Answered step by step
Verified Expert Solution
Question
1 Approved Answer
first three pics is detail of question and fourth pic is all 6 points answer them please within 30mins these are detail of question ignore
first three pics is detail of question and fourth pic is all 6 points answer them please within 30mins
these are detail of question

ignore all the pics and just answer this matching table

just check last pic and do that
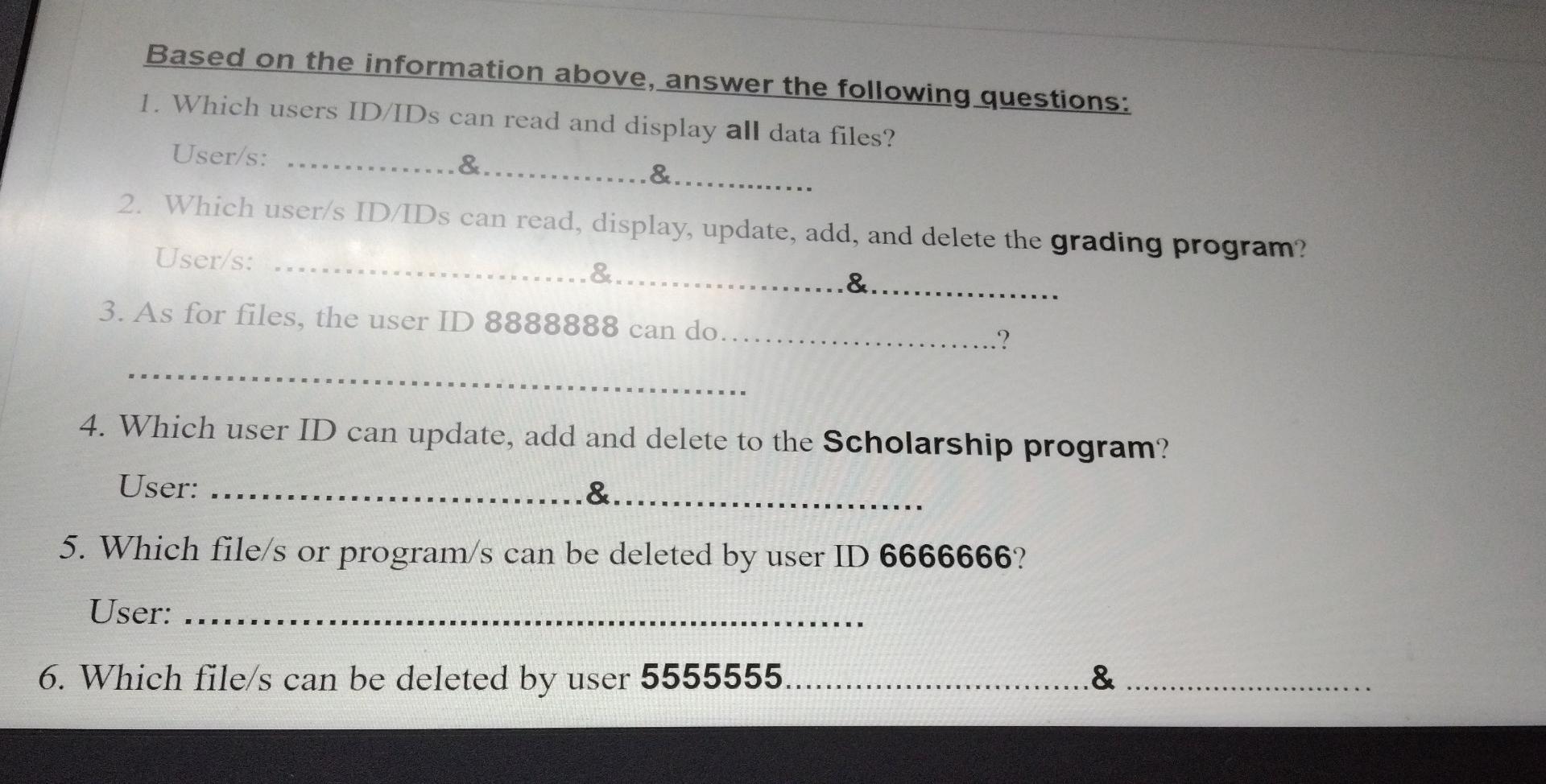
