Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Explain the following Threats in networks Session hijacking TCP sessions TCP protocol sets up state at sender and receiver end nodes and uses this state
Explain the following 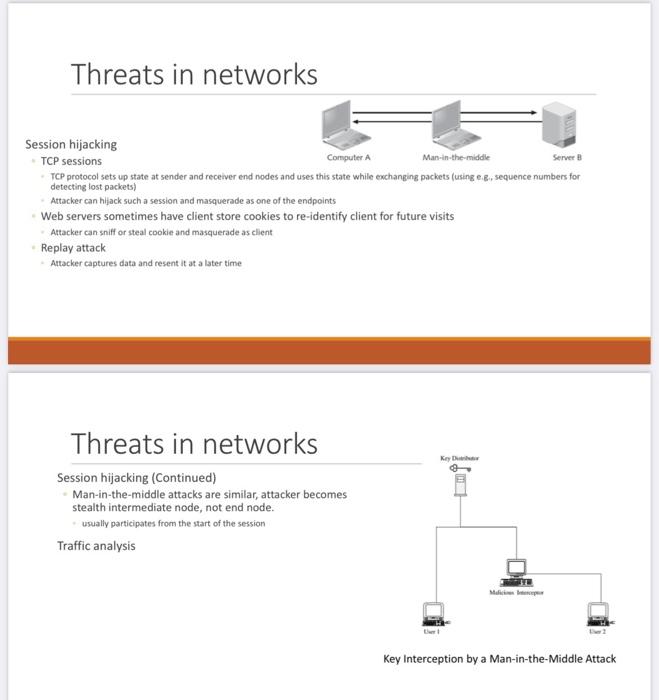
Threats in networks Session hijacking TCP sessions TCP protocol sets up state at sender and receiver end nodes and uses this state while exchanging packets (using e.g. sequence numbers for detecting lost packets) Attacker can hijack such a session and masquerade as one of the endpoints Web servers sometimes have client store cookies to re-identify client for future visits Attacker can sniff or steal cookie and masquerade as client Replay attack Attacker captures data and resent it at a later time Threats in networks Session hijacking (Continued) Man-in-the-middle attacks are similar, attacker becomes stealth intermediate node, not end node. usually participates from the start of the session Traffic analysis Key Interception by a Man-in-the-Middle Attack 
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


