
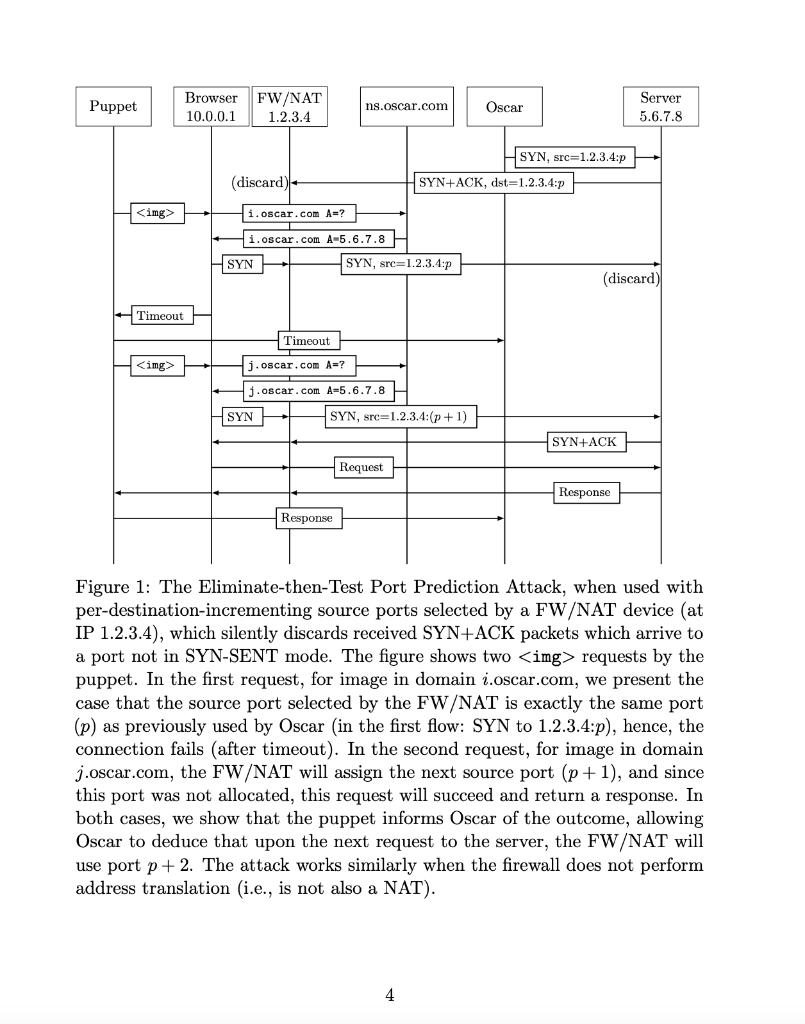
Exercise 3 (The Eliminate-then-Test port prediction attack). The Eliminatethen-Test port prediction attack, as presented in Fig. 1, can only test if x, the next port that the client would use to connect to specific server S, is equal to the 'test port' p. However, the figure does not show how to handle the case where the next client port x is not p. Complete the missing details: 1. Show sequence diagram for how to continue the attack and find the next port x, as a 'naive' extension of the shown attack, when the guess p is not correct, i.e., p=x. 2. We also discussed the 'haunted mansion game optimized' attack, where Oscar sends multiple spoofed SYN packets, to 'eliminate' multiple client (source) ports p1,p2,pn. Assume that Oscar can send thus 'eliminate' up to 64 ports, after which, the server would ignore new SYN packets from this source IP address. Which port numbers p1,p2,pn should Oscar 'eliminate'? 3. What would be good choice for the domain names in the img tags? Explain why and how this would work for the attack. Note/hint: modern browsers send multiple requests to the same server over the same connection, rather than open a new connection for each request (to the same server domain). 4. Explain how the attacker completes the attack and finds the next port that the client would use in a connection to the server. Note: assume that the client uses per-destination incrementing source port numbers. Figure 2: TLS 1.3 1-RTT full Diffie-Hellman handshake Figure 1: The Eliminate-then-Test Port Prediction Attack, when used with per-destination-incrementing source ports selected by a FW/NAT device (at IP 1.2.3.4), which silently discards received SYN+ACK packets which arrive to a port not in SYN-SENT mode. The figure shows two requests by the puppet. In the first request, for image in domain i.oscar.com, we present the case that the source port selected by the FW/NAT is exactly the same port (p) as previously used by Oscar (in the first flow: SYN to 1.2.3.4:p), hence, the connection fails (after timeout). In the second request, for image in domain j.oscar.com, the FW/NAT will assign the next source port (p+1), and since this port was not allocated, this request will succeed and return a response. In both cases, we show that the puppet informs Oscar of the outcome, allowing Oscar to deduce that upon the next request to the server, the FW/NAT will use port p+2. The attack works similarly when the firewall does not perform address translation (i.e., is not also a NAT)








