > Flags: x8180 Standard query response, No error Questions: 1 Answer RRs: 2 Authority Additional RRS: 0 > Frame 196: 144 bytes on wire (1152 bits), 144 bytes captured (1152 bits) on interface > Ethernet II, Src: Vmware_b6:3c:9f (00:50:56:b6:3c:9f), Dst: IntelCor_f1:5a:4f (7c:67:a2:f1:5a:4f) > Internet Protocol Version 4, Src: 172.18.10.39, Dst: 172.18.10.178 > User Datagram Protocol, Src Port: 53, Dst Port: 53802 Domain Name System (response) Transaction ID: @xa167 Queries ssl.google-analytics.com: type A, class IN Expand Subtrees Collapse Subtrees Name: ssl.google-an [Name Length: 24] [Label Count: 3] Destination 172.18.10.39 172.18.10.178 172.18.10.39 172.18.10.39 172.18.10.178 172.18.10.39 Type: A (Host Addre Class: IN (ex0001) > Answers Protocol Length Info DNS DNS DNS DNS DNS DNS [Request In: 195] [Time: 0.002935000 secon Shift+Right Shift+Left Expand All Collapse All Apply as Column Apply as Filter Prepare a Filter Conversation Filter Change the == "ss1... part of the filter to contains "brcc.edu". Ctrl+Right Ctrl+Left 77 Standard query @x38e3 A webr 93 Standard query response 0x38 72 Standard query @x16e8 A www. 84 Standard query exa167 A ssl. 144 Standard query response exal 73 Standard query @xa@a2 A rtb. Ctrl+Shift+ Selected Not Selected E IVICIOSOIL Edge credit cards.txt dns.resp.name contains "brcc.edu No. Time 97 6.490273 This should give you better results. What is the IP address of the server for www.brcc.edu? Source 2) You should get four possible addresses for www.brcc.edu. You could enter the addresses into display filters one at a time and see which one the browser contacted, but you can save yourself some effort. Note that all four are on the same /24 network. You can catch all four, and hopefully not much background noise, by using this display filter: ip.addr == 123.123.123.0/24 172.18.10.178 Note that 123.123.123.x is not the real address--you should use your answer to step 1. 3) When your IP filter is working, the first thing you should see is an HTTP session on port 80. All it contains is an HTTP 1.1 301 "Moved Permanently" error, which redirects the browser to HTTPS on port 443 (See the heading for Location in the Moved Permanently packet.) This is one place where HTTP Strict Transport Security (HSTS) helps us. If an attacker executes a MITM attack against us, they won't be able to stop the connection from moving to HTTPS. (The browser opened three connections; the one with source port 3576 is the one we are interested in.) Immediately after the redirection, the browser starts an TLS handshake with the server. What is the client's source port number for the HTTPS/TLS 1.2 connection? 4) top.strwam eq 8 traser 5) Right-click a packet in the TLS connection and select Follow > TCP Stream. This will clear all other traffic from our Window. brcc.edu.pcapng File Edit View Go Capture Analyze Statistics Telephony Wireless Tools Help No. Time 218 8.635493 242 8,649435 243 8.649495 246 8.649816 271 8.662889 208 8.674237 290 8.674651 291 8.674651 292 8.674652 791 8.674751 Destination 172.18.10.39 Source 172.18.10.170 32.84.33.105 172.18.10.178 172.18.10.178 52.84.33.185 52.84.33.185 52.84.33.185 52.84.33.185 52.84.33.185 177.18.18.178 6) Examine the Client Hello packet. (Note that this is a TLS 1.2 connection with the longer handshake.) How many choices of cipher suites does the browser offer? Protocol DNS Destination 52.54.35.385 172.18.10.178 32.84.33.185 52.04.33.185 172.18.10.178 172.18.10.178 172.18.10.178 172.18.10.178 172.18.10.178 a. TLS version b. Key Exchange c. Certificate d. Symmetric Encryption e. Hash Protocal Length fo TOP 66 3577 443 (SV] Seq-0 win-64240 Len-B55-1460 S-256 SACK_PER 66 4433577 [SYN, ACK] Seq-0 Ack-1 Min-29200 Lene SS-1400 SACK PERIS 34 3577 443 (ACK] Seq-1 Ack-1 win-65536 Len-B TLSV1.2 571 client Hello TCP TCP TCP 60 443 3577 [ACK] Seq-1 Ack-518 vin-30464 Len- TLSv1.2 1514 Server Hello TCP 1514 4433577 [ACK] Seq-1461 Ack-518 vin-30464 Len-1460 [TCP segment of TCP 1514 4433577 [ACK] Seq-2921 Ack-518 Min-30464 Len-1460 [TCP segment of a TL5v1.2 1231 Certificate, Server Key Exchange, Server Hello Done 156 1577 469 fark! Somut Arka7971 Wine L 7) Still in the Client Hello packet, find the extension called Server Name Indicator. This portion of the session is unencrypted and allows the server to determine which web site the browser wants. (Remember that several sites can be hosted on the same IP address.) 