Question
For this program, you will write a chunk based decryption program. Study the base code and make the following changes: Implement display_chunks(). Loop over each
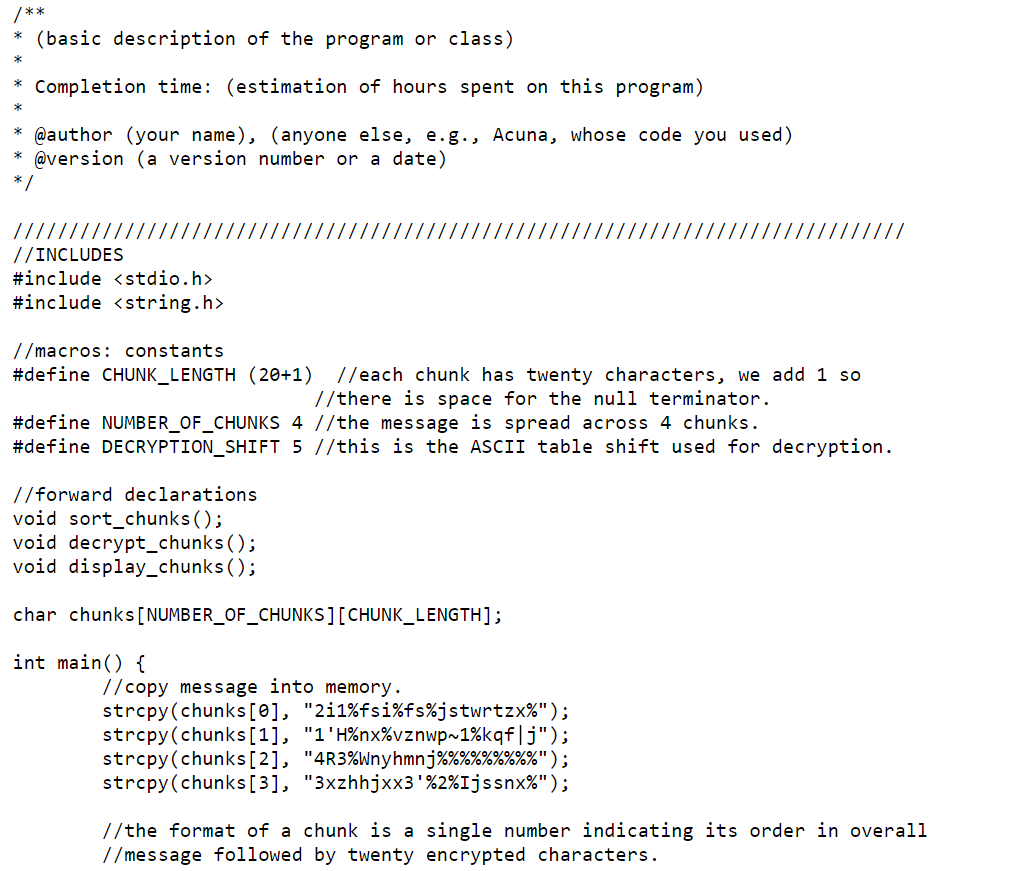
For this program, you will write a chunk based decryption program. Study the base code and make the following changes:
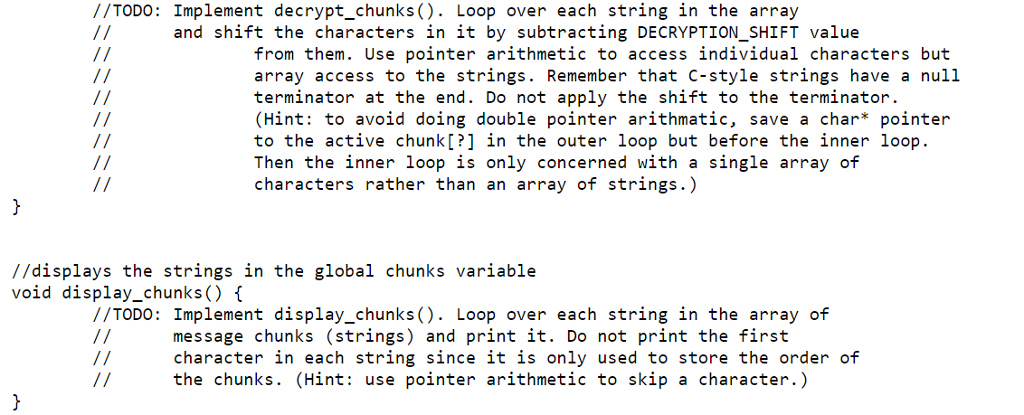
Implement display_chunks(). Loop over each string in the array of message chunks (strings) and print it. Do not print the first character in each string since it is only used to store the order of the chunks. (Hint: use pointer arithmetic to skip a character.) [2 points]
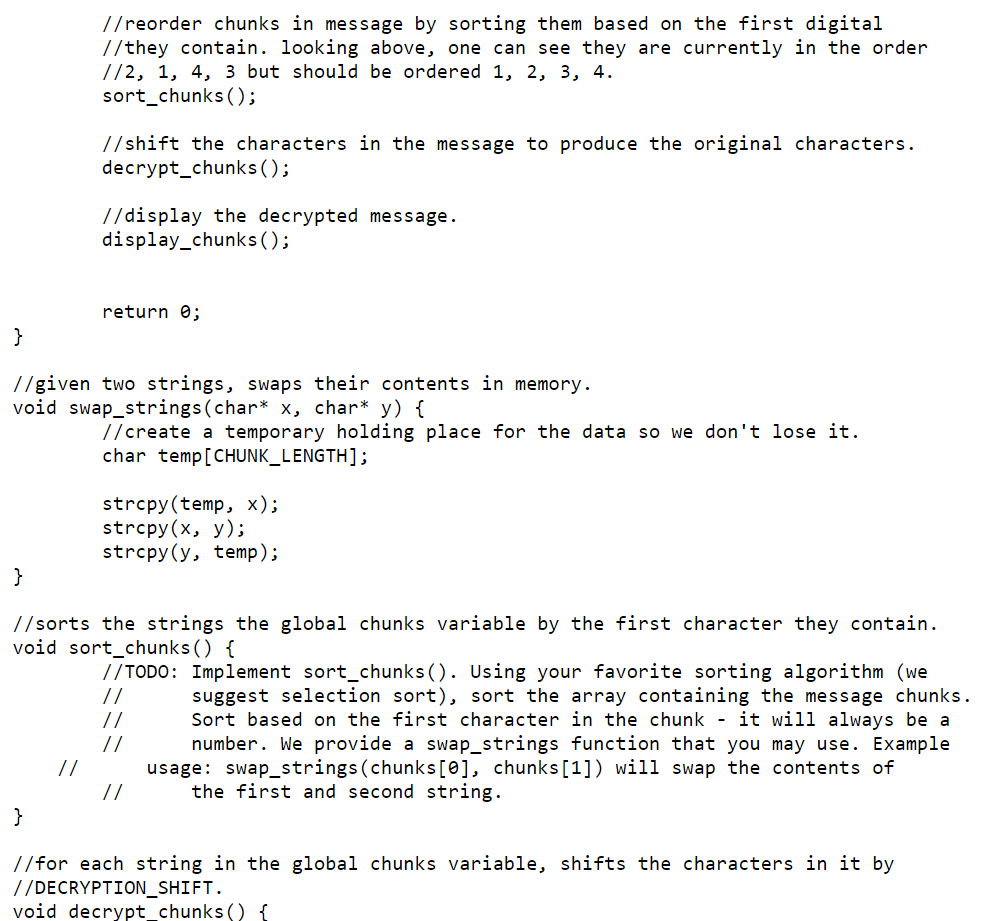
Implement decrypt_chunks(). Loop over each string in the array and shift the characters in it by subtracting DECRYPTION_SHIFT value from them. Use pointer arithmetic to access individual characters but array access to the strings. Remember that C-style strings have a null terminator at the end. Do not apply the shift to the terminator. (Hint: to avoid doing double pointer arithmetic, save a char* pointer to the active chunk[?] in the outer loop but before the inner loop. Then the inner loop is only concerned with a single array of characters rather than an array of strings.) [3 points]
Implement sort_chunks(). Using your favorite sorting algorithm, sort the array containing the message chunks. Sort based on the first character in the chunk - it will always be a number. We provide a swap_strings function that you may use. Example usage: swap_strings(chunks[0], chunks[1]) will swap the contents of the first and second string. [10 points]
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