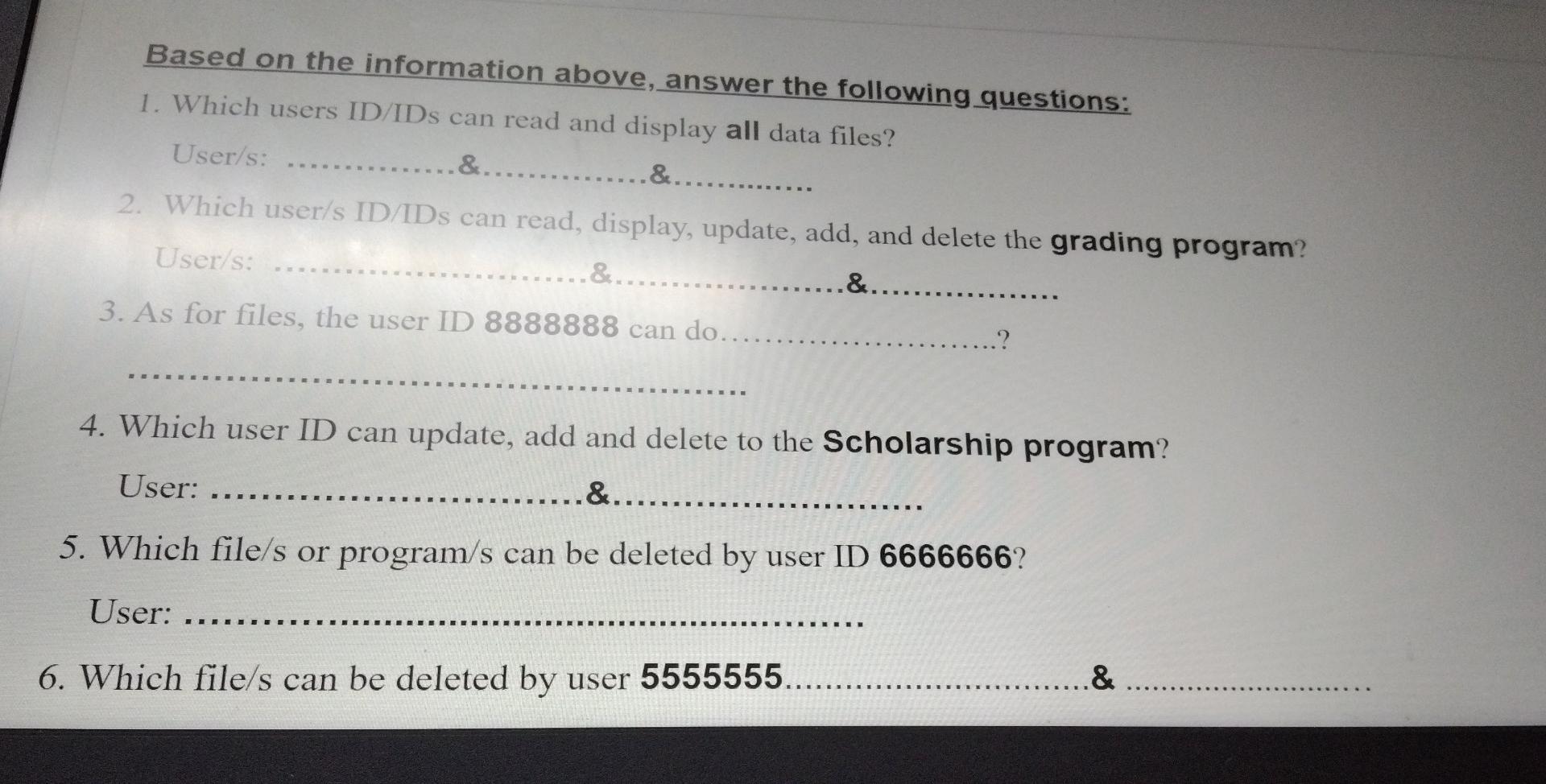
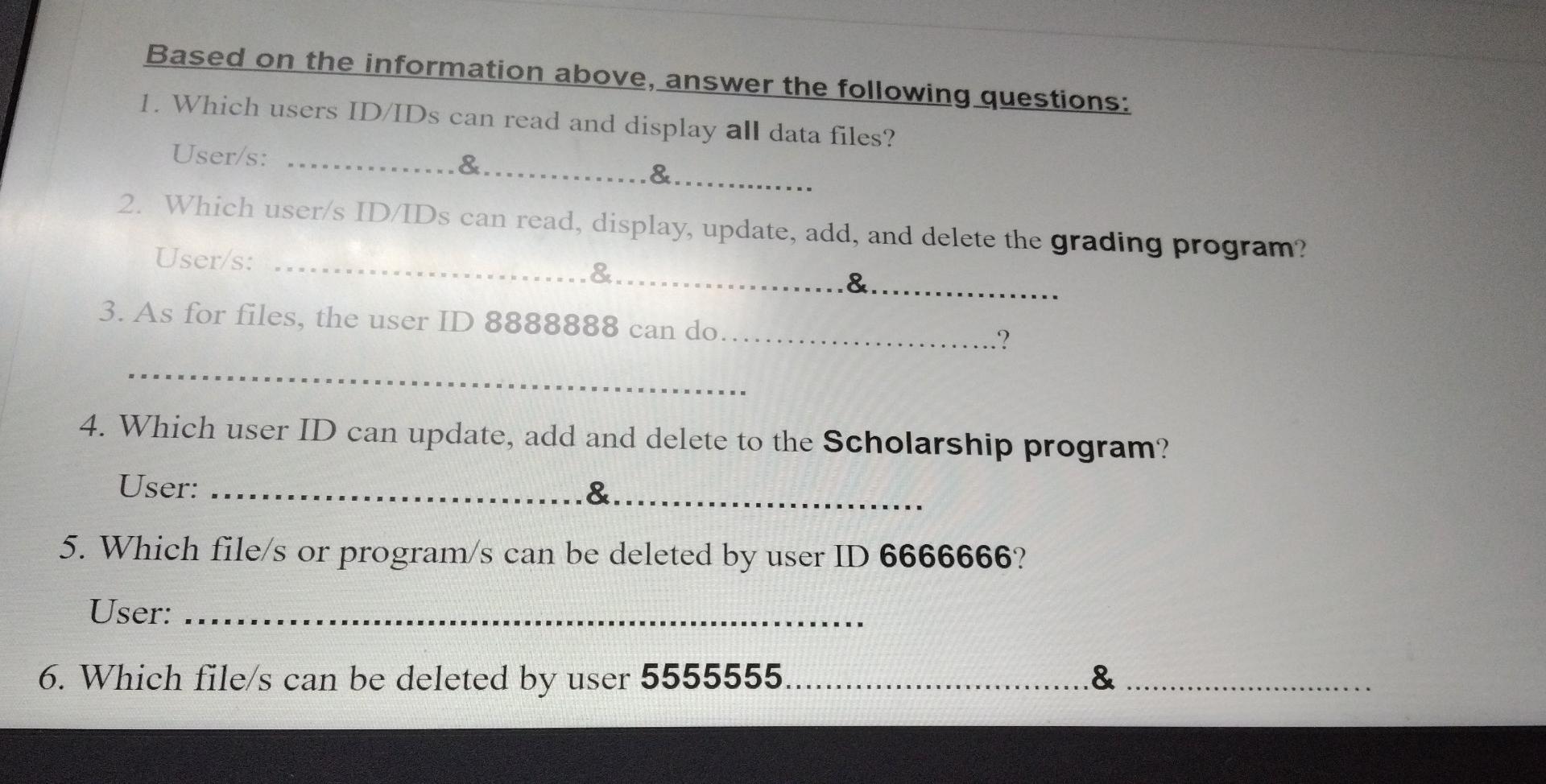
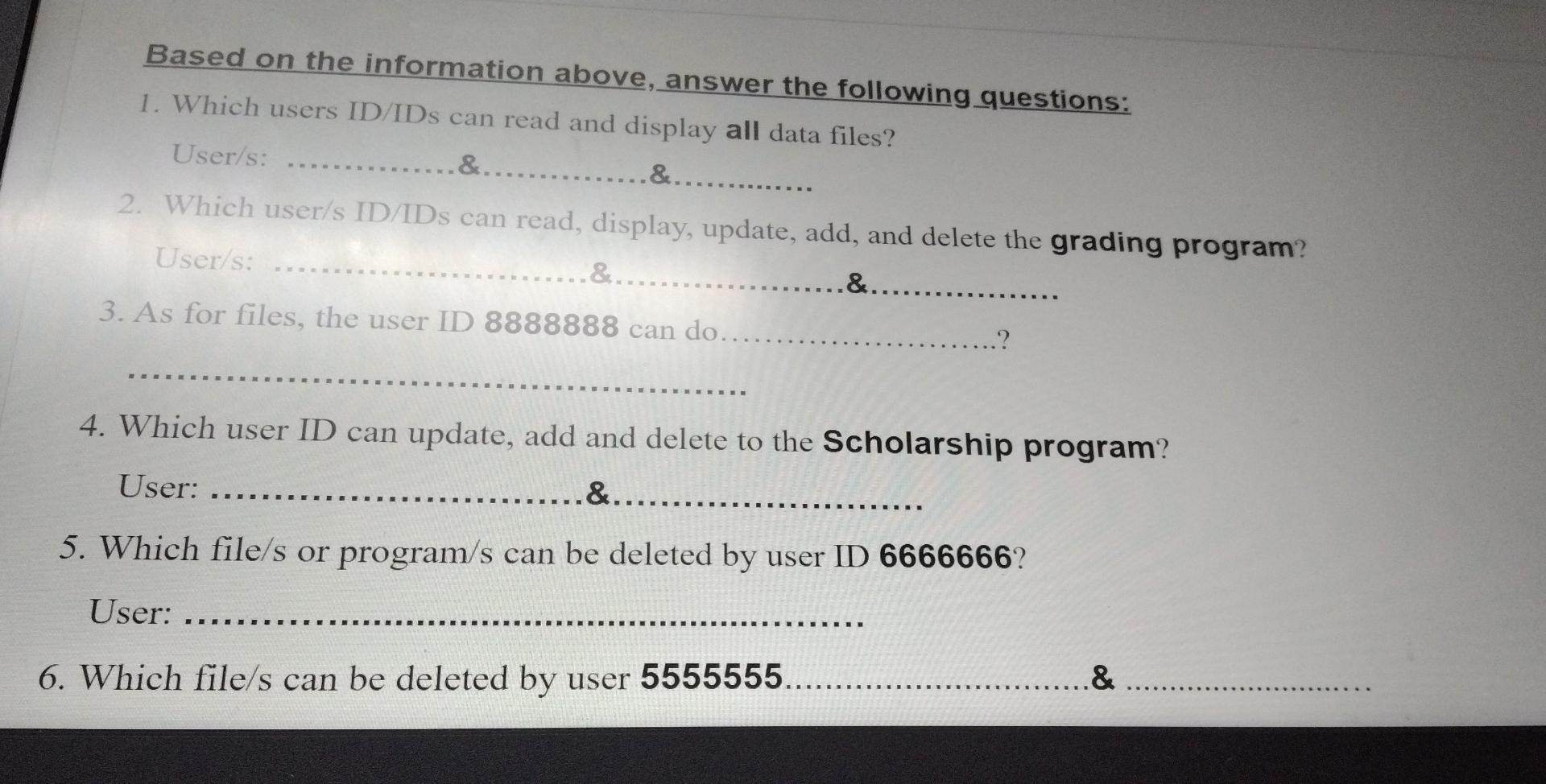
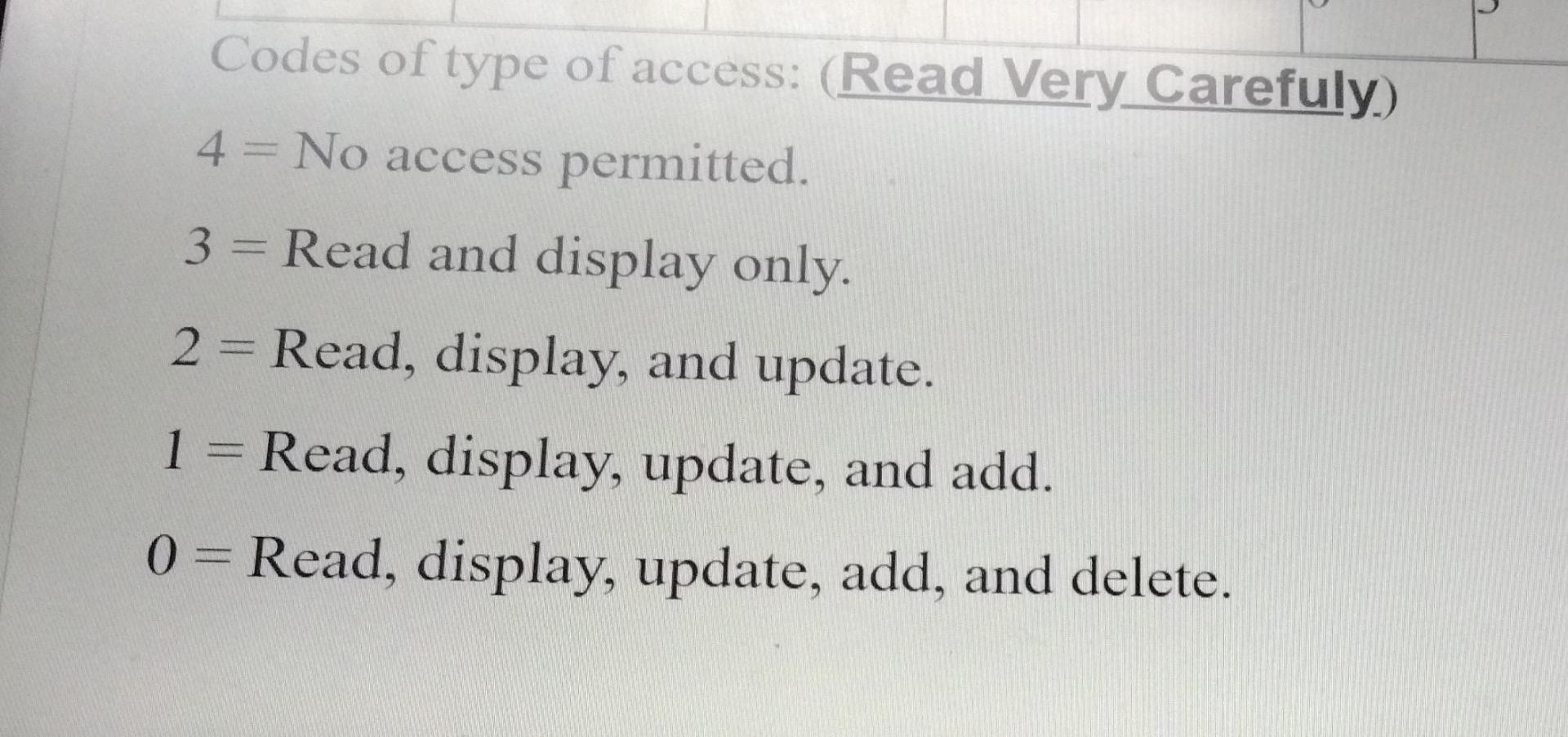
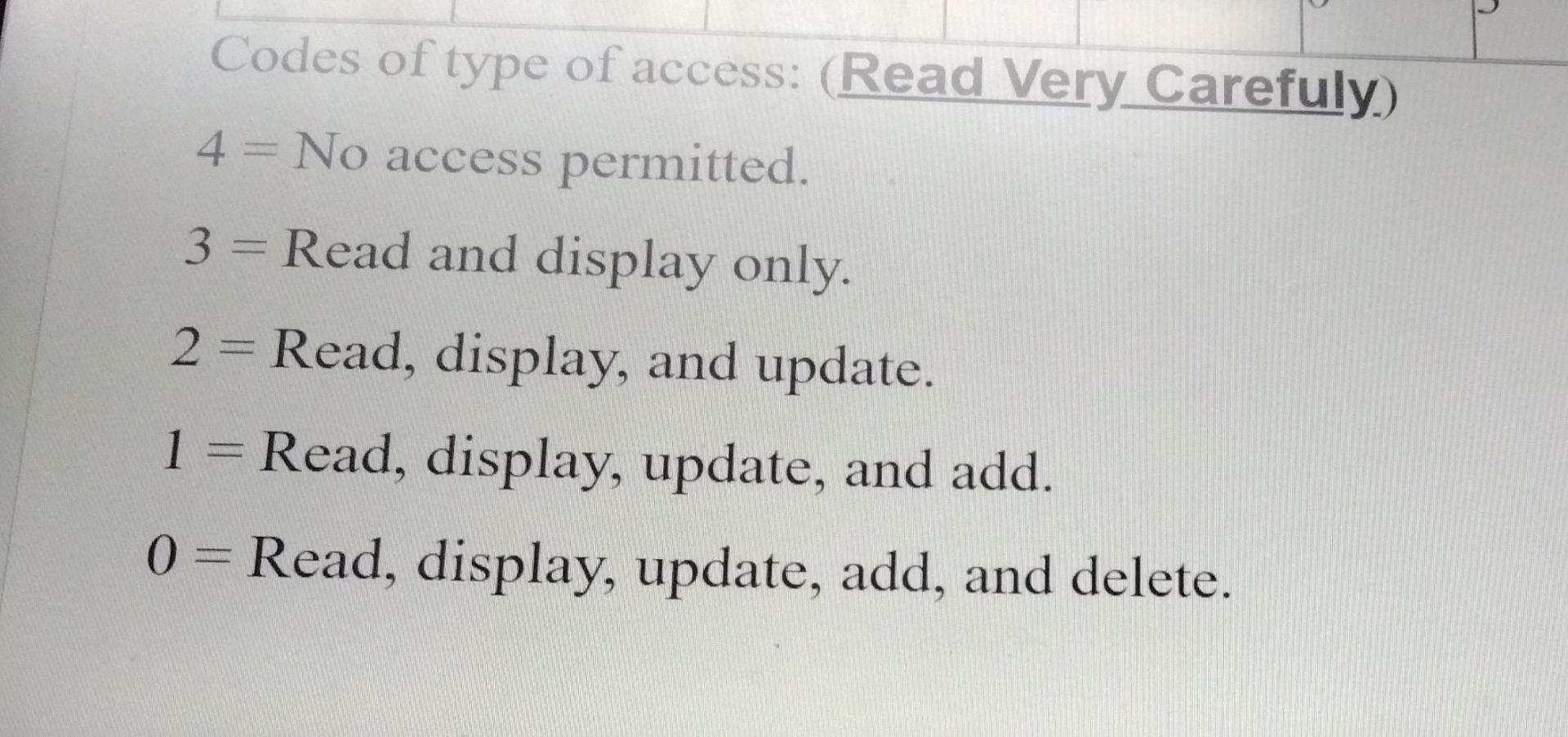
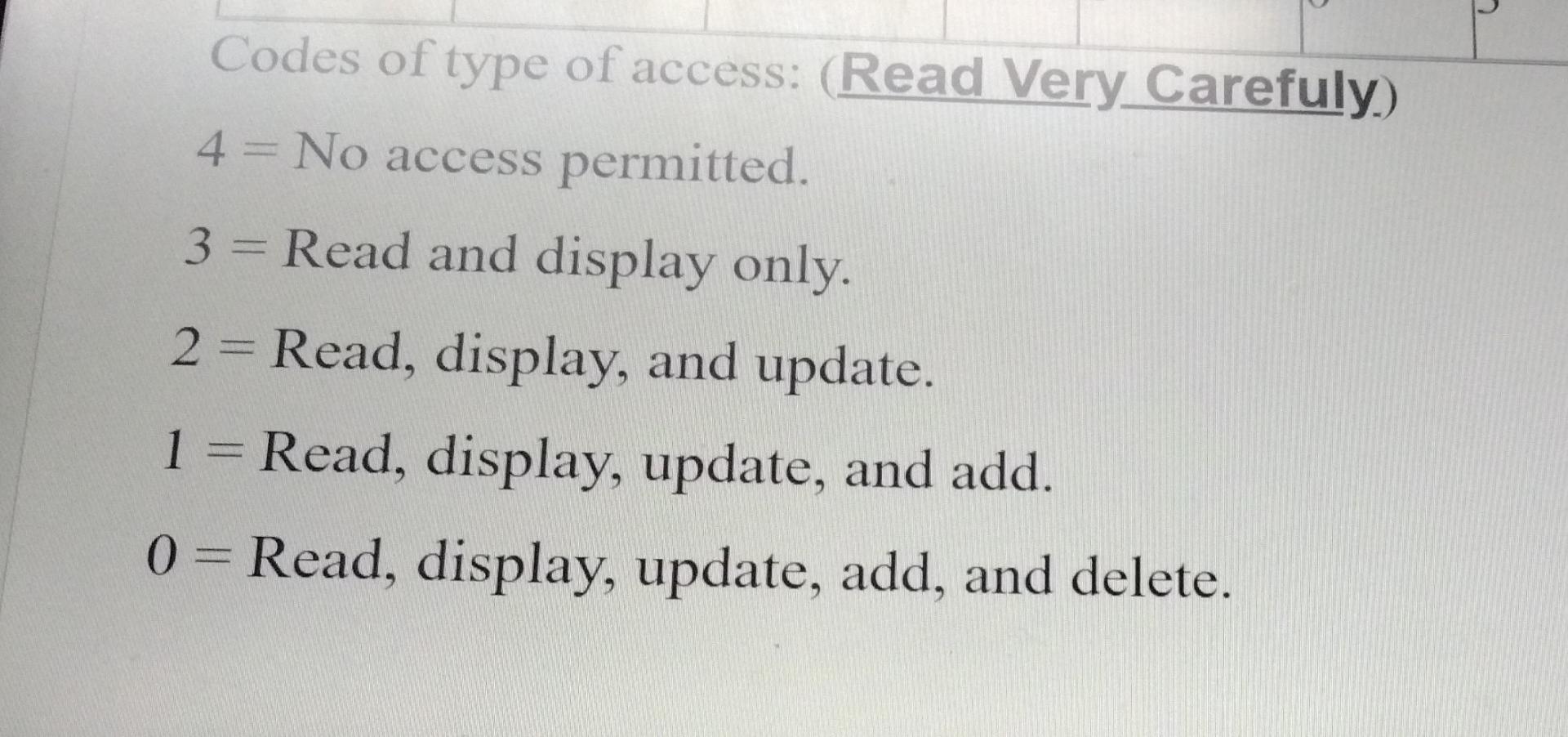
Based on the information above, answer the following questions: 1. Which users ID/IDS can read and display all data files? User/s: ... &......... &..... 2. Which user/s ID/IDS can read, display, update, add, and delete the grading program? User/s: &.. .