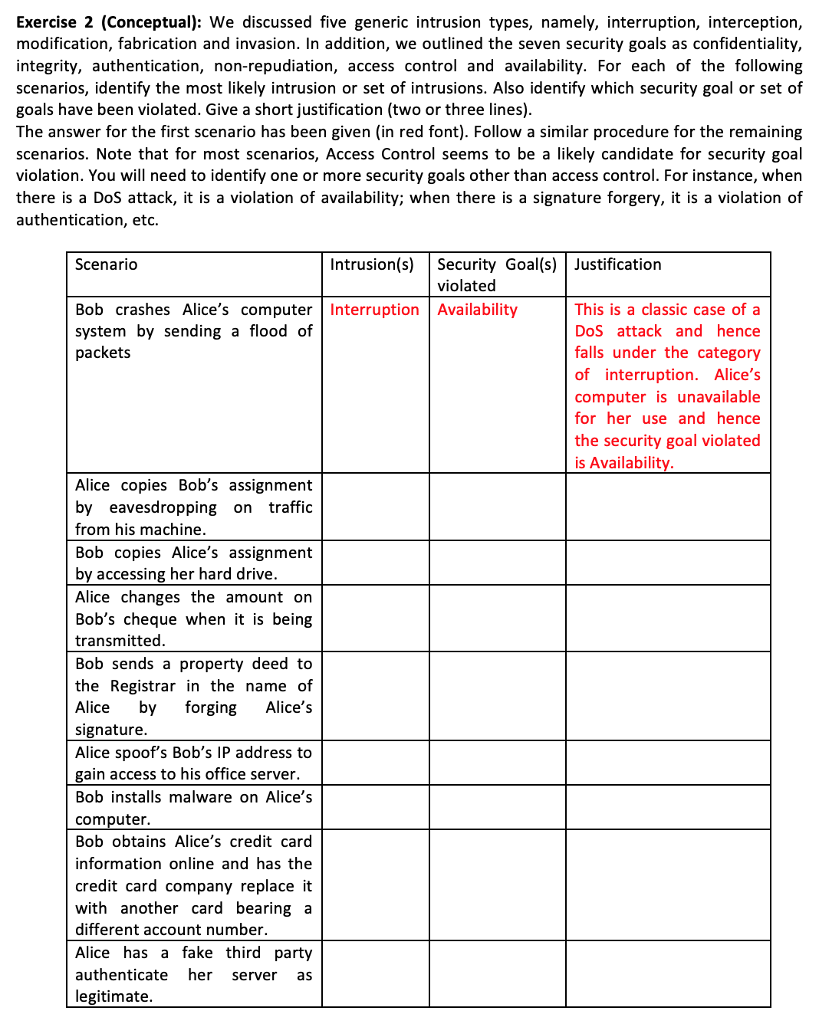
Exercise 1 (Exploratory): www.sectools.org offers a rich catalogue of network security tools, including their classification, ratings, links to the tool's website and reviews. Visit the website and pick one network security tool. Ensure that you select a tool that is used for ethical hacking and network administration Conduct an exploration of the tool and write a report summarizing the tool. In your report, describe the tool's features, what it provides, and how it works. Also outline how it is useful to a network security specialist and how it may be used for harmful purposes by a hacker Length of the report: Approximately 2 pages, single line spacing, 11-point font size. Figures may be part of the 2-page report. However, if figures occupy more than half a page, put the extra figures in an appendix. Referencing your work: If you are using only www.sectools.org as your reference, then no need to cite it since it has already been provided to you. If you explore other sources, please cite them Exercise 2 (Conceptual): We discussed five generic intrusion types, namely, interruption, interception, modification, fabrication and invasion. In addition, we outlined the seven security goals as confidentiality, integrity, authentication, non-repudiation, access control and availability. For each of the following scenarios, identify the most likely intrusion or set of intrusions. Also identify which security goal or set of goals have been violated. Give a short justification (two or three lines) The answer for the first scenario has been given (in red font). Follow a similar procedure for the remaining scenarios. Note that for most scenarios, Access Control seems to be a likely candidate for security goal violation. You will need to identify one or more security goals other than access control. For instance, when there is a DoS attack, it is a violation of availability; when there is a signature forgery, it is a violation of authentication, etc. Scenario Intrusion(s)Security Goal(s) Justification violated Bob crashes Alice's computer Interruption Availability system by sending a flood of packets This is a classic case of a DoS attack and hence falls under the category of interruption. Alice's computer is unavailable for her use and hence the security goal violated is Availabilit Alice copies Bob's assignment by eavesdropping on traffic from his machine Bob copies Alice's assignment by accessing her hard drive Alice changes the amount on Bob's cheque when it is being transmitted Bob sends a property deed to the Registrar in the name of Alice by forging Alice's signature Alice spoof's Bob's IP address to gain access to his office server Bob installs malware on Alice's computer Bob obtains Alice's credit card information online and has the credit card company replace it with another card bearing a different account number Alice has a fake third party authenticate her server a legitimate








