Question: definitions for all operations you use. [5 marks] (b) State precisely what it means for a function f : N k ? N to be
definitions for all operations you use. [5 marks] (b) State precisely what it means for a function f : N k ? N to be ?-definable. [5 marks] (c) For each of the following functions, show (using the definitions you gave) that it is primitive recursive and ?-definable. (i) The function square : N ? N given by square(x) = x 2 . [4 marks] (ii) The function fact : N ? N given by fact(x) = x!. [4 marks] (d) Give a definition of a function that is ?-definable but not primitive recursive. [2 marks] 4 CST.2011.6.5 5 Logic and Proof (a) Recently, automated theorem provers based on the saturation algorithm have become very powerful tools. (i) Exhibit a proof by resolution of the following formula in first-order logic. Include the conversion into a set of clauses and provide brief justification for each step of the proof. ?x(P(x) ? Q(x)) ? (?yP(y) ? ?zQ(z))
(a) Name five different types of intellectual property.
(b) Distinguish between "Deep linking" and "Direct linking". Can a search engine
deep link without infringing the copyright of the original site?
(c) Why is the use of thumbnails of pictures by a search engine fair use?
(d) Why are there likely to be only a few dominant search engines?
14 E-Commerce
(a) In a telecommunications business context, what is meant by Triple and
Quadruple Play strategies, and what will be the effects of the adoption of
such strategies?
(b) Describe possible business models for a small independent Internet television
start-up company. Estimate start-up costs and profitability, and describe some
of the challenges such a television station will need to overcome.
(a) (i) Briefly describe the purpose of broadband fixed wireless access (FWA)
and give typical situations where it could be deployed.
(ii) What advantages does radio offer over traditional wired access?
(b) Explain how intersymbol interference (ISI) arises in a wireless communication
system and its effect on system performance.
(c) (i) Describe how
? linear equalisation
? orthogonal frequency division multiplexing (OFDM)
can be used to combat ISI. [4 marks]
(ii) Highlight a problem which can occur when using linear equalisation and
describe an alternative equalisation approach that can overcome this
problem. What problem can occur with this alternative approach?
(iii) Highlight problems that arise with the use of OFDM. In what situation
is OFDM preferred over the use of equalisation?
(a) Describe, with examples, the function of a naming service for a largescale distributed system. Include definitions for "name space" and "naming
domain".
(b) Discuss consistency versus availability for naming data in large-scale systems.
(c) How can any distributed naming service be engineered so that invocations on
behalf of users can be resolved efficiently in the presence of failures and heavy
load?
(d) Contrast the assumptions under which DNS was designed originally for the
Internet, with the properties of dynamically formed groups of mobile hosts
using wireless communication (MANETS). How might DNS-like services be
provided for MANETS?
5 Advanced Systems Topics
Modern peer-to-peer (P2P) systems are typically described as structured or
unstructured.
(a) Compare and contrast these two approaches. Include a discussion of the
general topology, membership management and query mechanisms. Use
examples to support your answer.
(b) Which approach is more resilient to churn? Justify your answer.
(c) One early criticism of P2P systems was that they did not consider network
latencies. Describe how one can add proximity awareness to:
(i) unstructured P2P systems
(ii) structured P2P systems.
(d) Swarming P2P systems like BitTorrent are designed for efficient (and incentive
compatible) download of large files. However, it is typically not possible to use
the file until it has downloaded in its entirety. Sketch the design of a swarming
P2P system which supports streaming video - that is, allows playback of video
to overlap the ongoing download of the remainder of the stream. Comment
on how efficient (in terms of network resources) your system would be in
comparison with a system like BitTorrent
Some banks issue their Automatic Teller Machine (ATM) card customers with
a randomly selected personal indentification number (PIN). Others issue their
customers with an initial PIN only, and let the customers choose their own PIN the
first time they use the card in an ATM. Describe the advantages and disadvantages
of these approaches. [5 marks]
Again, some banks compute the customer PIN by encrypting the account number
using DES and a key known only to their central systems and ATMs, taking the first
four hex digits of the result, replacing the digits A, . . . , F with 0, . . . , 5 respectively,
and finally, if the first digit of the result is 0, replacing it with a 1. What is the
probability that a criminal can get the PIN right given three guesses? [5 marks]
Yet other banks have used DES, and a key known only to their central systems and
ATMs, to encrypt the PIN (whether randomly generated or customer selected); they
then write the result on the magnetic strip on the customer's card, so that the ATM
can verify it without reference to the central system. Describe the disadvantages
of this arrangement. [5 marks]
In order to prevent attacks based on manipulating magnetic strips, banks in some
countries have moved to using smart cards. What effect would you expect such a
move to have on the incidence of card-based fraud? [5 marks]
5 [TURN OVER
CST.98.12.6
7 Compiler Construction
Explain how a parse-tree representation of a program may be converted into a
stack-based intermediate language giving sketches of code to translate expressions,
assignments and the if-then-else command; you should also explain how
occurrences of a variable in an expression or assignment are translated.
The program may be assumed to conform to the following syntax:
E -> n | x | E + E | f(E,E)
D -> let f(x,x) = {Dseq; Cseq; E} | let x = E
C -> x := E; | if E then C else C
Cseq -> C | C Cseq
Dseq -> D | D Dseq
with start symbol Dseq. Here n corresponds to integer constants, x corresponds to
identifiers used as variable names and f corresponds to identifiers used as function
names (you may assume these are disjoint)
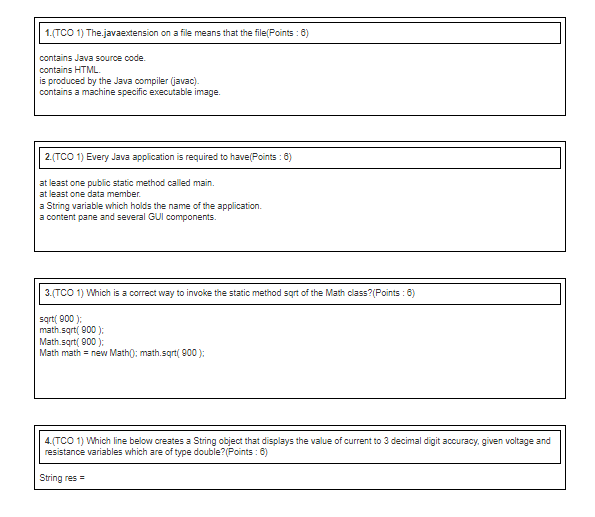

1.(TCO 1) The.javaextension on a file means that the file(Points: 6) contains Java source code. contains HTML. is produced by the Java compiler (javac). contains a machine specific executable image. 2.(TCO 1) Every Java application is required to have(Points: 6) at least one public static method called main. at least one data member. a String variable which holds the name of the application. a content pane and several GUI components. 3.(TCO 1) Which is a correct way to invoke the static method sqrt of the Math class? (Points: 6) sqrt(900); math.sqrt(900); Math.sqrt(900); Math math= new Math(); math.sqrt( 900); 4.(TCO 1) Which line below creates a String object that displays the value of current to 3 decimal digit accuracy, given voltage and resistance variables which are of type double? (Points: 6) String res=
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


