Question
//CSE240 Fall 2018 HW3 // Enter your name here // State the IDE that you use: Visual Studio or GCC #include #include #pragma warning(disable :
//CSE240 Fall 2018 HW3
// Enter your name here // State the IDE that you use: Visual Studio or GCC
#include
#pragma warning(disable : 4996) // compiler directive for Visual Studio only
// Read before you start: // You are given a partially complete program. Your job is to complete the functions in order for this program to work successfully. // All instructions are given above the required functions, please read them and follow them carefully. // You shoud not modify the function return types or parameters. // You can assume that all inputs are valid. Ex: If prompted for an integer, the user will input an integer. // Note: DO NOT use pointers in this assignment. Pointer assignment will be given in the next homework.
// Global Macro Values. They are used to define the size of 2D array of characters #define NUM_STRINGS 4 #define STRING_LENGTH 35
// Forward Declarations void initializeStrings(char[NUM_STRINGS][STRING_LENGTH]); void swapFirstnameLastname(char strings[NUM_STRINGS][STRING_LENGTH]); void encryptStrings(char[NUM_STRINGS][STRING_LENGTH], int); void decryptStrings(char[NUM_STRINGS][STRING_LENGTH], int); void printStrings(char[NUM_STRINGS][STRING_LENGTH]); void inputMatrix(int matrixA[3][3]); void determinant(int matrixA[3][3]);
// Problem 1: initializeStrings (5 points) // Traverse the 2D array of characters variable 'strings' (input from user in main() ) and set all characters in each // array to a null terminator so that there is a 4 row and 35 column 2D array full of null terminators. // The null terminator is represented by the character value '\0' and is used to denote the end of a string. // This may come in use later in the program to know the end of string. void initializeStrings(char strings[NUM_STRINGS][STRING_LENGTH]) {
}
// Problem 2: printStrings (5 points) // Traverse the 2D character array "strings" and print each of the contained strings. // See the example outputs provided in the word document. Your output should match the example outputs. void printStrings(char strings[NUM_STRINGS][STRING_LENGTH]) {
}
// Problem 3: swapFirstnameLastname (15 points) // Swap the first name and last name in each string of the 2D char array. // In main(), the user will input the string as the first name followed by a space and followed by the last name. For eg- "John Doe". The user will input 4 such strings in "strings[][]". // In this function, swap the first name and last name (with a space between them) in each string of the 2D char array For eg- "Doe John" // Hint: Use a temp[35] char array to hold a copy of the string, find the space in the temp[] to identify the index of space which separates first and last name. // Using that index, overwrite the original string with last name in temp[] , followed by a space, followed by first name in temp[]. // Tip: Implement this function in a separate C file and work on a 1D char array before implementing for 2D char array in this file. void swapFirstnameLastname(char strings[NUM_STRINGS][STRING_LENGTH]) { char temp[35];
}
// Problem 4: encryptStrings (5 points) // Traverse the 2D character array 'strings' and encrypt each string in 2 steps as follows- // 1) In order to encrypt the 2D array of characters, we will first swap the last name and first name of the string. // Hint: Use 'swapFirstnameLastname()' for this step. // 2) Then we will shift those ASCII characters forward by the integer value of 'key'. // If the string is "hello" and key = 2, we will shift those characters forward in ASCII by 2 and the result will be "jgnnq". // Once the value of 'key' gets larger, you will extend past alphabetical characters and reach non-alphabetical characters. Thats ok.
