Answered step by step
Verified Expert Solution
Question
1 Approved Answer
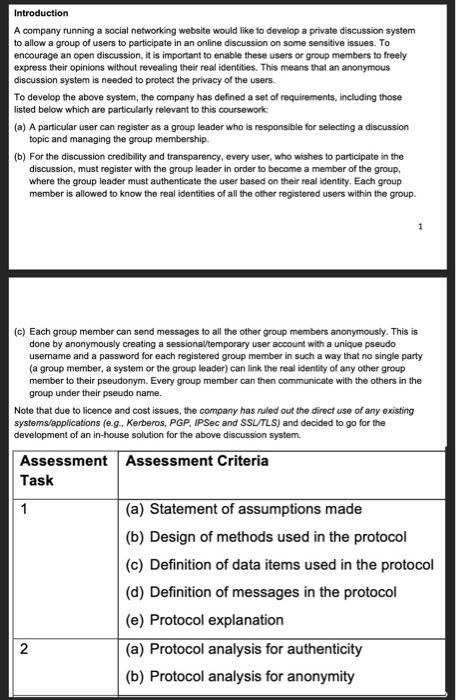
Detail of the task You are required to participate in the design of the anonymous discussion system described above in the Introduction section. You can
Detail of the task
You are required to participate in the design of the anonymous discussion system described above in the Introduction section. You can assume the availability of any cryptosystems you need for the design, and document all the results obtained from each of the following tasks assigned to you:
1. Propose a communication protocol for the group membership registration and anonymous account creation for a user, and describe what assumptions you have made and how the proposed protocol operates.
Note that the protocol should consist of messages transferred step by step between different parties/entities involved, where the details of all the data items sent in each message must be clearly defined.
You can assume that there exists a trusted server for assistance in the process of anonymous user account creation, but the server must not be able to link the pseudo username of an anonymous account to the real identity of its associated group member.
2. Analyse the security of your proposed protocol in detail to show how the protocol achieves the following security properties:
Authenticity described in requirement (b) in the Introduction section, including the authenticity of each protocol message, and
Anonymity stated in requirement (c) in the Introduction section.
notes :
- Your assumptions cannot compromise/weaken the authenticity and anonymity requirements stated.
- design by yourself how you achieve confidentiality, authenticity and anonymity using only asymmetric/symmetric crypto algorithms
- the protocol needs to satisfy both the authenticity and anonymity requirements.
- You need to define your protocol messages in a style similar to the one used by the Kerberos protocol. You need to define the messages of your own protocol using notations, not just descriptions. Have a look at the Kerberos protocols.
-If an encryption is used, all its inputs including the key used must be clearly defined.
** please follow the notes **
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


