Answered step by step
Verified Expert Solution
Question
1 Approved Answer
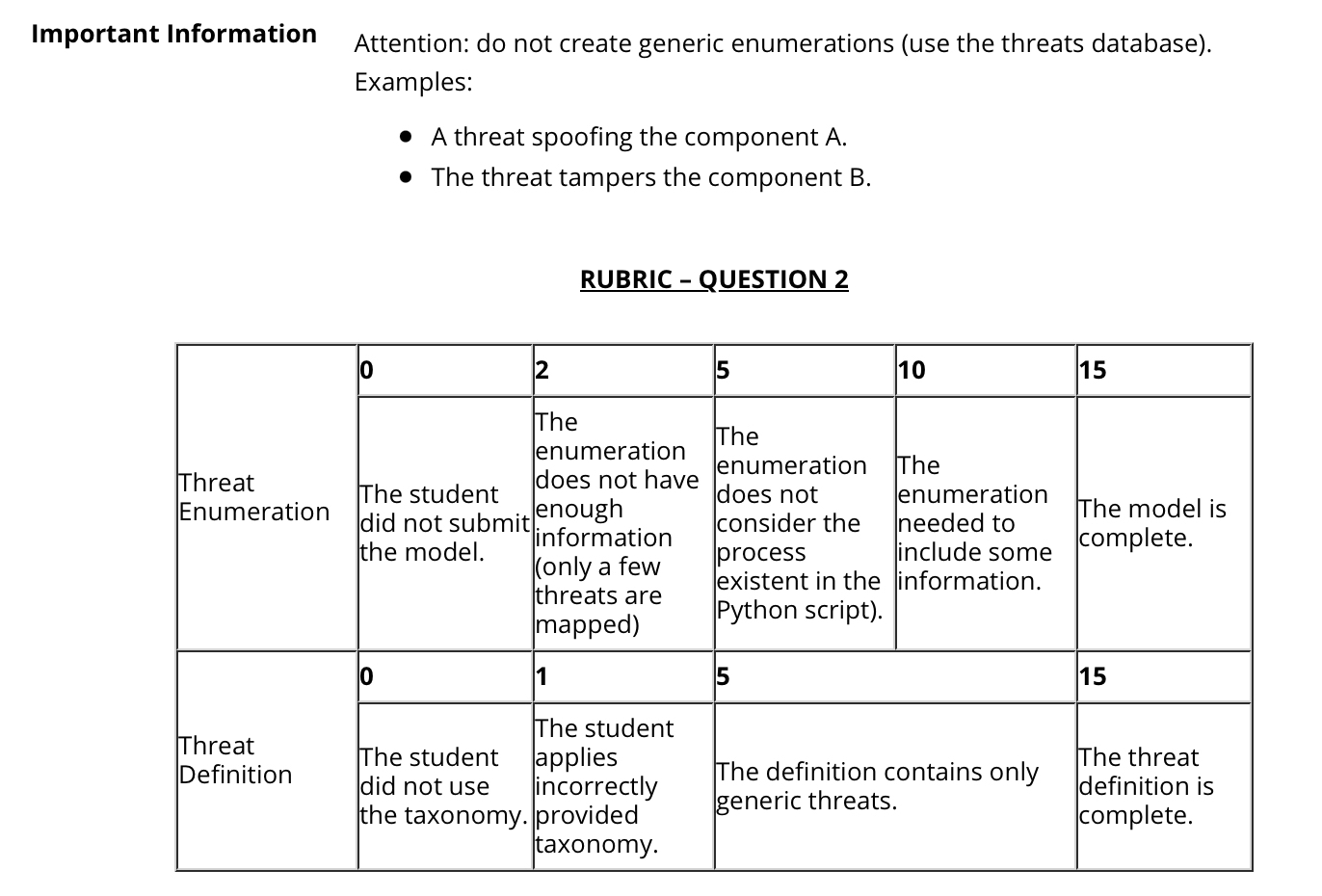
Enumerate the feasible threats of the MFA system using STRIDE. To perform this task, remember to use the method toughed in the class:Before starting the
Enumerate the feasible threats of the MFA system using STRIDE. To perform this task, remember to use the method toughed in the class:Before starting the enumeration, it is important to check the assumptions and previous information about the system and the problem. A good read of the DFD and the requirements is essential.Search on the Internet for the feasible threats of the MFA components.Create a list of your system's objects processes entities, data stores, etc. and analyze them one by one using STRIDE strength and weaknessUse STRIDE per Element to support the analysis.Use not copy a Threat database CAPEC CWE, NVD etc. to help you to understand and describe the threat. Tips: When in doubt, try to understand which security property is affected by exploiting the threat to check the STRIDE type. Deliverable: The questions deliverable is the table filled with the threat enumeration using the taxonomy provided in the class. Threat definition using the taxonomy providedSTRIDE classificationEntity in the DFD
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


