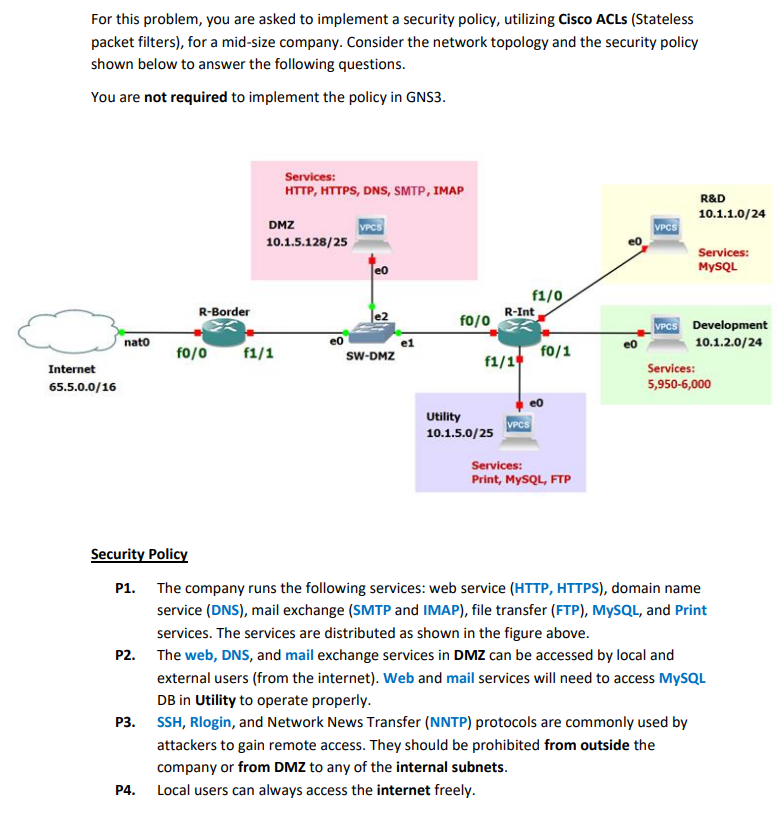
For this problem, you are asked to implement a security policy, utilizing Cisco ACLs (Stateless packet filters), for a mid-size company. Consider the network topology and the security policy shown below to answer the following questions. You are not required to implement the policy in GNS3. Services: HTTP, HTTPS, DNS, SMTP, IMAP DMZ VPCS 10.1.5.128/25 R&D 10.1.1.0/24 VPCS eo Services: MySQL f1/0 R-Int R-Border f0/0 eo f0/0 f1/1 SW-DMZ f0/1 nato Internet 65.5.0.0/16 f1/14 VPCS Development 10.1.2.0/24 Services: 5,950-6,000 Utility 10.1.5.0/25 VPCS Services: Print, MySQL, FTP Security Policy P1. The company runs the following services: web service (HTTP, HTTPS), domain name service (DNS), mail exchange (SMTP and IMAP), file transfer (FTP), MySQL, and Print services. The services are distributed as shown in the figure above. P2. The web, DNS, and mail exchange services in DMZ can be accessed by local and external users (from the internet). Web and mail services will need to access MySQL DB in Utility to operate properly. P3. SSH, Rlogin, and Network News Transfer (NNTP) protocols are commonly used by attackers to gain remote access. They should be prohibited from outside the company or from DMZ to any of the internal subnets. P4. Local users can always access the internet freely. P5. MySQL and FTP services in Utility can be accesses from local subnets, including the DMZ, but not from the internet. P6. The MySQL service in R&D is limited to the R&D use only (no one should be able to access it from outside R&D). P7. SSH connections to Utility, DMZ, and the Development subnets are permitted only from local subnets, except DMZ as indicated in P3. Questions a. What are the IP addresses and the wild card masks for the network subnets? Subnet IP Wildcard Mask Internet DMZ Utility R&D Development b. Define the access control lists (ACLs) required to enforce the security policy. Again, no implementation in GNS3 is required. I only need the ACLs. Make sure you clearly specify the router, interface, and the direction (similar to what we have done in the case-studies). You can use the following template. You are not required to use Cisco syntax, but feel free to do so. [interface-name@device) (In/Out] (sequence): (action), (protocol), [src ip : port], [dst ip: port] You can use the subnet name (e.g., DMZ, R&D, Dev, Utility, Internet) instead of the exact IP address/wildcard mask of subnets. Similarly, you can use the service name (HTTP, DNS, Rlogin, etc.) instead of the exact port number. For this problem, you are asked to implement a security policy, utilizing Cisco ACLs (Stateless packet filters), for a mid-size company. Consider the network topology and the security policy shown below to answer the following questions. You are not required to implement the policy in GNS3. Services: HTTP, HTTPS, DNS, SMTP, IMAP DMZ VPCS 10.1.5.128/25 R&D 10.1.1.0/24 VPCS eo Services: MySQL f1/0 R-Int R-Border f0/0 eo f0/0 f1/1 SW-DMZ f0/1 nato Internet 65.5.0.0/16 f1/14 VPCS Development 10.1.2.0/24 Services: 5,950-6,000 Utility 10.1.5.0/25 VPCS Services: Print, MySQL, FTP Security Policy P1. The company runs the following services: web service (HTTP, HTTPS), domain name service (DNS), mail exchange (SMTP and IMAP), file transfer (FTP), MySQL, and Print services. The services are distributed as shown in the figure above. P2. The web, DNS, and mail exchange services in DMZ can be accessed by local and external users (from the internet). Web and mail services will need to access MySQL DB in Utility to operate properly. P3. SSH, Rlogin, and Network News Transfer (NNTP) protocols are commonly used by attackers to gain remote access. They should be prohibited from outside the company or from DMZ to any of the internal subnets. P4. Local users can always access the internet freely. P5. MySQL and FTP services in Utility can be accesses from local subnets, including the DMZ, but not from the internet. P6. The MySQL service in R&D is limited to the R&D use only (no one should be able to access it from outside R&D). P7. SSH connections to Utility, DMZ, and the Development subnets are permitted only from local subnets, except DMZ as indicated in P3. Questions a. What are the IP addresses and the wild card masks for the network subnets? Subnet IP Wildcard Mask Internet DMZ Utility R&D Development b. Define the access control lists (ACLs) required to enforce the security policy. Again, no implementation in GNS3 is required. I only need the ACLs. Make sure you clearly specify the router, interface, and the direction (similar to what we have done in the case-studies). You can use the following template. You are not required to use Cisco syntax, but feel free to do so. [interface-name@device) (In/Out] (sequence): (action), (protocol), [src ip : port], [dst ip: port] You can use the subnet name (e.g., DMZ, R&D, Dev, Utility, Internet) instead of the exact IP address/wildcard mask of subnets. Similarly, you can use the service name (HTTP, DNS, Rlogin, etc.) instead of the exact port number