8) Find the Server Hello packet. What cipher suite does the server select? 9) Note that the TLS protocol allows the hosts to put multiple TLS records into one packet. What other TLS records are included in the packet that holds the client's "Change Cipher Spec" record? IVICIOSOIT Edge credit cards.txt Finding the connection using certificates instead of DNS and IP addresses (While TLS 1.2 is still in use, this is very helpful. We'll have to find something else for TLS 1.3) Searching DNS traffic to find IP addresses, and then filtering IP addresses can be time consuming. It may be faster to search for certificates. Use the same pcap file as before, brcc.edu.png. This time use this display filter: tls.handshake.certificate (Note: older versions of Wireshark call this ssl. handshake.certificate.) Ide handehace.certificate Time 258 8.655887 202 8.674652 314 8.685361 1434 9.320582 1571 9.658211 1577 9.660273 1621 9.700816 1679 9.896033 handha.coraficate Tine 258 8.655887 292 8.674652 314 8.685361 1434 9-320582 Source 173.231.178.115 52.84.33.105 209.197.3.15 205.185.200.52 192.229.163.25 192.229.163.25 104.244.43.241 72.21.91.79 Source Now you can open the SSL portion in the packet details pane so that the certificate name is displayed. Then you can cycle through the packets until you find the certificate name you want and select Follow > TCP stream on that packet. 173.231.178.115 52.84.33.185 209.197.5.15 295.185.200.52 Handshake Protocol: Certificate Handshake Type: Certificate (11) Length: 5116 traser Destination 172.18.10.178 172.18.10.178 172.18.10.178 172.18.10.178 172.18.10.178 172.18.10.178 172.18.18.178 172.18.10.179 Certificates Length: $113 Certificates (5113 bytes) Protocol TLSV1.2 TLSV1.2 TLSV1.2 TL5v1.2 TL5v1.2 TL5v1.2 TLSV1.2 TL5v1.2 Destination 172.18.10.178 172.18.10.178 172.18.10.178 172.18.18.178 LengthInfo 1371 Certificate, Server Key Exchange, Server Hello Done 1231 Certificate, Server xey Exchange, Server Hello Done 1514 Certificate [TCP segment of a reassembled PDU] 1230 Certificate [TCP segment of a reassembled POU] Protocol TLSV1.2 TLSv1.2 TL5v1.2 TL5v1.2 990 Certificate, Certificate Status, Server Key Exchange, S 900 Certificate, Certificate Status, Server key Exchange, S 1867 Certificate, Certificate Status, Server Key Exchange, S 954 Certificate, Certificate Status, Server Key Exchange, s Frane 292: 1231 bytes on wire (0848 bits), 1231 bytes captured (0043 bits) an Interface e Ethernet II, Sec: Palmilte 83:d9:10 (d4:f4:be:85:49:10), Dat: IntelCor_fla:4 (76721:5:4) Internet Protocol Version 4, Srci 52.84.33.185, Dst: 172.18.10.178 Transmission Control Protocol, Sec Port: 443, Ost Part: 3577, Seq: 4381, Ack: 518, Len: 1177 [4 Reassembled TCP Segeents ($125 bytes): #289(1375), 29(1400), 291(1400), 292(830)] Transport Layer Security TLSv1.2 Record Layer: Handshake Protocol: Certificate Content Type: Handshake (22) Version: TLS 1.2 (303) Length: $120 1371 Certificate, Server Key Exchange, Server Hello Done 1231 Certificate, Server Key Exchange, Server Hello Done 1534 Certificate [TCP segment of a reassembled POU] 1238 Certificate [TCP sepsent of a reassembled PDU) Certificate Length: 1347 > Certificate: 3082053130820427003020102021100b9de255cb6ba5c6d. (id-at-comonte, BRCC. EDU, id-at-organizationName-Blue Ridge Community College, in Certificate Length: 1208 Certificate: 38820503082036003020102020c8ee94cc30000000051 (id-at-commoniane-Entrust Certification Authority LIK, id-at-organizationalitate Certificate Length: 1283 Certificate: 388284ff388283e7a0e3828282828451434044300d0c92a. (id-at-commoniane-Entrust Root Certification Authority 62, id-at-organizationalUnits Certificate Length: 1175 > Certificate: 3082849138828379800382016282844560505430068928 (1d-at-commonne-Entrust Root Certification Authority, id-at-organizationalite Transport Layer