&........ 3. As for files, the user ID 8888888 can do... 4. Which user ID can update, add and delete to the Scholarship program? User: &......... 5. Which file/s or program/s can be deleted by user ID 6666666? User: E & 6. Which file/s can be deleted by user 5555555... ........ Codes of type of access: (Read Very Carefuly) 4 = No access permitted. 3 = Read and display only. 2 = Read, display, and update. 1 = Read, display, update, and add. 0 = Read, display, update, add, and delete. 2 Codes of type of access: (Read Very Carefuly) 4 = No access permitted. 3 = Read and display only. 2 = Read, display, and update. 1 = Read, display, update, and add. 0 = Read, display, update, add, and delete. 2 Codes of type of access: (Read Very Carefuly) 4 = No access permitted. 3 = Read and display only. 2 = Read, display, and update. 1 = Read, display, update, and add. 0 = Read, display, update, add, and delete. 2 Authorization controls are implemented by creating an access control matrix, which specifies what part of the IT System a user can access and what actions they are permitted to perform. When an employee tries to access a particular resource, the It System performs a compatibility test that matches the user's authentication credentials against the matrix to determine if the action should be allowed. The following is an access control matrix for files and programs at Bahrain Company. (6 Points) Match each of the following statements with the appropriate concept/term provided for you. use all the available concepts. Note that you will not Access to the system and its data is controlled. A. Move ticket Sensitive information is protected from unauthorized disclosure. B. Master production schedule C.Security A high technology (robots) used as a part of the production process. D. Reliability E. Receiving Report F. Attempt to minimize or eliminate inventory by purchasing or producing only in response to actual sales. Computer-integrated manufacturing (CIM) G. JIT System H.Confidentiality Is the primary document used to document the date goods received, shipper, supplier, PO number, item number, description, unit of measure, and quantity for each item. 1. Operations List Radio-Frequency IDentification Lists the sequence of steps required to produce each product, including the equipment needed and theStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


