Answered step by step
Verified Expert Solution
Question
1 Approved Answer
For Figure 3.13 below which represent how two users, A & B, can exchange a secret key using the Diffie-Hellman Key Exchange algorithm, show
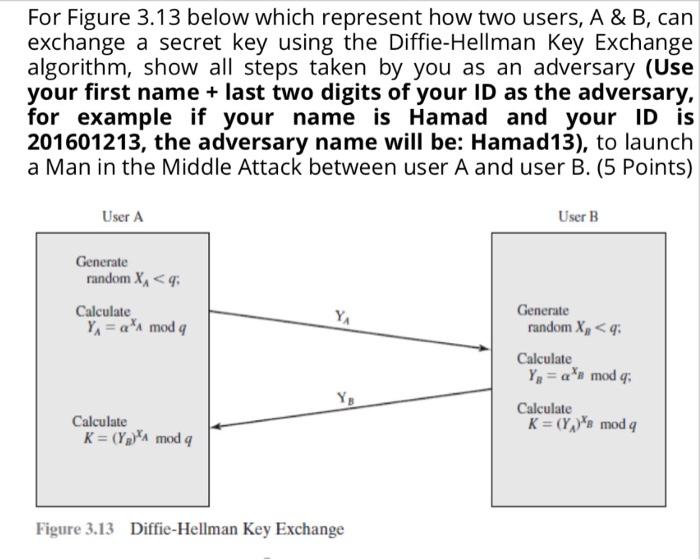
For Figure 3.13 below which represent how two users, A & B, can exchange a secret key using the Diffie-Hellman Key Exchange algorithm, show all steps taken by you as an adversary (Use your first name + last two digits of your ID as the adversary, for example if your name is Hamad and your ID is 201601213, the adversary name will be: Hamad13), to launch a Man in the Middle Attack between user A and user B. (5 Points) User A Generate random X < q: Calculate Y = a A mod q Calculate K= (Y)A mod q YA Figure 3.13 Diffie-Hellman Key Exchange User B Generate random X < q: Calculate Y = an mod q; Calculate K = (Y)s mod q
Step by Step Solution
★★★★★
3.41 Rating (148 Votes )
There are 3 Steps involved in it
Step: 1
Trudy13 breaks the aut...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