Security Monitoring Certificate Names with Wireshark The file, certificates.pcapng, contains the results of some random browsing. Although the HTTPS sessions are encrypted, we can get a general idea of what is taking place by looking at the digital certificates from the browsing. The certificates are transferred during the TLS/SSL handshake before encryption is enabled, so they are available in the network traffic. Open the file in Wireshark, and then use the display filter, tls.handshake.certificate. After opening the sections in the packet details that allow you to see the certificate names, you should be able to scroll through the packets and see the certificates. Note that your browser will accept both Common Names (CN) and Subject Alternative Names (SAN) as matches for what is displayed in the browser navigation bar. E IVICTOSOTL Edge credit cards.txt Here's where the CN can be found. (This is from the brcc.edu.pcng file to prevent giving you spoilers. You should use certificate.pcng.) tis handshake.certificate Time 258 8.655887 292 8.674652 314 8.685361 1434 9.320582 No. No Source 173.231.178.115 52.84.33.185 209.197.3.15 285.185.288.52 Content Type: Handshake (22) Version: TLS 1.2 (00303) Frame 292: 1231 bytes on wire (948 bits), 1231 bytes captured (9648 bits) on interface Ethernet 11, Sre: PaloAlto 83:09:10 (04:f4:be:33:49:10), Ost: IntelCor_fi:58:4f (7c:67:a2:01:56:4f) Internet Protocol version 4, Sre: 52.84.33.185, Dst: 172.18.10.179 Length: $120 Handshake Protocol: Certificate Transmission Control Protocol, Src Port: 443, Dst Port: 3577, Seq: 4381, Ack: 518, Len: 1177 [4 Reassembled TCP Segments (5125 bytes): #289(1375), 8290 (1460), 291(1460), #292(830)] Transport Layer Security TL5v1.2 Record Layer: Handshake Protocol: Certificate Handshake Type: Certificate (11). Length: 5116 Certificates Length: 5113 Certificates (5113 bytes) Time 258 8.655887 292 8.674652 314 8.685361 1434 9.320582 traser Here's where the SANS can be found (same note as above.) Protocol TLSV1.2 TLSV1.2 TLSV1.2 TLSV1.2 Certificate Length: 1347 > Certificate: 308205330020427800302010202118069de255cbbascid. (id-at-commontiane.DaCC.EDU.id-at-organizationisme-Blue Ridge Community C Certificate Length: 1298 Certificate: 3882050308293f6a003828182828c94cc30000000051. (id-at-commonane-Entrust Certification Authority LIK, id-at-organizational Certificate Length: 1283 - > Certificate: 388284ff388205e78003028182828451434044300de5092a. (id-at-commoniane-Entrust Root Certification Authority 62, id-at-organizati Certificate Length: 1173 > Certificate: 388284913032037980053020102020445665854300506092a. (id-at-commonfame-Entrust Root Certification Authority, id-at-organizationalu Source 173.231.178.115 52.84.33.185 209.197.3.15 205.185.200.52 Content Type: Handshake (22) Version: TLS 1.2 (0x0303) Length: 5120 Handshake Protocol: Certificate Handshake Type: Certificate (11) Length: 5116 Destination 172.18.18.178 172.18.18.178 172.18.10.178 172.18.10.178 Certificates Length: 5113 Certificates (5113 bytes) Transmission Control Protocol, Sre Parts 443, Dst Port: 3577, Seq: 4381, Ack: 518, Len: 1177 [4 Reassembled TCP Segments (5125 bytes): #289 (1575), #290(1460), #291(1460), #292(830)] Transport Layer Security TLSV1.2 Record Layer: Handshake Protocol: Certificate > validity Destination 172.18.10.178 172.18.10.178 172.18.10.178 172.18.10.178 serialNumber: 8x80b9de255cb6ba5c6deeeeeeees@1200 > signature (sha256WithRSAEncryption) > issuer: rdnsequence (0) subject: rdnsequence (0) >subjectPublicKeyInfo extensions: 9 itens Certificate Length: 1347 Certificate: 3082053f388284278003820102021100b9de255cb6ba5c6d.. (id-at-commontane-M.BRCC.EDU, id-at-organizationName-Blue Ridge Communit signed Certificate version: v3 (2) Protocol TL5V2.2 TLSV3.2 TLSV2.2 TL5V2.2 Extension (id-ce-keysage) > Extension (id-ce-extkeyusage) > Extension (id-ce-cRLDistributionPoints) >Extension (id-ce-certificatePolicies) > Extension (id-pe-authorityInfoAccess) Extension (id-ce-subjectAlta) Length Info 1371 Certificate, Server Key Exchange, Server Hello Done 1231 Certificate, Server Key Exchange, Server Hello Done 1514 Certificate [TCP segment of a reassembled POU] 1238 Certificate (TCP segment of a reassembled FOU] Extension Id: 2.5.29.17 (id-ce-subjectAlta) Generaliases: 2 items Generallane: dNSame (2) Same: M.BRCC.EDU GeneralName: Shane (2) 1) What certificates did you find? 2) Does the Amazon certificate have any SANS? Length Info 1371 Certificate, Server Key Exchange, Server Hello Done 1231 Certificate, Server Key Exchange, Server Hello Done 1514 Certificate [TCP segment of a reassembled POU] 1230 Certificate [TCP segment of a reassembled POU] IVICIOSOIT Edge credit cards.txt TLS 1.3 Start a packet capture, and then point your browser to https://enabled.tls13.com/. This is a simple site to test your browser to see if it supports TLS 1.3. You should find that the cipher suite list is still present. Since the server no longer gives us an unencrypted copy of its certificate, about all we have left is the Server Name Indication (SNI) extension, which is present in both TLS 1.2 and 1.3. Note that this does show that we are going to enabled.tls13.com. It allows the server to host multiple DNS names on the same IP address, just as the HOST field does for unencrypted HTTP. pado-304 36.1253 Tire 41 6341866 44-8. 45 6:655245 46 6.055510 se 711960 51 6.719991 32 6.726341 53 6.733051 14 6.733364 55 6.772046 56 6,772049 57 6.772514 58 6.775656 35 6.704009 06825595 61 6.828349 45 6.872102 65.96296 Source 192.1981-148 184.16.125.34 192.168.1.140 192.148.1.140 204.10.125.39 104.14.125.34 192.148.1.140 192.168.1.140 192.168.1.140 104.14.125.14 104.16.125.34 192.168.1.140 192.168.1.140 104.10.125.34 192.168.1.140 104.16.125.M 104.14.125.34 104.16.125.14 Content Type: Handshake (22) Version: TLS 1.0 (1) Length: 548 Handshake Protocol: Client Helle Handshake Type: Client nella (3) Length: 544 Version: TLS 1.2 (33) Random: 0067fa56434203870707478014484075888f Session 1D Length: 32 Session 10: Vidc0a507031313637387bd01dd575034 Cipher Suites Length: 34 Cipher Suites (17 suites) Compression methods Length: 1 Compression Methods (1 eethod) Extensions Length: 437 Extensions Reserved (GREASE) (len-) Extensions server nane (len-22) 104.28.125-34 181.168.1.140 184.16.125.34 104.16.125.34 192.168.1.140 192.168.1.140 104.16.125.34 184.16.125.34 104.16.135.14 192.168.1.140 192.168.1.140 104.16.125.34 104.16.125.34 192.168.1.140 104.14.125.34 192.168.1.140 192.168.1.140 192.168.1.140 Type: server nase (0) Length: 22 Server Indication extension Server Nase ist length: 28 A Server Nase Type: host name (0) Server Nase langth: 17 Server Nase enabled.tis13.com >Extension extended master secret (len) > Extensions renegotiation Info (1) > Extension supported groups (le-10) Extension: ec point formats (l2) traser Protocol STEP TOP TOR TL5E-3 TO TL541.3 TL5.5 TL5.3 TL5v4.3 TL5.3 TLSv. TOP TL54.3 TLSW.3 TOP TOP TOP Liv.3 Length 3r 4 23LE 443 [318] Sepi udin+64248 Len=8 P55+2448 HS-25E SACE PENI BE43 = 2316 (1, ACK] Seq- c220 L 155-1400-SACE_RER-4 54 2316-443 [ACK) Seq-1 Ack-1 Win-65536 Len- s87 client nell 044-2316 [ACK] Seq-1 Ack-554 vin-38720 L 266 Server Helle, Change Cipher Spec, Application Data 118 Change Cipher Spes, Application Data 14 Application Deta 152 Application Data IN A 520 Application Data 116Application Deta 54 2316 443 (ACK] Seq-1082 Ack-741-4768 Len 25 Application Data Application Drta 34 2328 443 (ACK) Sep-181 Ack-772 vi-4708 Lan 443-2316 [ACK] Seq-772 Ack-1982 -31744 Len- 0 443 2310 [ACK] Seq-772 Ack-1833 vi11744 Len ses Application Data Note that the server replies with its Hello message and then immediately begins transmitting encrypted data. The handshake is much shorter in TLS 1.3. Also note that the certificate is not present in the unencrypted data. The site https://www.ssllabs.com/ssltest/viewMyClient.html will test your browser to see what protocols it supports and let you know if your browser supports vulnerable protocols. Most likely your browser supports some outdated protocols so you can browse to sites that have not yet updated to secure protocols. 3) Does your browser support any insecure or weak protocols? What are they?
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


