Answered step by step
Verified Expert Solution
Question
1 Approved Answer
For each of the following protocols between Alice - a human client - and Bob - a server - decide, whether the protocol is doable,
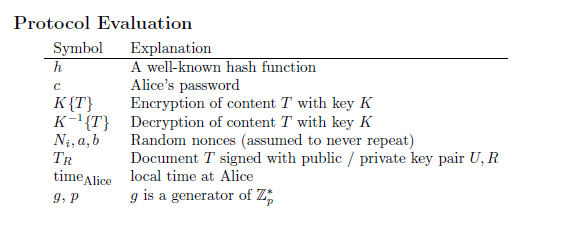 For each of the following protocols between Alice - a human client - and Bob - a server - decide, whether the protocol is doable, whether it actually authenticates the other party, and whether it is vulnerable to a 1. replay attack 2. reflection attack 3. dictionary attack by (a) somebody snooping (b) somebody impersonating Alice (c) somebody impersonating Bob 4. impersonation of Alice 5. impersonation of Bob
For each of the following protocols between Alice - a human client - and Bob - a server - decide, whether the protocol is doable, whether it actually authenticates the other party, and whether it is vulnerable to a 1. replay attack 2. reflection attack 3. dictionary attack by (a) somebody snooping (b) somebody impersonating Alice (c) somebody impersonating Bob 4. impersonation of Alice 5. impersonation of Bob 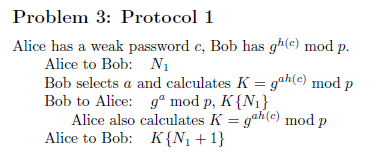
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


