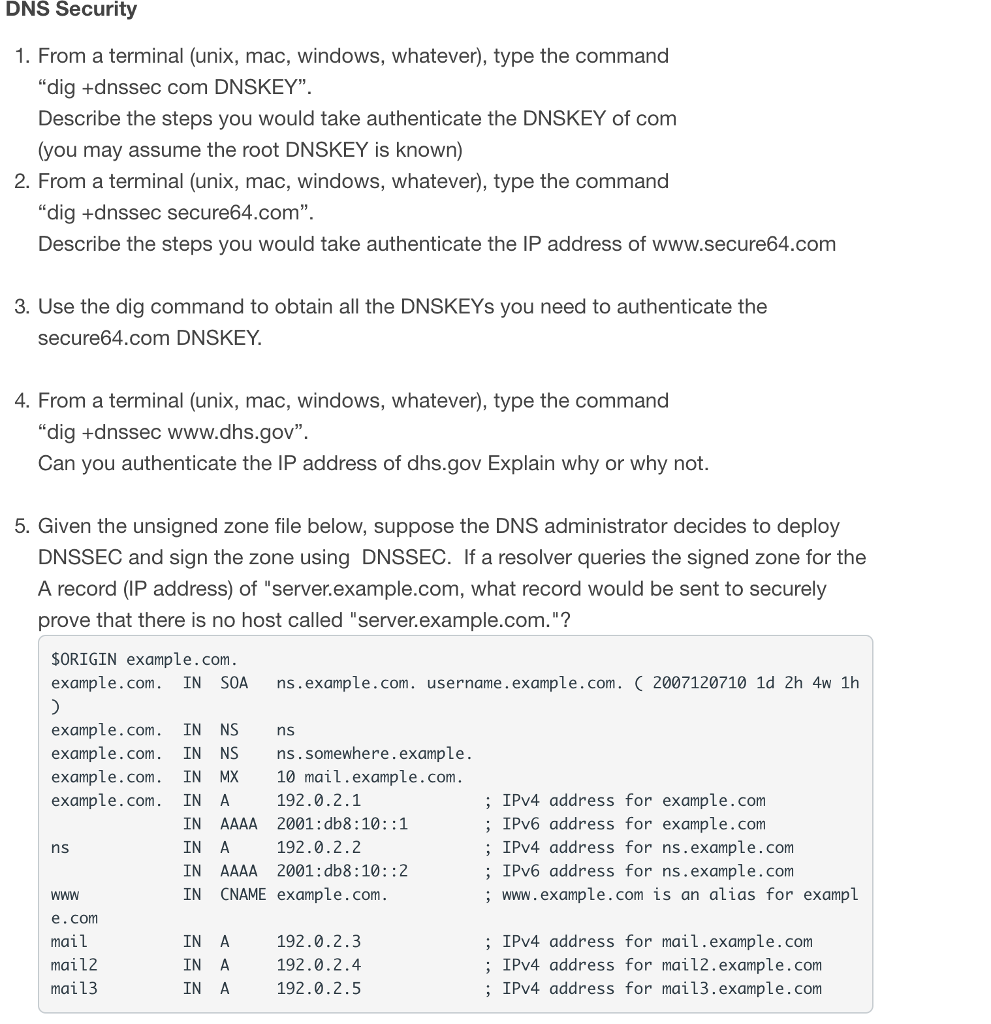
DNS Security 1. From a terminal (unix, mac, windows, whatever), type the command "dig +dnssec com DNSKEY". Describe the steps you would take authenticate the DNSKEY of conm (you may assume the root DNSKEY is known) 2. From a terminal (unix, mac, windows, whatever), type the command "dig +dnssec secure64.com". Describe the steps you would take authenticate the IP address of www.secure64.com 3. Use the dig command to obtain all the DNSKEYs you need to authenticate the secure64.com DNSKEY 4. From a terminal (unix, mac, windows, whatever), type the command "dig +dnssec www.dhs.gov". Can you authenticate the IP address of dhs.gov Explain why or why not. 5. Given the unsigned zone file below, suppose the DNS administrator decides to deploy DNSSEC and sign the zone using DNSSEC. If a resolver queries the signed zone for the A record (IP address) of "server.example.com, what record would be sent to securely prove that there is no host called "server.example.com."? SORIGIN example.com example.com. IN SOA ns.example.com. username.example.com.C 2007120710 1d 2h 4w 1h example.com IN NS ns example.com. IN NS ns.somewhere.example. example.com. IN MX 10 mail.example.com. example.com. IN A 192.0.2.1 IN AAAA 2001:db8:10::1 IN A IN AAAA 2001:db8:10::2 IN CNAME example.com ; IPv4 address for example.com ; IPv6 address for example.com ; IPv4 address for ns.example.com ; IPv6 address for ns.example.com ; www.example.com is an alias for exampl ns 192.0.2.2 WWw e.com mail mail2 mail3 IN A IN A IN A 192.0.2.3 192.0.2.4 192.0.2.5 ; IPv4 address for mail.example.com ; IPv4 address for mail2.example.com ; IPv4 address for mail3.example.com DNS Security 1. From a terminal (unix, mac, windows, whatever), type the command "dig +dnssec com DNSKEY". Describe the steps you would take authenticate the DNSKEY of conm (you may assume the root DNSKEY is known) 2. From a terminal (unix, mac, windows, whatever), type the command "dig +dnssec secure64.com". Describe the steps you would take authenticate the IP address of www.secure64.com 3. Use the dig command to obtain all the DNSKEYs you need to authenticate the secure64.com DNSKEY 4. From a terminal (unix, mac, windows, whatever), type the command "dig +dnssec www.dhs.gov". Can you authenticate the IP address of dhs.gov Explain why or why not. 5. Given the unsigned zone file below, suppose the DNS administrator decides to deploy DNSSEC and sign the zone using DNSSEC. If a resolver queries the signed zone for the A record (IP address) of "server.example.com, what record would be sent to securely prove that there is no host called "server.example.com."? SORIGIN example.com example.com. IN SOA ns.example.com. username.example.com.C 2007120710 1d 2h 4w 1h example.com IN NS ns example.com. IN NS ns.somewhere.example. example.com. IN MX 10 mail.example.com. example.com. IN A 192.0.2.1 IN AAAA 2001:db8:10::1 IN A IN AAAA 2001:db8:10::2 IN CNAME example.com ; IPv4 address for example.com ; IPv6 address for example.com ; IPv4 address for ns.example.com ; IPv6 address for ns.example.com ; www.example.com is an alias for exampl ns 192.0.2.2 WWw e.com mail mail2 mail3 IN A IN A IN A 192.0.2.3 192.0.2.4 192.0.2.5 ; IPv4 address for mail.example.com ; IPv4 address for mail2.example.com ; IPv4 address for mail3.example.com