// NOTE: DO NOT encrypt the null terminator character. Use the null terminators to find the end string. // *** NOTE: If you were unable to code for swapFirstnameLastname(), then skip that step in this function and simply shift the characters ahead by 'key'. // While decrypting in the next function, you will again have to skip the swapping part. You will get partial points in that case. void encryptStrings(char strings[NUM_STRINGS][STRING_LENGTH], int key) {
}
// Problem 5: decryptStrings (5 points) // HINT: This should be very similiar to the encryption function defined above in Problem 4. // Traverse the 2D character array 'strings' and decrypt each string in 2 steps as follows- // 1) We will shift those ASCII characters backward by the integer value of 'key'. // 2) Then we will swap the last name and first name of the string. // Hint: Use 'swapFirstnameLastname()' for this step. // *** NOTE: If you were unable to code for swapFirstnameLastname(), then skip that step in this function and simply shift the characters backward by 'key'. // You will get partial points in that case. void decryptStrings(char strings[NUM_STRINGS][STRING_LENGTH], int key) {
}
// Problem 6: inputMatrix (10 points) // Ask the user for each element of the 3X3 matrix and store the elements in "matrixA[][]" // Display the matrix in the following form: // matrixA = // 1 2 3 // 4 5 6 // 7 8 9 // The user may input any inetgers for matrix elements, not necessarily same as example above. void inputMatrix(int matrixA[3][3]) {
}
// Problem 7: determinant (5 points) // Calculate the determinant of the 3x3 matrix "matrixA[][]" and print it. // Read about how to caclualte the determinant of 3x3 matrix. Here is a video tutorial: https://www.khanacademy.org/math/algebra-home/alg-matrices/alg-determinants-and-inverses-of-large-matrices/v/finding-the-determinant-of-a-3x3-matrix-method-2 // Since it is strictly a 3x3 matrix, you may use hardcoded indices. For eg- matrixA[0][0] to access 1st element of the matrix void determinant(int matrixA[3][3]) {
}
// You should study and understand how this main() works. // *** DO NOT modify main() in any way *** int main() { char strings[NUM_STRINGS][STRING_LENGTH]; // will store four strings each with a max length of 34 int i, key; char input[STRING_LENGTH]; int matrixA[3][3]; // 3x3 int array for matrix printf("CSE240 HW3: 2D Character Arrays "); initializeStrings(strings); for (i = 0; i
i = getchar(); // remove the character ' ' i = getchar(); // keep console open. Needed in VS depending on how you execute. return 0; }
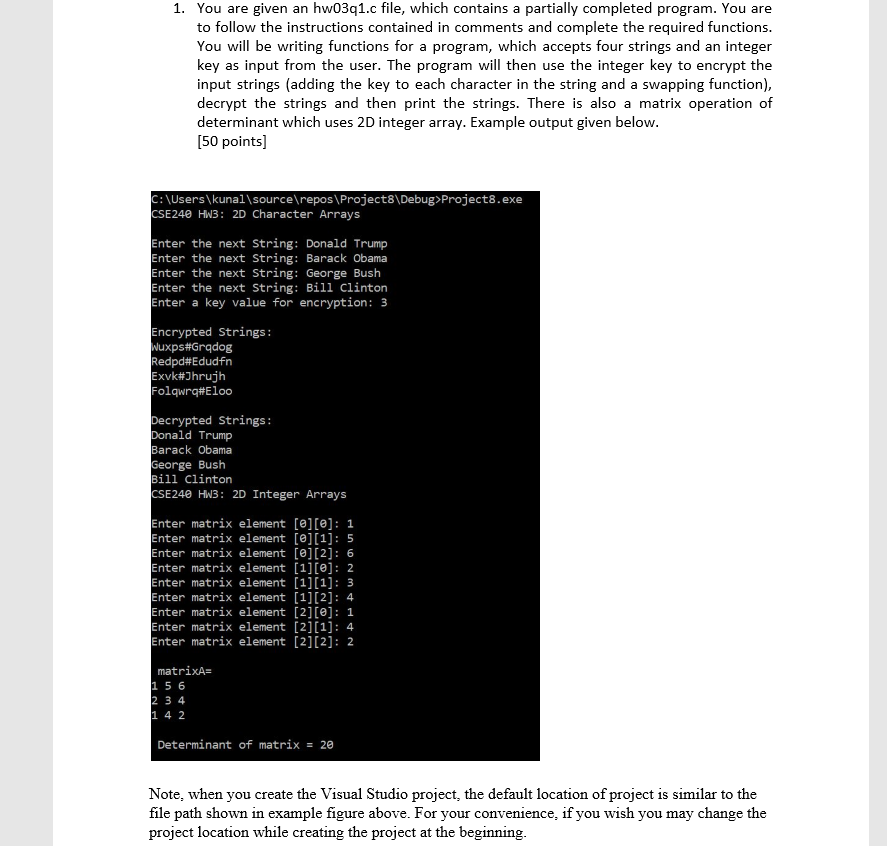
1. You are given an hw03q1.c file, which contains a partially completed program. You are to follow the instructions contained in comments and complete the required functions You will be writing functions for a program, which accepts four strings and an integer key as input from the user. The program will then use the integer key to encrypt the input strings (adding the key to each character in the string and a swapping function), decrypt the strings and then print the strings. There is also a matrix operation of determinant which uses 2D integer array. Example output given below [50 points] : \Users\kunal\source repos\Project8\Debug>Project8.exe SE240 HW3: 2D Character Arrays Enter the next String: Donald Trump Enter the next String: Barack Obama Enter the next String: George Bush Enter the next String: Bill Clinton Enter a key value for encryption: 3 Encrypted Strings RedpditEdudfn Exvk#7hrujh Folqwrq#5100 ecrypted Strings onald Trump Barack Obama eorge Bush Bill Clinton SE240 HW3 2D Integer Arrays Enter matrix element [ej[e]: 1 Enter matrix element [ej[1]: 5 Enter matrix element [e][2]: 6 Enter matrix element [1][e]: 2 Enter matrix element [11[1] 3 Enter matrix element [1][2]: 4 Enter matrix element [2][e]: 1 Enter matrix element [2]01]: 4 Enter matrix element [2][2]: 2 matrixA- 1 5 6 Determinant of matrix20 Note, when you create the Visual Studio project, the default location of project is similar to the file path shown in example figure above. For your convenience, if you wish you may change the project location while creating the project at the beginningStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


